What is an account takeover?
An account takeover (ATO) is a cyber-attack in which cybercriminals use stolen credentials to gain unauthorized access to corporate systems. Criminals often obtain a user’s credentials for free on the dark web or Telegram, buying them in bulk, or through phishing attacks.
Once in control of the account, the attackers can exploit the compromised account for malicious purposes, such as stealing corporate data, withdrawing funds, or even using the company’s accounts to promote scams. Implementing a dedicated account takeover prevention strategy helps stop such incidents before attackers gain control of your systems.
The risks of account takeovers
Identity theft and data breaches
Stolen credentials can expose sensitive data and trigger costly breaches, putting your company’s privacy and compliance posture at risk.
Financial losses and fraud
Failing to invest in account takeover prevention early can result in significant financial losses from fraudulent transactions, ransomware, and regulatory fines.
Loss of customer trust
Frequent or large-scale account takeovers can erode customer trust, trigger negative press, and cause long-term harm to your reputation.
Compliance and legal issues
Account takeovers can result in non-compliance with standards like GDPR, SOC 2, PCI DSS, and ISO 27001, leading to fines and legal challenges.
How NordStellar account takeover prevention works
Scans for exposed accounts
NordStellar cross-references your accounts with recaptured data from Telegram, the deep web, and dark web sources.
