Summary: Discover the threat intelligence lifecycle, its key stages, and how it helps organizations detect, prevent, and respond to modern cyber threats.
Cyber threats grow in both volume and sophistication. Yet, the latest IBM Cost of a Data Breach Report 2025 shows a 9% drop in the global average breach cost to $4.44 million, the first decline in five years. Faster breach identification and containment, powered by AI, automation, and smarter use of cyber threat intelligence, largely drove this improvement. This shift toward faster detection and containment stresses the need for a structured approach to managing cyber risks: the threat intelligence lifecycle.
More than just a technical process, the cyber threat intelligence lifecycle is a strategic framework that enables security teams to transform scattered data into practical insights. By following its stages one by one, organizations can identify potential threats earlier, respond more effectively, and make decisions that reinforce their overall security posture.
What is the threat intelligence lifecycle?
The threat intelligence lifecycle is the structured process that turns scattered pieces of security data into ready-to-use knowledge. Think of it as the backbone of a network security team: a repeatable framework that transforms raw indicators of compromise, logs, and other signals into guidance that helps form defense against risks.
Understanding this lifecycle is essential because, without a clear process, organizations can quickly become overwhelmed by the sheer volume of threat data. When applied consistently, the lifecycle provides the foundation for both proactive threat hunting and effective threat exposure management.
Bad actors improve their methods quickly, and without a clear intelligence cycle, you risk drowning in noise. By following a defined threat intelligence process, organizations can spot vulnerabilities, prioritize resources, and take action.
In short, the lifecycle gives shape and discipline to cyber threat intelligence efforts, ensuring that data doesn’t just pile up. Rather, it drives better security decisions.
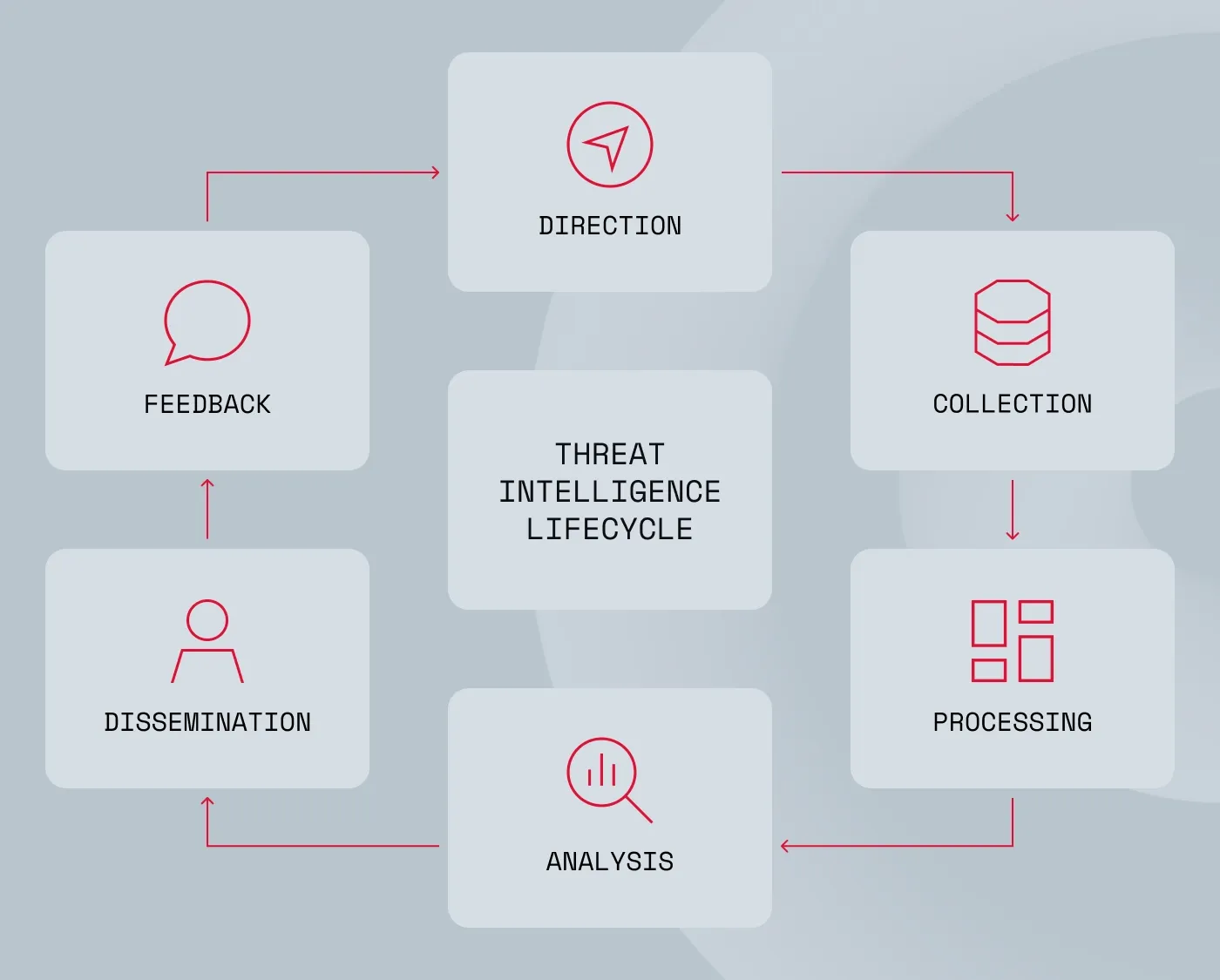
6 steps of the threat intelligence lifecycle
Each stage of the threat intelligence lifecycle plays a critical role in ensuring that security teams don’t just collect data, but turn it into insights that strengthen defenses.
Planning and direction: Setting intelligence goals
