Summary: Cyber-attacks often start in a place your security can’t see: the dark web. This guide shows you how to gain visibility and prevent breaches.
A data breach often starts with a single compromised password. An employee's credentials, stolen from an unrelated data breach, appear for sale on an illegal marketplace. Days later, an attacker might use it to log into your corporate network, bypassing the firewall as a 'legitimate' user.
Many breaches begin this way—not with a complex hack but with compromised data bought and sold on the dark web.
To protect your organization, you need visibility into these dark web-related threats. This guide explains what dark web monitoring is, how it works, and why it's now an essential layer of any effective security strategy.
What is dark web monitoring?
The dark web is a hidden network of websites that can't be reached with standard browsers. Unlike the surface web we use every day, it requires special browsers, like Tor, which mask a user's virtual location and IP address. This anonymity makes the dark web an appealing hub for cybercriminals to buy and sell compromised information.
Dark web monitoring is the process of scanning dark web forums and marketplaces, Telegram channels, and ransomware blogs for mentions of your company and stolen data, such as employee passwords, customer details, domain mentions, or specific keywords.
When the information linked to your business is found, you get a real-time alert. This provides an early warning to protect your business
How does dark web monitoring work?
Dark web monitoring continuously scans hidden corners of the internet for sensitive information related to your business. The process provides early alerts about your data exposure, allowing you to take action before that information can be used in an attack.
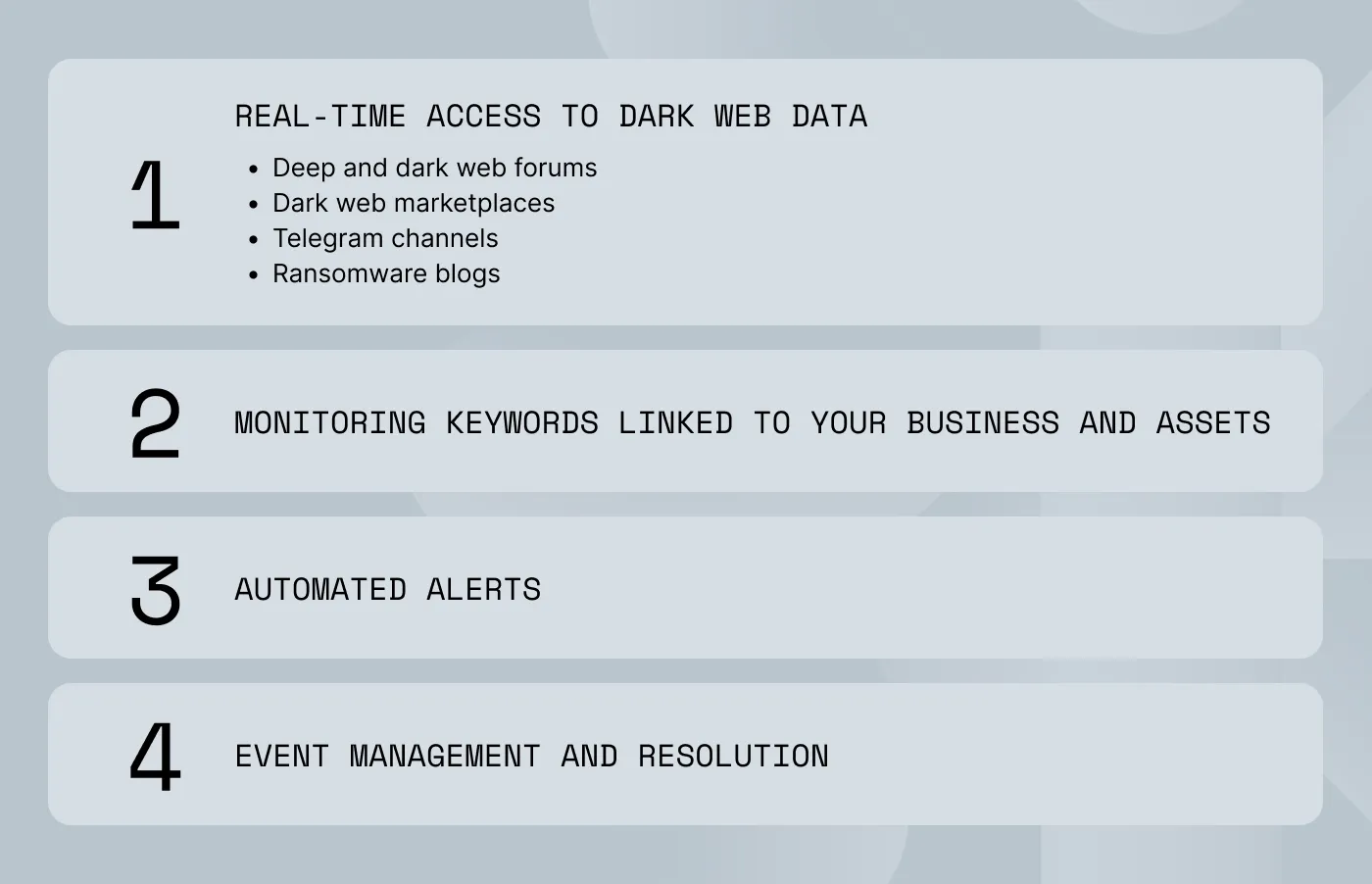
Here's a closer look at the key steps in how dark web monitoring works.
