Summary: Business email compromise (BEC) uses social engineering and hijacked accounts to trick employees into making fraudulent payments, requiring layered defenses to prevent losses.
Trust is one of the most valuable resources in modern business. However, business email compromise (BEC) attacks show that trust can also become a critical vulnerability, leading to devastating fraud and financial harm.
BEC attacks leverage trust by seizing control of legitimate email accounts and imitating their owners. This makes them hard to spot, but easy to execute with some social engineering skill and access to trusted accounts.
According to the FBI IC3, business email compromise costs exceeded $55 billion between 2013 and 2023, with over 158,000 US victims. In 2024, US businesses lost around $2.8 billion to email fraudsters. But here's the thing: many of those losses were, and are, avoidable.
This article will introduce business email compromises, including common types and attack techniques. We will explore stages in the BEC lifecycle before offering practical tips for handling and preventing email compromise incidents.
What is a business email compromise scam?
Business email compromise (BEC) attacks control legitimate business email accounts to request fraudulent transfers and access sensitive data.
BEC scams are a subset of phishing attacks, but they differ from familiar phishing techniques. Most importantly, BEC attacks target specific individuals with privileged access or executive authority and use social engineering methods to imitate the account holders.
Criminals manipulate employees by using hijacked accounts to build trust. Victims believe they are dealing with legitimate corporate accounts and behave accordingly. Entry-level and junior employees may also fail to challenge suspicious activity due to the seniority of compromised accounts.
Scammers use their trusted position to gain access to financial resources, confidential data, and critical systems. They exploit trust to execute wire fraud transactions or divert payroll to fraudulent accounts. Victims rarely detect fraud until it's too late. Even worse, ashamed victims may not report incidents promptly, having been deceived by social engineering attacks.
Generic phishing attacks are less targeted than BEC scams. Phishers aim to persuade email recipients to take risky actions, which trigger secondary techniques such as malware infection or credential theft. The targeted nature of BEC scams makes them far more dangerous, requiring specific security countermeasures.
Types of BEC scams and common tactics used by threat actors
Companies must mitigate risks related to BEC attacks, with no room for complacency. Mitigation begins with an awareness of what motivates attackers and how BEC scams operate. Knowing tactics, techniques, and procedures (TTPs) enables proactive measures against cyber attackers.
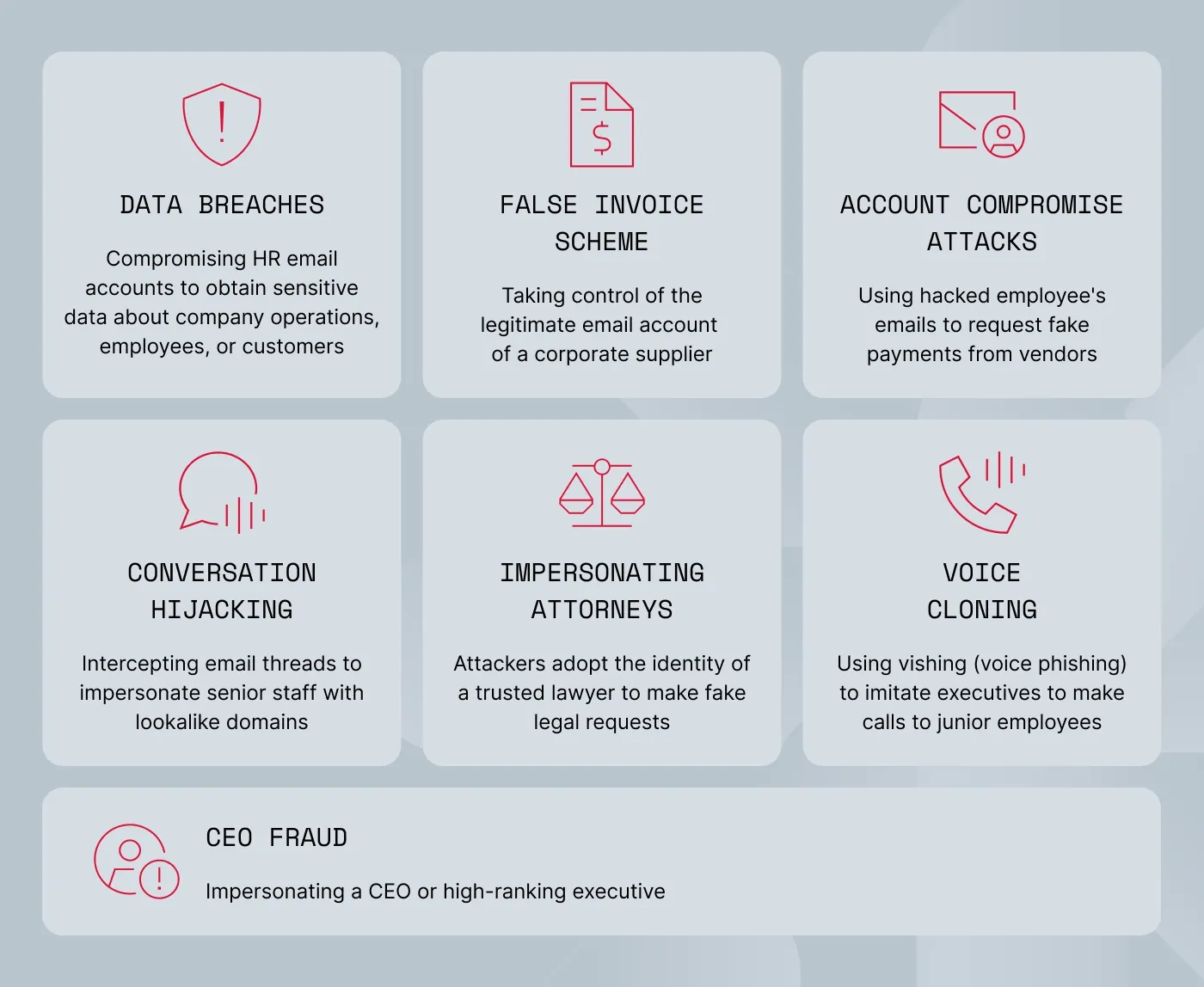
Types of BEC scams
The principles behind BEC attacks are simple: hijack accounts and use them to manipulate other email account holders. However, this type of account compromise attack takes several forms. Each type requires subtly different mitigation measures. Here are the main varieties:
CEO fraud
In this variety, attackers impersonate a CEO or high-ranking executive. Criminals may then email junior employees in the persona of the CEO to request financial transfers to a fraudulent bank account.
False invoice scheme
In this BEC fraud technique, attackers control the legitimate email account of a corporate supplier. They then email the vendor's clients and request funds via false invoice requests. Without proper verification processes, clients often accept requests from trusted vendors.
Account compromise attacks
Attackers execute an employee email account compromise and request payments from regular vendors (reversing the false invoice scheme). Requests often rely on months of research, tracking communication styles, timings, and transaction patterns. As with most BEC attacks, payments are sent to fraudulent bank accounts owned by the hackers.
Data breaches
Some BEC scams focus on obtaining sensitive data about company operations, employees, or customers. These attacks generally compromise HR email accounts, as human resources officers are well-placed to request information about individuals. For example, phishers may use BEC techniques against a CEO to execute data breaches before launching whaling attacks.
Impersonating attorneys
In the attorney impersonation technique, attackers adopt the identity of a trusted lawyer, whether they are employed internally or independently. The attorney contacts employees to make fake legal requests for sensitive information or financial transfers.
Voice cloning
This attack uses vishing (voice phishing) to imitate executives. Advanced AI tools enable realistic voice impersonation, allowing criminals to join group meetings or make strategic phone calls to junior employees. Voice cloning often combines with email communications to make attacks even more effective.
Conversation hijacking
This BEC attack type relies on surveillance. Attackers intercept email conversations and create email domains that closely resemble senior participants. Phishers choose a strategic moment to intervene via their fake account - generally a point of decision where participants are vulnerable to urgent action requests.
BEC attack techniques
The business email compromise variants listed above provide privileged access to data and financial systems. But how do attackers bypass phishing protection measures and fool employees into following their instructions?
Domain spoofing. Attackers use sender domains that resemble legitimate contacts, such as CEOs or trusted vendors. Display name deception also allows attackers to show the legitimate contact's name, making slightly inaccurate sender domains harder to spot.
Account takeovers. Criminals steal login credentials to compromise email accounts. Account compromises enable attackers to impersonate company officers accurately. They also position hackers to monitor communications and business activity.
Spear phishing. Criminals research individuals and use the findings to craft highly persuasive emails. Phishing emails enriched with specific business or personal data are often more compelling and harder to ignore.
