Summary: Think dark web forums don’t affect your business? Think again. Learn how they work, why they’re risky, and how to protect your data.
The dark web has a reputation for being a dangerous corner of the internet, and for good reason. While a small part of the dark web is used for privacy and free speech, most dark web forums are where cybercriminals trade stolen data and discuss attack strategies.
For businesses, this isn’t a distant risk; it’s a live threat. In 2020 alone, over 15 billion stolen credentials were circulating on the dark web, more than 5 billion of which were unique. By 2022, that number jumped by 82%.
If your business data gets leaked, there's a good chance it will end up in one of these forums. In this article, we'll break down how dark web forums work and how you can protect your organization before it shows on hackers’ radar.
What is a dark web forum?
Dark web forums work like regular online discussion platforms, but they live in the hidden part of the internet. You can’t just Google them. You can access these sites through dark web search engines. You also need specialized software like Tor (The Onion Router), which hides your location and IP address.
That built-in anonymity makes dark web forums a breeding ground for illegal activity. They are notorious for selling leaked data, hacking tools, illicit services, and drug sales. Some even offer step-by-step guides for launching cyber-attacks.
However, not every dark web forum is illegal. Some serve as open spaces for free speech, especially in countries with strict censorship. But these are rare. Most forums are tied to cybercrime, and many are active marketplaces for leaked business data.
The risk is real for companies. If your business suffers a data breach or hackers uncover vulnerabilities in your systems, your data may end up in one of these forums: exposed, traded, or used in future attacks.
How do dark web forums work, and how can you access them?
Dark web forums run on highly encrypted, anonymous networks. The most popular software for accessing the dark web is the Tor network. Tor, in short, the Onion Router, works by wrapping a user's internet traffic in multiple layers of encryption, like the layers of an onion. The result is a network where tracking a user’s location or activity becomes exceptionally difficult. Predictably, this anonymity has turned Tor into a magnet for cybercriminals. Websites and services exclusive to the Tor network typically have addresses ending in “.onion.”
Some forums are easy to access if you have the link. But the more dangerous ones—the ones criminals really care about—have strict entry rules. Many charge a fee (usually in cryptocurrency) to keep out casual visitors.
To join, new users might need an invite from someone inside or prove their worth by sharing something valuable, like compromised data or hacking tools. These forums also use ranking systems, where members earn reputation points by posting useful content or making successful deals. Some even sell higher ranks for faster access.
Inside, they work like regular online communities. People post, reply, and build status, but instead of talking about hobbies or tech, they trade hacking tips, leaked data, and ransomware services. If it’s illegal and digital, there’s probably a forum for it.