Provides real-time breach alerts
When compromised credentials are found, your security team receives instant alerts, enabling rapid response.
Helps prevent the use of breached credentials
Upon receiving an alert, you can take immediate action, such as resetting passwords or suspending accounts.
Continuously monitors for new leaks
NordStellar provides ongoing scans to detect exposures early and maintain protection against takeover attempts.
Why use NordStellar to prevent account takeovers?
Using NordStellar to mitigate account takeover attacks offers benefits such as:
Protect sensitive business data
Prevent unauthorized access to your company’s and clients’ confidential information.
Preserve account privacy
Ensure strong security measures are in place to protect customer accounts and personal data.
Maintain business continuity
Minimize disruptions caused by compromised accounts to keep operations running smoothly.
Monitor executive accounts
Monitor accounts of key executives and VIPs to reduce the threat exposure of your most visible people.
Monitor supply chain ATO risks
Identify account takeover vulnerabilities related to your current and potential partners. This data allows you to make cyber risk data-informed decisions.
Trusted by leading teams across the globe
NordStellar’s account takeover prevention and threat exposure management platform is highly praised by both our clients and independent cybersecurity experts.
Explore more security solutions from NordStellar
NordStellar lets your cybersecurity team patch critical vulnerabilities and strengthen account takeover fraud prevention, intervening at the earliest stages of an attack–before any real damage is done.
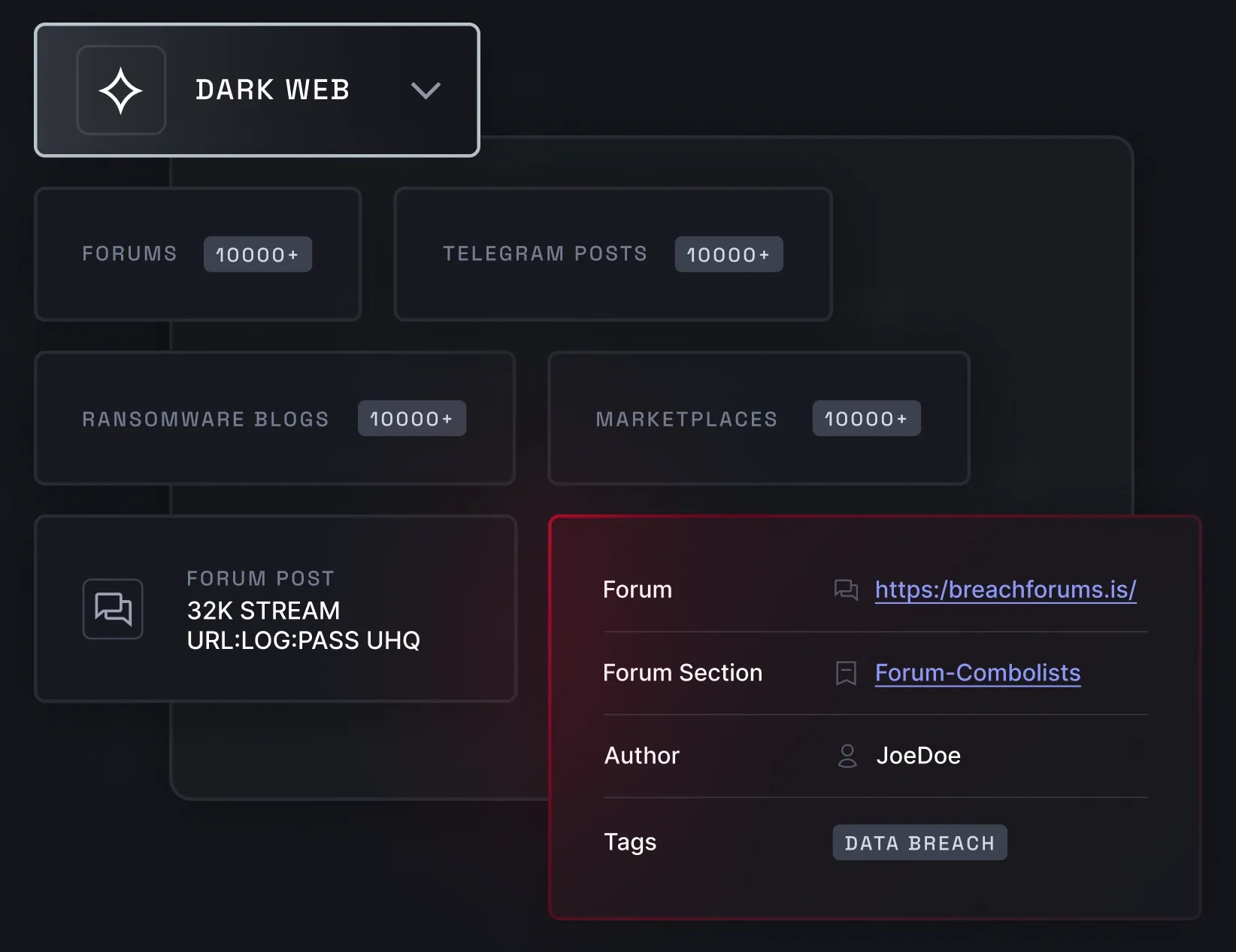
Dark web monitoring
Dark web monitoring allows you to track keywords associated with your business across deep and dark web communities, such as hacker forums, ransomware blogs, illicit marketplaces, and Telegram channels. It helps you uncover brand mentions, issues with vendors, and leaked information about your VIP personnel.
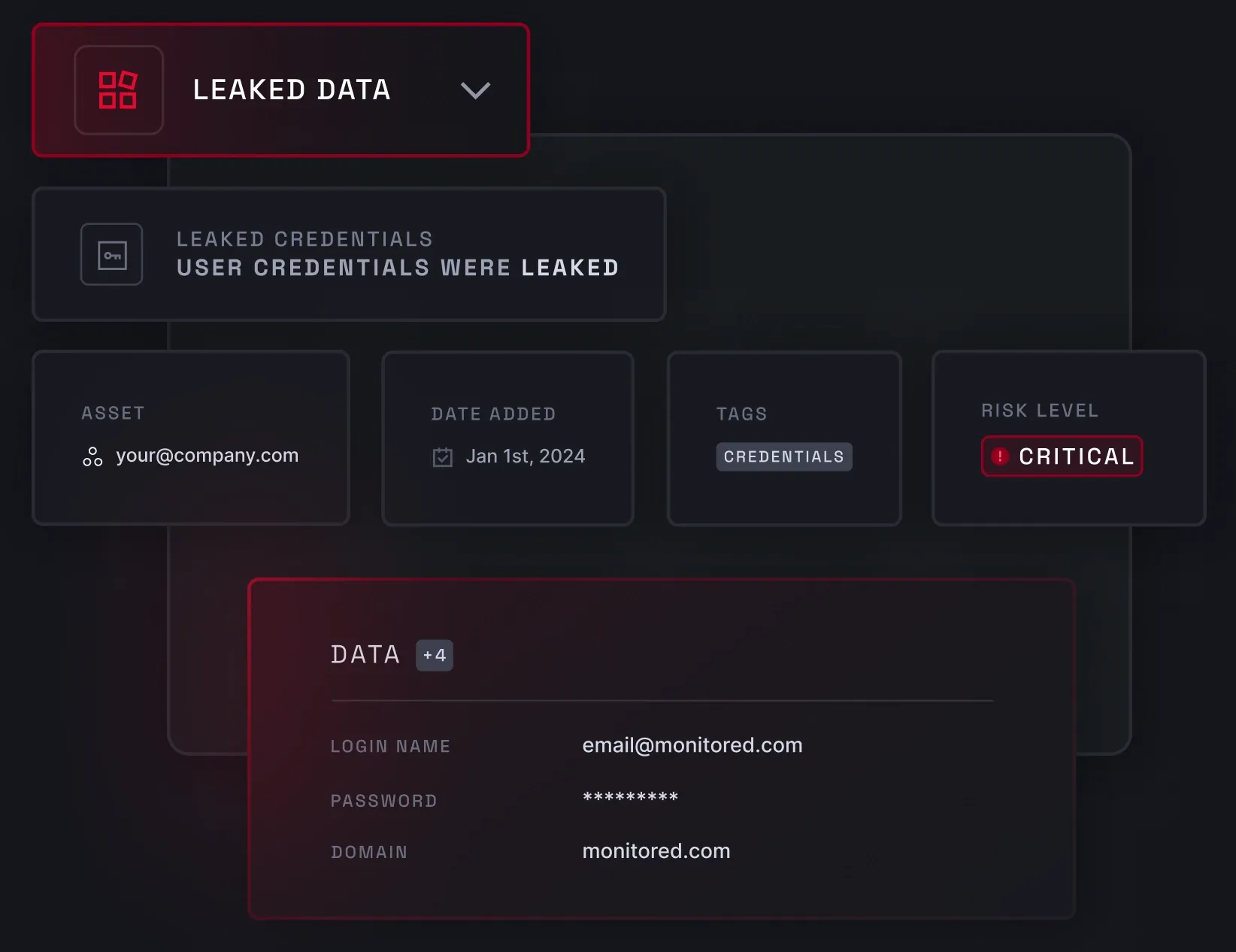
Data breach monitoring
Data breach monitoring scans the deep and dark web for leaked sensitive information linked to your business. To spot breached data, NordStellar checks infostealer malware logs, leaked databases, and lists of stolen credentials. Data breach monitoring is a crucial part of account takeover prevention, as it gives you real-time visibility into leaked credentials and the full context of past and present attacks.
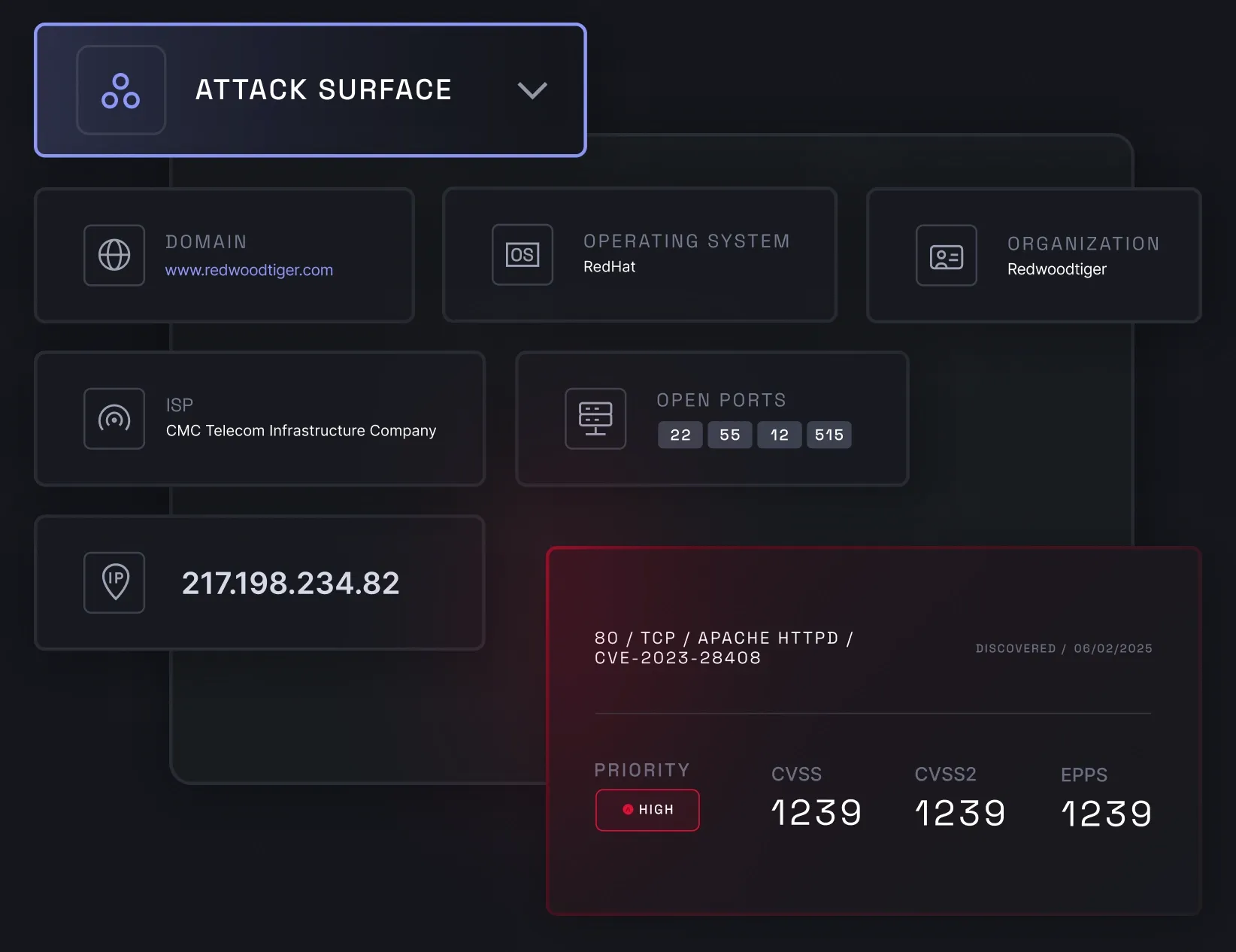
Attack surface management
Attack surface management (ASM) helps you monitor your business's external attack surface to prevent cyber risks. It enables you to manage your company's internet-facing assets efficiently, such as your IP addresses with open ports and outdated technologies, by identifying vulnerabilities and security gaps within them.
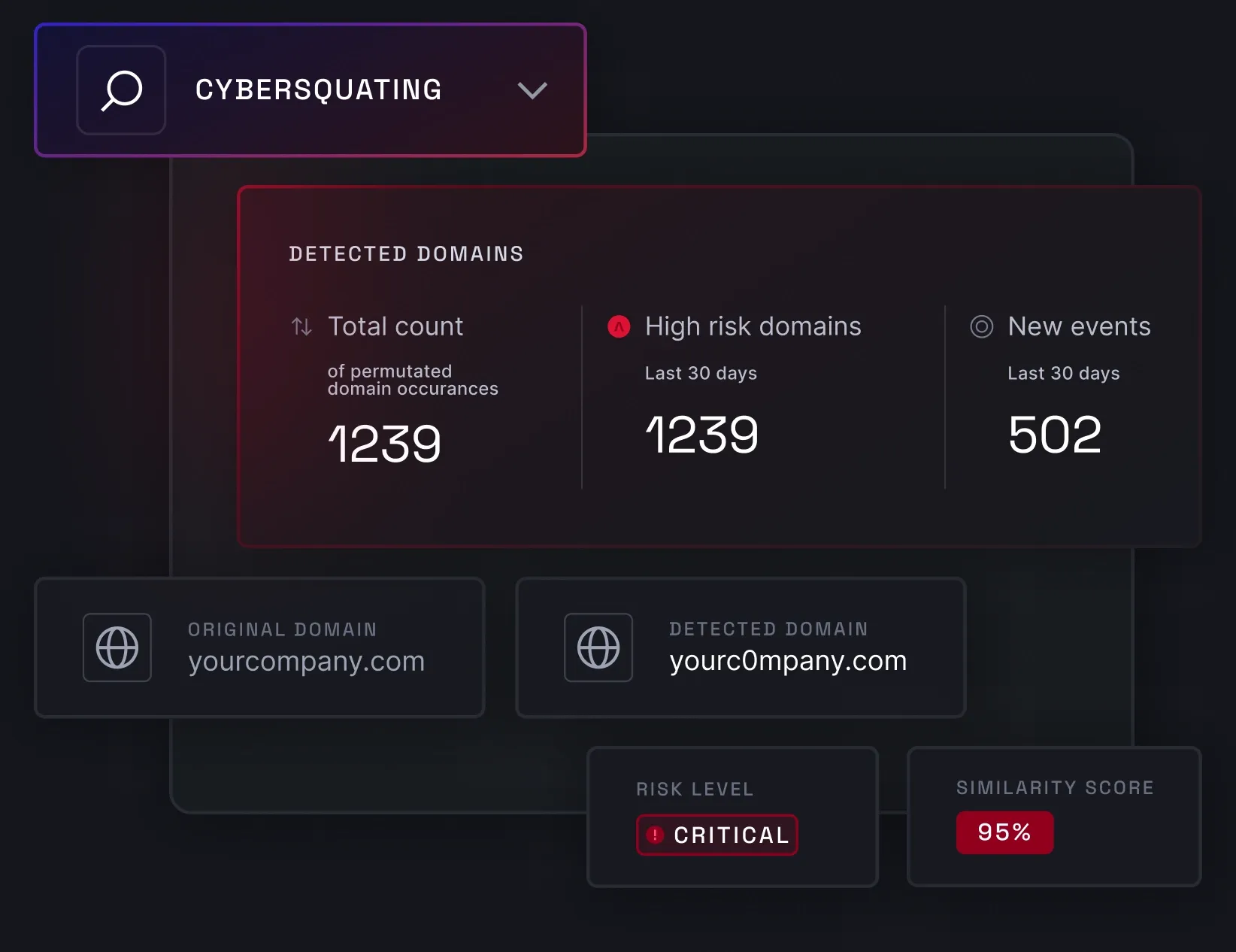
Cybersquatting detection
Cybersquatting detection helps you recognize and stop threat actors from impersonating your brand. Using content and visual similarity algorithms enriched with AI, NordStellar can detect domain manipulations and send real-time alerts with a detailed view of each suspicious domain.