Malicious forwarding and hidden email filters. Attackers use business email compromise tools to divert emails to independently controlled accounts. Hidden filters then delete the original emails or conceal them in sub-folders. This renders BEC attacks almost invisible without advanced email protection.
Malicious links. Threat actors create vendor websites that appear authentic but actually harvest visitor credentials. These sites are even more persuasive if victims reach them via spoofed emails from the vendor that contain malicious links.
Strategic timing. Timing is critically important in BEC attacks. Emails from criminals often coincide with strategic dates (such as the end of the financial year or before holidays). Phishers also try to identify moments of stress when employees are most likely to ignore warning signs. Busy periods or merger processes are often linked to email compromise scams.
How does a BEC attack work?
BEC attacks play out differently. But they tend to follow a standard lifecycle. Understanding how BEC attempts develop is important because it enables security teams to detect and correlate BEC attack identifiers before criminals succeed.
#1 Reconnaissance
Before sending any emails, attackers gather information about targets. Sources include social media feeds, website profiles, and leaked data available for sale on dark web forums or Telegraph channels.
This information sets up the business email compromise by generating a profile of the target. Attackers can craft social engineering attacks that accurately mimic their targets without arousing suspicion.
#2 Initial compromise
The second stage of BEC exploits involves gaining access to strategic email accounts.
Typically, compromises start with convincing phishing emails. Victims acquire malware by downloading malicious attachments or following links to fake websites, before unwittingly supplying login credentials. Attackers use these credentials to access the victim's mailbox.
#3 Establishing persistence
BEC schemes rarely move immediately from account compromises to final attacks. Attackers must establish a persistent presence.
Persistence enables criminals to monitor account activity and understand how to imitate the account holder. Long-term monitoring provides clues about how to bypass verification systems and which high-value contacts to exploit.
Attackers also use concealed forwarding systems and rules to hide malicious emails. This creates the conditions to start conversations with contacts or clients without the initial target's knowledge.
#4 Exploitation
The exploitation phase weaponizes access to the target's account. Attackers start sending fraudulent business emails and cultivating relationships with secondary victims. Through skilful use of social engineering techniques, attackers prime targets to supply sensitive information, enable access, or make risky transactions.
#5 Attack execution
Attackers use their trusted position to request funds or disclose sensitive data. For instance, criminals executing a vendor email compromise submit fraudulent invoices after preparing targets with regular questions. In the case of CEO fraud attacks, execution involves sending requests for wire transfers.
Execution is the final part of the attack. Contact with attackers tends to cease when they have achieved their desired results.
#6 Aftermath
A range of harmful consequences follows the execution phase of a business email compromise. Companies often discover accounting discrepancies months after the event during quarterly audits. Or they flag up invoices with regular vendors and receive denials that those invoices were ever submitted.
The actual money or sensitive information involved has long gone. Attackers quickly move funds via intermediary account holders or money mules. These intermediaries withdraw stolen funds, often transforming it into cryptocurrency or storing it in overseas accounts.
Meanwhile, attackers encrypt data and route it to secure servers across the world. In either situation, law enforcement agencies struggle to gather evidence and track down the offenders.
Related articles

Rūta TamošaitytėAug 28, 20258 min read

Aurelija EinorytėAug 9, 20258 min read
Signs your business is under a BEC attack
We know some examples of business email compromise and attack techniques. Now it's time to talk about prevention. Given the serious consequences for victims, business email compromise prevention should be a cybersecurity priority.
The first step in prevention is awareness. Understanding common signs of business email compromise attacks is critically important. Here are some red flags to help you spot BEC exploits early:
Unusual or urgent payment requests from executives. All payment requests should be verified before approval. However, applying greater scrutiny to requests from senior officers is a good starting point. Look for urgent language such as tight deadlines or dire warnings. They often indicate that cyberattackers are present.
Requests for secrecy or bypassing normal approval chains. BEC attackers want to remain concealed before executing transfers. However, large financial transfers should be transparent and subject to normal accounting processes, and requests to bypass these processes should always be challenged.
Slight spelling changes in domains or display names. As we have seen, BEC attackers use spoofed domains to impersonate legitimate colleagues or create fake websites. Staff should look for slight discrepancies. Even spotting a "0" instead of an "O" could block a multi-million dollar fraud.