These places aren’t harmless hacker hangouts. They’re hubs for fraud, extortion, and identity theft. Even just visiting can be risky. Many sites track your activity or try to infect you with malware for spying, profit, or blackmail.
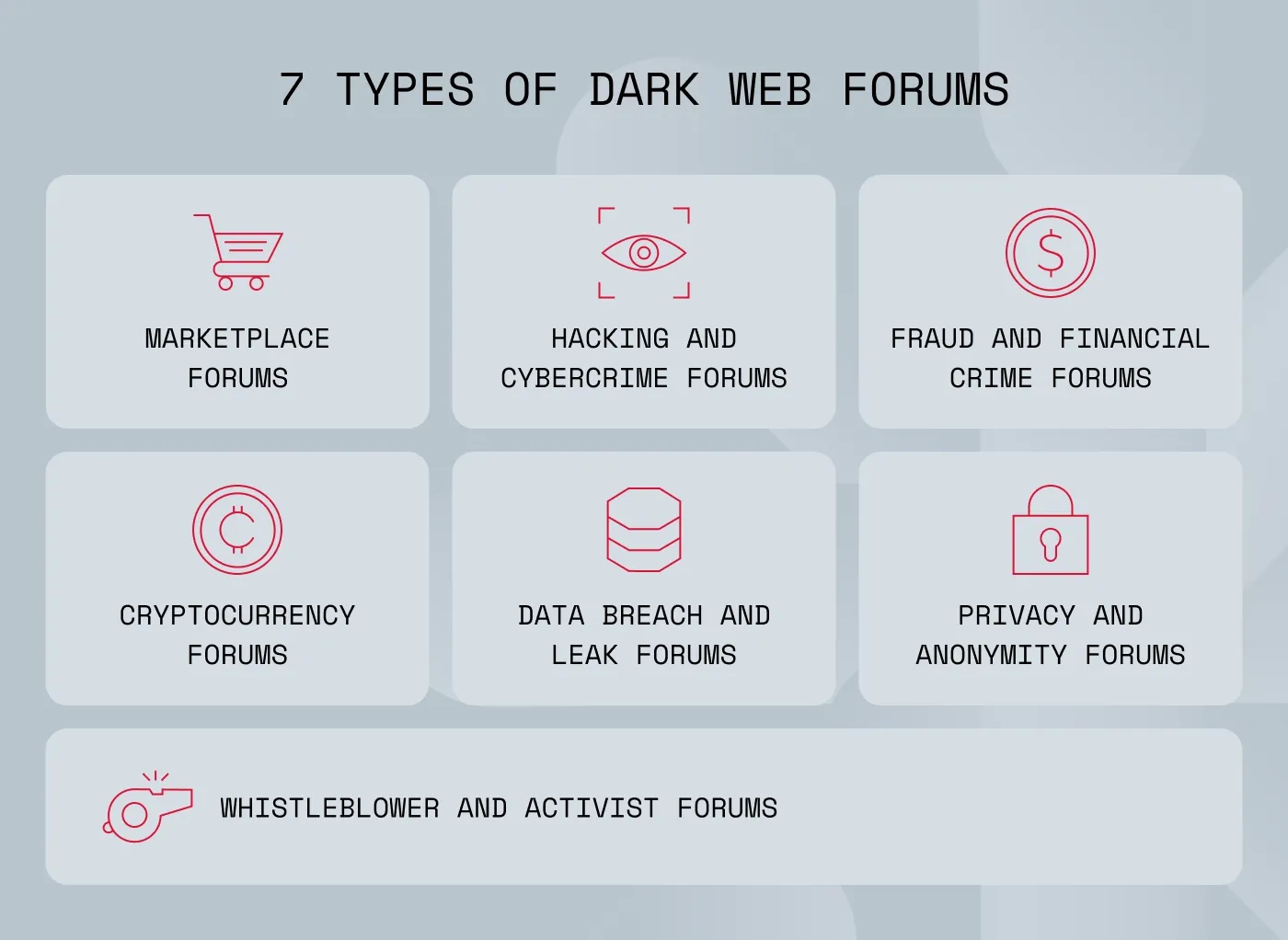
Common types of dark web forums
Not all dark websites are the same. Some focus on very specific types of crimes, while other forums cover a bit of everything, with multiple subforums dedicated to different crimes. A single forum can host discussions on hacking, fraud, data breaches, and more, making it a one-stop shop for cybercriminals.
Here's a closer look at the types of dark web forums, or subforums, that businesses should be aware of.
Marketplace forums
These forums attract the most attention because they provide criminals with access to valuable, illegal goods. Here's how these forums operate:
Main focus: Buying and selling illegal goods and services, like stolen login credentials, credit card data, and malware.
How it works: Transactions on marketplace forums often use escrow services to build “trust” between criminals. A forum administrator holds payments until both parties confirm the deal is complete.
Business risk: Stolen company data is frequently sold or leaked in these spaces. A single breach can quickly spiral into long-term damage through resale, fraud, or follow-up attacks.
Hacking and cybercrime forums
These hacking forums are dedicated to the “how-to” side of cybercrime. Let's take a look at how these forums work:
Main focus: Unauthorized access, digital sabotage, and sharing malicious tools and techniques
How it works: Hackers trade attack methods, share custom malware, and offer hacking services. Some forums also sell access to compromised systems, often gained through phishing or credential stuffing.
Business risk: Vulnerable companies are frequently discussed and targeted, especially those storing valuable or sensitive data.
A single exposed security flaw discussed in these forums can quickly lead to a full-scale breach.
Fraud and financial crime forums
Financial fraud is a popular topic on the dark web sites, with many forums dedicated to it. Here's what you have to know about them:
Main focus: Financial crimes like credit card fraud, fake invoices, payment exploits, and identity theft.
How it works: Criminals trade stolen financial data, identity kits ("fullz"), and combo lists of usernames and passwords. These resources fuel scams and impersonation tactics.
Business risk: Financial institutions and e-commerce platforms are frequent targets. Criminals constantly find new ways to bypass banking security, clone credit cards, or exploit payment processors. Once company data is exposed, fraud attempts can surge, leading to financial losses, legal trouble, and brand damage.
Cryptocurrency forums
Cryptocurrency is the backbone of the dark web's financial infrastructure, so it shouldn't be a surprise that you can find many forums that discuss crypto scams:
Main focus: Cryptocurrency-related activity.
How it works: Criminals share techniques to launder crypto, avoid blockchain tracking, and offer "cleaning services" for a cut of illicit funds.
Business risk: Even non-crypto companies can be impacted by fraudulent purchases, money laundering, and misuse of business accounts, which can lead to chargebacks, revenue loss, or legal exposure.