The first step is direction. Here, the questions arise: What do we need to know to protect the organization? Are we looking to support threat hunting, identify gaps in our security tools, or monitor for potential threats targeting our industry?
Clear objectives are crucial because they set expectations for what this lifecycle should deliver and create measurable key performance indicators (KPIs). Without them, even the best analysts risk collecting mountains of data that never turn into useful insights.
Collection: Gathering relevant threat data
Once goals are set, the collection phase begins. This is where the team gathers collected data from multiple sources:
Open source intelligence (OSINT)
Paid feeds and commercial providers
Dark web sources and underground forums
Logs and telemetry from internal security tools
The challenge here isn’t just data collection, but ensuring the right balance of internal and external sources. For example, if you rely only on commercial feeds, you may miss tailored attacks specific to your attack surface. If you focus only on internal logs, you won’t see the bigger picture of emerging threats in your sector.
A comprehensive collection also ensures that threat exposure across the organization is mapped and understood, making future defenses more precise. This stage lays the foundation for detecting security threats before they become incidents.
Processing: Cleaning and organizing raw data
The raw data collected in the previous stage is rarely usable as-is. That’s why the processing step matters: normalizing formats, removing duplicates, and enriching data with context.
This ensures that cyber threat intelligence tools and analysts aren’t overwhelmed by information. Well-processed data also improves the accuracy of later stages and reduces false positives, saving security teams from wasted hours chasing irrelevant signals.
Think of it as cleaning and tagging thousands of puzzle pieces before you even try to put them together. Only once data is well-organized and enriched with context can analysts extract meaningful intelligence to guide defenses.
Analysis: Turning data into threat intelligence
Here’s where the magic happens. Analysts transform processed data into tactical intelligence (short-term threat indicators), operational insights (attacker tactics, techniques, and procedures), and strategic context (who the threat actors are and why they’re targeting you).
By analyzing patterns across your threat surface, internal telemetry, and external feeds, the threat intelligence team can generate cyber threat reports that help leadership and operations teams make strategic decisions.