FAQ
Yes, it is critical. An account takeover is one of the most dangerous attacks for a business. With complete control of your accounts, criminals can distribute malware, carry out phishing attacks, withdraw funds, and cause long-term damage.
First, monitor corporate accounts for any unusual changes or incidents that may signal unauthorized access. Second, educate employees to spot phishing and social engineering attempts. Third, enforce proper cyber hygiene: require strong, unique passwords, multi-factor authentication, and secure credential management. Finally, use an account takeover prevention solution, like NordStellar, to centralize monitoring, detect compromised accounts, and alert your security team in real time.
MFA (multi-factor authentication) is a great way to strengthen account security, but it’s not enough on its own. ATO attacks can result from various hacking techniques, such as session hijacking, which bypasses MFA. For example, hackers can take over your MFA device or intercept the security code. To prevent ATO, the best defense is to combine MFA with other security methods.
The biggest red flag is unexpected changes to account details. Hackers will usually try to change the account’s primary email, phone number, and recovery email, as well as make purchases from a new location. These signs are a major warning.
Most industries are at risk of account takeover attacks, but companies in retail, gaming, and healthcare, as well as financial and online services, are often targeted the most.
An account takeover attack can lead to serious financial consequences. Attackers may use compromised accounts to commit fraudulent transactions, steal funds, or access sensitive financial data. Beyond these direct losses, companies often face regulatory fines, legal fees, and the costs of remediation, such as incident response, system recovery, and customer compensation. Long-term effects, like reputational damage and customer churn, can further amplify the total financial impact of an account takeover.
If your organization’s accounts are found on the dark web, reset compromised passwords and enable strong authentication measures. You should also investigate how the credentials were leaked and monitor for suspicious activity across your accounts and networks. To prevent future incidents, enforce strict password policies, educate employees about phishing threats, and use a threat exposure management platform like Nordstellar for monitoring.
Account takeover prevention is about stopping attacks before they happen. This includes detecting exposed credentials, enforcing strong authentication, and monitoring for suspicious activity. Account takeover mitigation, on the other hand, is what you do after an account has been compromised. It comprises resetting passwords, suspending affected accounts, investigating the breach, and tightening security controls to prevent recurrence. In short, prevention keeps attackers out; mitigation limits the damage once they’re in.