Real-time access to dark web data
The process begins with continuously scanning data from a wide range of illicit sources where stolen information is bought, sold, and shared. These sources include:
Deep and dark web forums: Hidden online communities where cybercriminals discuss tactics, trade exploits, and sell data.
Dark web marketplaces: Sites on the dark web designed specifically for selling illegal goods, including stolen credentials, company databases, and malware.
Telegram channels: Private and public chat groups used for coordinating fraud, phishing campaigns, and identity theft.
Ransomware blogs: Websites where ransomware gangs publish stolen data from victims who refuse to pay a ransom.
Monitoring keywords and assets
Once access is established, the monitoring platform actively searches these sources for keywords, phrases, and mentions of your company. This is like setting up a search alert for your most valuable information in places you can't normally see.
Automated alerts
When the monitoring system detects a match—whether it's a compromised employee email address or a mention of your company on a ransomware blog—you receive an immediate alert. These alerts provide context, including the source of the leak, allowing you to respond quickly to mitigate the threats.
Event management and resolution
The final step is managing the information you receive. Dark web monitoring allows you to review the source of the mention. After that, you can work on resolving the issue, for example, by forcing a password reset for a compromised account.
Dark web monitoring works like an alarm system—it can’t remove your data, but it gives you the early warning needed to act quickly. That’s why it should be part of a broader cybersecurity strategy that includes strong security practices, employee training, and a clear incident response plan.
What type of data is monitored on the dark web
Not all stolen data is valued equally, but every piece represents a potential risk. Cybercriminals look for information that can be monetized, used for extortion, or as a foothold for a larger attack. Understanding their target data is the first step in protecting your most valuable assets.
Here’s a more detailed look at the types of data that are monitored on the dark web:
Domains. Monitoring our company's domain names for compromised customer data from malware infections or combo lists.
Email addresses and phone numbers. Both corporate and personal email addresses or phone numbers can be monitored to detect data breaches, combo lists, and malware infections.
Keywords: Tracking specific names, terms, or text strings related to your company can signal a data breach. By using keywords, you can monitor, such as:
Brand mentions
Corporate and personal contact information
Client and partner information
Employee records
Is it legal to use dark web monitoring?
Using dark web monitoring solutions is legal. These services help organizations identify data leaks and prevent them from escalating into major security incidents.
However, if you're considering using a dark web monitoring service for your organization or personal use, reviewing the provider's privacy policy and terms of use is a good idea. Doing so will help you understand how they operate and protect your information. Ensure that your chosen service complies with all relevant laws and regulations.
What are the benefits of dark web monitoring for businesses?
Dark web monitoring provides many benefits for businesses. It helps them protect their sensitive information, maintain a good public image, and can even save them from financial loss:
It warns about potential threats. By continuously screening for exposed information, you can stay one step ahead of cybercriminals and address potential risks before they escalate into critical incidents. This proactive approach is essential in disrupting the early stages of the
cyber kill chain.
It protects the company's reputation. By quickly detecting and responding to data leaks, you can maintain trust with customers and partners, improve your brand's credibility, and maintain a good public image.
It protects the employee and client information. Continuous dark web surveillance ensures that any compromised employee or client information is flagged early. This way, you can prevent criminals from exploiting this stolen information.
It improves your cybersecurity strategy. By monitoring past vulnerabilities, your security team can gain more accurate insights into how criminals exploited them, leading to a better understanding of potential threats. Advanced
threat intelligence tools can automate this monitoring process, correlating threat indicators across your environment and providing contextual awareness about emerging attack vectors.
It saves costs. By identifying and addressing threats early, you can reduce the financial impact of legal fees, reputational damage, and recovery costs, ultimately saving your business money in the long run.
Related articles

Aurelija EinorytėJan 19, 20257 min read

Violeta LyskoitJan 10, 20259 min read
What are the limitations of dark web monitoring?
While dark web monitoring is a valuable tool for businesses, it does have its limitations:
It can't remove leaked information. A dark web monitoring tool can alert you about compromised data, but it can't remove that information once it's been posted on the dark net. The primary benefit of tracking information on the dark web is early detection, which allows you to take steps to minimize damage.
It won't stop cyber-attacks. Monitoring alone can't protect businesses from cyber-attacks, such as data breaches where sensitive information is leaked or stolen. It is a preventative measure that helps you identify compromised information before malicious actors can exploit it.
Despite these limitations, the benefits of these services alone make dark web monitoring worth the cost. By being aware of possible threats and acting quickly to address them, organizations can significantly reduce the risk of data breaches and improve their cybersecurity strategies.
How can your data get on the dark web?
Business and personal information can end up on the dark web through various means, often as a result of cybercriminal activity:
A data breach. When an organization experiences a
data breach, compromised credentials, and other sensitive data can be stolen and then shared on dark web forums and marketplaces to be sold.