At this point, analysis not only identifies active risks but also helps shape enterprise cybersecurity policies by connecting intelligence with broader business priorities. This is where actionable intelligence emerges, by offering insights that lead to defensive actions like patching systems, adjusting security solutions, or updating detection rules.
Dissemination: Delivering intelligence to the right people
However, good intelligence is useless if it doesn’t reach the right stakeholders. Dissemination is the stage where findings are packaged and shared with executives, SOC analysts, and other decision-makers.
The format matters: threat analysis reports for executives, dashboards for SOC teams, alerts for incident responders. Dissemination often relies on threat intelligence platforms to ensure insights reach relevant workflows where they can drive real security efforts.
When the right person gets the right intelligence at the right time, it can mean the difference between shutting down an attack early and suffering a major breach.
Feedback: Refining the process based on input
The intelligence cycle is a continuous process, not a one-time event. Feedback closes the loop: Was the intelligence timely? Did it help reduce security threats? Did the team gain insights that improved defenses?
By gathering feedback from stakeholders, organizations can refine the threat intelligence lifecycle stages, improve KPIs, and ensure that future intelligence is even more targeted and effective. Without this step, intelligence risks becoming outdated—or worse, irrelevant. Together, these six stages create a repeatable cycle that sharpens visibility, reduces noise, and lays the foundation for realizing the full benefits of the threat intelligence lifecycle.
By continuously refining the lifecycle, organizations not only improve security operations but also realize measurable business benefits. As the threat landscape evolves, maintaining this cycle ensures security teams can adapt quickly to new tactics and exposures.
Benefits of the threat intelligence lifecycle framework
Following the cyber threat intelligence cycle isn’t just an academic exercise—it has a direct business impact. By structuring your security activities around the lifecycle, your organization gains clarity, precision, and efficiency.
Here are some of the biggest benefits:
Reducing false positives and wasted resources. A disciplined threat intelligence process ensures that only relevant signals are escalated. That means fewer alerts for SOC teams to chase, and more time spent countering real cyber risks.
Supporting proactive risk management. By integrating intelligence into daily security operations, organizations can identify risks before they occur. This reduces the chances of data breaches and gives defenders a chance to act before attackers succeed.
Enabling smarter budgeting and prioritization. When executives get clear threat reports and actionable insights, they can make better calls on where to invest in security tools, training, or monitoring. Instead of reacting to crises, they allocate resources based on evidence.
Ultimately, the threat intelligence lifecycle (NIST and similar frameworks) ensures organizations can move from reactive firefighting to proactive defense. It transforms scattered data into a business advantage: reducing noise, sharpening response, and extending the value of every security dollar spent.
Why now is the time to strengthen your intelligence lifecycle
The reality is that the threat landscape will never slow down. New threat actors are constantly experimenting, and your exposure surface is expanding with every SaaS integration, cloud service, and remote endpoint. The organizations that succeed are the ones that view intelligence as an ongoing process, not a one-time event.
If your team is still struggling with scattered feeds, disconnected security tools, and outdated threat intelligence reports, you’re not getting the full picture, and attackers know it. By integrating threat intelligence properly, you give your SOC and leadership the ability to see around corners, anticipate potential threats, and make the right decisions before damage is done.
The six cyber threat intelligence lifecycle steps give you the playbook. The next one is putting it into practice with technology and expertise that can scale.
Solutions like NordStellar help operationalize the threat intelligence lifecycle. The platform delivers real-time visibility into cyber risks through data breach monitoring, dark web monitoring, attack surface management, and cybersquatting detection—transforming intelligence into proactive defense.

Agnė Srėbaliūtė
Senior Creative Copywriter
Agne is a writer with over 15 years of experience in PR, SEO, and creative writing. With a love for playing with words and meanings, she crafts content that’s clear and distinctive. Agne balances her passion for language and tech with hiking adventures in nature—a space that recharges her.