Data breach and leak forums
Data leak and breach forums often intersect with hacking forums, though many are specifically focused on methods for stealing, leaking, and exploiting data from corporate breaches. These forums function as follows:
Main focus: Sharing and selling data from corporate breaches.
How it works: Hackers analyze leaked data, negotiate prices, and sometimes leak samples to prove legitimacy or pressure companies during ransom demands. Breach data is posted for sale or free download.
Business risk: After a breach, compromised data often surfaces in these forums within hours, increasing the risk of further attacks, reputational harm, and legal consequences.
Privacy and anonymity forums
Not all dark websites are criminal in nature. Some are more neutral zones that focus entirely on teaching users how to preserve privacy or protect themselves from surveillance:
Main focus: Privacy tools, encryption, and anonymous communication.
How it works: Users exchange guides on Tor, VPNs, encrypted messaging apps, and other privacy-enhancing technologies.
Business risk: While some users are privacy advocates, the same tools are often used by threat actors, making these communities a potential source of risk and misuse.
Whistleblower and activist forums
The dark web can also be a secure place where whistleblowers and activists share information without fear of exposure. Here's what you should know about these forums:
Main focus: Secure spaces for whistleblowers, journalists, and activists to share sensitive information.
How it works: These platforms support anonymous tips, expose misconduct, and enable encrypted communication between sources and reporters. Activists also use them to coordinate safely in restrictive environments.
Business risk: Although often used for public interest, these forums can pose risks, like disgruntled insiders leaking company information, which can lead to reputational and security fallout.
Of course, many other underground forums focus on criminal activity like drug trafficking, illegal goods, and even more severe offenses such as human exploitation and smuggling. However, the forums outlined above are the most relevant for businesses, as they’re where threat actors target and exploit sensitive data and corporate infrastructure.
Related articles

Aurelija EinorytėJan 19, 20257 min read

Joanna KrysińskaJan 14, 20259 min read
Who uses dark web forums?
Underground forums attract all kinds of participants, each with different motives. Some seek privacy, others chase profits, and some are just curious. Here's a breakdown of the most common types of people active in these hidden communities:
Professional threat actors monetising from compromised data, fraud, and exploitation
Hobbyist hackers testing their tools and skills in semi-anonymous environments
Privacy advocates and free speech seekers communicating beyond surveillance
Whistleblowers and activists who want to share information safely
Investigative journalists exploring the darker corners of cybercrime
Security researchers gathering threat intelligence from high-risk forums
Buyers and sellers of illicit goods, including stolen credentials, counterfeit documents, weapons, and narcotics
Tech enthusiasts and gamers in search of obscure software, game mods, or underground discussion
Censorship escapees and curious users looking for restricted or banned content
While some forums serve specific linguistic or regional communities, such as Russian-language boards, most operate in English and cater to a global audience.
Is it illegal to visit a dark web forum?
In most jurisdictions, simply accessing a dark web forum isn’t illegal. The line is crossed when a user participates in criminal activity, such as trading stolen data, distributing malware, or purchasing illicit goods. Law enforcement agencies routinely monitor and infiltrate these spaces to identify and apprehend offenders.
Can police track users on anonymous networks? Despite tools like Tor offering strong privacy, security mistakes and vulnerabilities in these forums can still lead to arrests. Law enforcement takedowns of platforms like Alphabay and the Russian Anonymous Marketplace show that no hidden forum is above the law.
Risks associated with dark web forums
These cybercriminal communities are behind some of the biggest cyberattacks in recent years, fueling data breaches, phishing scams, ransomware, and fraud. These threats pose enormous risks for businesses.
Data leaks and stolen credentials
When networks are breached, stolen data is quickly sold on underground forums, often resold multiple times. For example, the Neopets breach exposed millions of user records, allowing attackers to infiltrate systems.
Organizations across every sector can face the same outcome. If employee credentials are exposed, attackers can exploit them to infiltrate your systems and escalate privileges.
Phishing
Phishing remains one of the oldest hacker tactics, but dark web forums have turned it into a sophisticated, scalable business. Criminals exchange ready-made phishing kits, including fake websites, email templates, and scripts to bypass security measures like two-factor authentication.
For example, a phishing kit targeting Chase Bank customers led to a 300% increase in phishing attacks, draining accounts and damaging the brand.
Ransomware and malware sales
Ransomware as a service (RaaS) is sold on hacker forums, allowing “affiliates” to launch business attacks. Malware, including keyloggers and infostealers, is also widely traded, making it easier for low-skilled attackers to execute sophisticated campaigns.