Unexpected changes to supplier payment details. Employees should exercise similar vigilance when checking vendor details. Vendors tend to use standard invoice formats and notify clients about changes to payment accounts or terms. If invoices change between orders without explanation, verify the reason before making a payment.
Emails that look legitimate but fail SPF/DKIM/DMARC checks. SPF, DKIM, and DMARC verify that emails between trusted contacts are authentic. Enforce the use of authentication tools when making financial transfers and sending sensitive information. Log any failures, as they could indicate an ongoing BEC attack.
Unexpected emails about software or project updates. Attackers often send fake emails following legitimate project milestones or network overhauls. Treat any emails after updates have concluded as suspicious, especially if they request "further payments".
How to respond if a BEC attack happens
Some BEC attacks are unavoidable. Human nature is vulnerable to manipulation, and employees can easily drop their guard when dealing with invoices or transfer requests. If you detect a compromise attack, don't panic. Follow these step-by-step instructions to limit the damage.
Immediately alert IT and security teams. Employees should alert security teams, detailing the nature of the attack and the identity of suspicious contacts. The sooner you enlist security professionals, the better.
Contain compromised accounts and reset credentials. Security teams quarantine affected accounts and require a reset to a strong, unique password. Threat detection tools search for persistent malware and active email diversion tools.
Notify financial institutions to halt the transfer. Provide financial partners with exact information about malicious transfers and freeze the accounts. This should contain losses until the incident response concludes.
Report to law enforcement. As soon as possible, report the crime to national law enforcement bodies. For example, US companies should notify
the FBI IC3 (the Internet Complaint Center).
Preserve logs and email trails for investigation. A comprehensive evidence chain is essential. Use SIEM tools (if available) to gather relevant event logs and extract email trails from affected accounts. You need to know the scope of the attack, how it happened, the duration of the attack, and its likely consequences.
Take action to prevent future BEC incidents. Incident response plans should investigate the root cause of email compromise attacks and fix security vulnerabilities as needed. For example, you may need to extend email encryption or schedule further executive staff training.
Communicate transparently with stakeholders. Communication is critical. Start by notifying internal staff to be vigilant and change their email credentials. Check with vendors who may also be victims of the compromise attack, and work closely with your bank to retrieve funds or limit losses.
Preventive measures to protect against BEC
Adopting a layered defensive strategy is the best approach to phishing protection. Layering means combining technical controls, policies, and training to ensure comprehensive security. Here are some best practices to layer defenses and block business email compromise attacks:
Implement multi-factor authentication. Request unique one-time authentication factors when accessing all business email accounts. This blocks impostors at the login stage.
Use advanced email security gateways. These gateways use threat detection tools to identify and block phishing attempts and malicious payloads before they reach users.
Apply strict payment verification protocols. Use MFA for approvals and mandatory out-of-band confirmation for changes to payment processes. Double-check large payments with independent third parties.
Enforce regular security awareness training. Staff should understand how business email compromise attacks work and how to spot early warning signs. Discuss BEC examples with teams to fine-tune detection skills and put phishing in a real-world context.
Set up domain monitoring and DMARC enforcement. These tools monitor incoming emails to detect suspicious domains and sender identities. DMARC also authenticates emails between trusted parties, which should detect fraudulent requests.
Limit public exposure of executive contact information. Ensure executives know how risky it is to expose personal information. Try to limit the personal use of social media. Use
threat intelligence solutions like NordStellar to search dark web marketplaces for stolen data.
Business email compromise scams take many forms, from attorney impersonation to CEO fraud and fake vendor invoices. Every variety can have crippling financial consequences. As a result, companies must know how to prevent business email compromise attacks and leverage all available tools to achieve this goal.
Fortunately, NordStellar's enterprise cybersecurity solutions make it easy to implement effective layered defensive strategies.
Our platform gives you complete visibility into threats targeting your business. This allows for proactive defense, showing you what hackers might already know about your organization.
Our solutions include:
Dark web monitoring tracks down keywords related to your business, mentions of your company, and leaked information about your VIP personnel. Security teams can detect attacks at the planning stage and take appropriate action.
Data breach monitoring to detect leaked company credentials, such as user passwords and email addresses. Users can take proactive steps to block account takeovers and secure critical data.
Take action to prevent business email compromise attacks. Contact NordStellar today and explore ways to secure employee email accounts against targeted phishing techniques.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she loves explaining complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.