Phishing attack. Malicious actors often use phishing tactics to trick individuals into providing personal information. They can later sell the data collected in a phishing attack to other criminals who may use it for identity theft, financial fraud, or launching further phishing schemes.
Hacking and malware. Malicious software can infiltrate systems to harvest personal and business information.
Insider threats. In some cases, employees with access to confidential information may intentionally or unintentionally leak it, which can then be sold on dark web platforms.
Anatomy of a response: What to do with an alert from dark web monitoring
When a dark web monitoring solution alerts you that your company’s data has been found on a hidden forum or marketplace, it’s time to act—fast. A swift, organized response can make the difference between a minor issue and a major crisis. Here are the five essential steps to take.
Step 1: Contain the immediate threat
Your first move is to cut off access. If an employee’s password was exposed, reset it immediately. If a digital key (like an API token) was leaked, disable it. This ensures criminals can't use the stolen information to get into your systems.
Step 2: Assemble your response team
Simultaneously, notify all relevant internal teams. This includes your IT security team to investigate, your legal team to advise on obligations, and your compliance team to ensure you follow all regulations. A coordinated response prevents mistakes and ensures all bases are covered.
Step 3: Assess the scope of the breach
Once the immediate threat is contained, your security team needs to determine the full scope of the exposure. They'll investigate exactly what data was lost, which systems might be affected, and if the attackers have already used the information. This assessment helps you understand the accurate scale of the problem.
Step 4: Manage external communications
Based on the investigation and legal advice, decide if you need to notify people outside your company. If their data was involved, you may be legally required to inform customers, partners, or government regulators. Honest and timely communication is key to maintaining trust.
Step 5: Document and improve
Throughout the process, keep a record of every step you take. This documentation is vital for later review and proves you handled the incident correctly. Use the lessons learned from the event to strengthen your security and update your response plan for the future.
What should you look for when choosing a dark web monitoring service?
When selecting a dark web monitoring service, you should consider several factors to ensure you choose a solution that meets your needs:
Wide coverage. Look for a service that scans various dark and deep web sources, including marketplaces, forums, and chat rooms, to maximize the chances of detecting compromised information.
Real-time monitoring and alerts. A good monitoring service should offer continuous monitoring and send alerts when it detects your information on the dark and deep web. This way, you can take immediate action.
Tailored solutions. Look for the ability to customize alerts based on your company's keywords or phrases for relevant, focused results.
Actionable alerts. Dark web alerts should provide clear steps to respond to detected threats.
Additional security features. It would be a great benefit if the company offered additional features to protect against various cyber threats.
NordStellar's dark web monitoring service encompasses all these essential features. It monitors thousands of cybercrime communities in real-time, informing you about threats targeting your company. This solution tracks explicitly keywords associated with your business across dark web forums, deep web search engines, illicit markets, hacking communities, and other sources.
By identifying a data leak related to your company early on, NordStellar helps prevent these issues from escalating into major security incidents. In addition to dark web monitoring, our services include data breach monitoring and account takeover prevention, which add an extra layer of protection for your organization.
FAQ
How can you know if your information is on the dark web?
The best and fastest way to determine if your information is on the dark net is to use dark web monitoring. These tools continuously scan various dark and deep websites and alert you if your personal or business information is detected. Using them allows you to take action quickly to mitigate any potential risks.
Is dark web monitoring safe?
Dark web monitoring is entirely safe. These tools seek information publicly available on the dark web to warn you about possible threats. Just be sure to choose a trusted provider that employs secure methods to handle your information and complies with industry regulations.
What are the features of dark web monitoring?
Dark web monitoring typically includes real-time alerts, regular scanning of dark web forums, marketplaces, and specialized dark web search engines, and the ability to search for specific information, such as email addresses or credit card information. Additionally, many services provide information about the threats found and how to protect yourself.
Are there free dark web monitoring services?
Yes, free dark web monitoring services are available, and they can be a good starting point for assessing your exposure. A free scanner, for instance, can quickly check if your credentials have been found in known data breaches circulating on the dark web.
However, the reliability of the provider is critical. When using a free tool, you should only choose a reputable service from a trusted cybersecurity provider. An unreliable service could mishandle your data, exposing you to the very risks you are trying to prevent.
Who should use dark web monitoring services?
Dark web monitoring can benefit everyone, but it is especially beneficial for businesses of all sizes. Companies most vulnerable to cyberattacks include financial institutions, healthcare providers, and e-commerce platforms. However, dark web monitoring can also help individuals who are worried about identity theft.
How can you prevent information exposure on the dark web?
Dark web monitoring alone can't fully protect your business from data exposure. To reduce the risk of a data breach, implement strong cybersecurity measures, such as using strong passwords, enabling two-factor authentication, and regularly updating all software. Utilize a password manager to help employees keep track of passwords to organizational accounts. Also, establish effective identity management practices to ensure that only necessary employees can access sensitive data. Educate employees about phishing attacks and safe online practices.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she loves explaining complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.