This booming underground economy emphasizes the need for robust attack surface and vulnerability management. Without these safeguards, weaknesses can go unnoticed until they’re exploited.
Financial fraud and dark web marketplaces
Underground forums are not only platforms for cybercrime but also major hubs for financial fraud. Criminals buy and sell stolen credit card details, bank logins, and payment processor accounts, fueling large-scale fraud.
How to tell if your company’s data is already on the dark web
Not every data breach is immediately visible. In many cases, signs of exposure appear quietly until attackers make their move.
Here are key indicators that your company’s data may already be circulating on underground forums or illicit marketplaces:
Unusual login activity. Multiple failed login attempts, unexpected multi-factor prompts, or sudden account lockouts may indicate that attackers are testing stolen credentials.
Targeted phishing attempts. If employees receive phishing emails containing accurate internal details, the leaked data is most likely used to craft targeted attacks.
Spoofed company emails. Customers or partners reporting scam emails “from” your company could signal domain spoofing. This often follows a breach in which an attacker gains access to brand or contact information.
Alerts from security tools. Your SIEM, identity provider, or dark web monitoring tools might flag exposed credentials, leaked passwords, or suspicious activity linked to your assets.
Mentions on dark web forums. Security researchers or intel feeds may pick up chats about your company, especially if stolen credentials, internal documents, or vulnerabilities are being shared.
Abnormal account behavior. Off-hour logins, data downloads, or permission changes by privileged users can signal compromised accounts being exploited.
How cybersecurity teams monitor dark web activity
Cybersecurity teams don’t wait for a breach, but they monitor the dark web to spot threats before they hit a company. By combining automated tools with hands-on threat intelligence, they track leaked data, impersonation attempts, and early signs of attack in real time. Here's how professionals combine tools, automation, and human expertise to monitor the dark web effectively:
Using dark web monitoring tools
Automated tools scan thousands of hidden sources, including hacker forums, marketplaces, and Telegram channels, for keywords tied to your company. These tools track the following in real time:
Email addresses
Domain mentions
Phone numbers
Specific keywords
Real-time alerts for exposed data
When dark web monitoring scans the dark web for company mentions and exposed data, such as credentials or domain mentions, alert systems are triggered instantly. These alerts are prioritized by severity, helping security teams respond faster and focus on the most critical threats.
Planning for early detection and response
Dark web monitoring isn’t just about seeing what’s out there. It’s about preparing for what comes next. Security teams use this intelligence to build stronger incident response plans, rotate compromised credentials, update configurations, and inform leadership of potential risks.
This means cybersecurity teams can turn dark web threats into actionable insights and stop attacks before they happen.
How can businesses safeguard against dark web threats?
Dark web communities aren’t vanishing, they’re mutating. Designed to stay a step ahead of law enforcement and automated surveillance, these online communities continue to operate in the shadows, exchanging everything from breached credentials to exploit kits.
But organizations are not powerless. With a strategy rooted in early detection, decisive action, and operational discipline, they can blunt the impact of dark web threats. Here is what your business can do:
Strengthen your infrastructure. Neglected updates, exposed ports, and overextended access privileges all create points of entry. You can take a disciplined approach to patch management and access controls to reduce your attack surface and lower the chances of data leakage in the first place.
Educate employees about dark web cyber threats. Most data breaches still hinge on human error. Training employees to recognize phishing tactics, enforce password hygiene, and adopt multi-factor authentication doesn’t just improve compliance; it narrows the window of opportunity for threat actors.
Implement real-time threat response plans. Knowing your data is on the dark web is only helpful if you can respond quickly. Build incident response processes to handle everything from resetting compromised credentials to engaging law enforcement.
Run external vulnerability scans frequently. Detection without response is theater. Organizations must develop actionable playbooks that cover everything from credential resets to executive communication. Time is often the decisive variable in limiting reputational and financial damage.
Invest in dark web monitoring. Dark web monitoring lets you discover breaches faster, giving you a head start in containing the damage. With NordStellar, you can continuously scan the dark web for mentions of your company, employee credentials, product names, or even specific projects.
How does NordStellar help prevent threats from dark web forums?
NordStellar gives your security team visibility to protect your business. As a threat exposure management platform, it continuously monitors dark web forums, Telegram channels, and illegal marketplaces, alerting about risks that might otherwise go unnoticed.
NordStellar also scans external-facing infrastructure for vulnerabilities, flags brand impersonation attempts, and tracks threat actor activity that could lead to account takeovers or ransomware attacks.
By combining External vulnerability scanning, Data breach monitoring, and Account takeover prevention, you gain a security framework that helps close the gap between exposure and response.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she loves explaining complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.