Powerful solutions for cybersecurity compliance
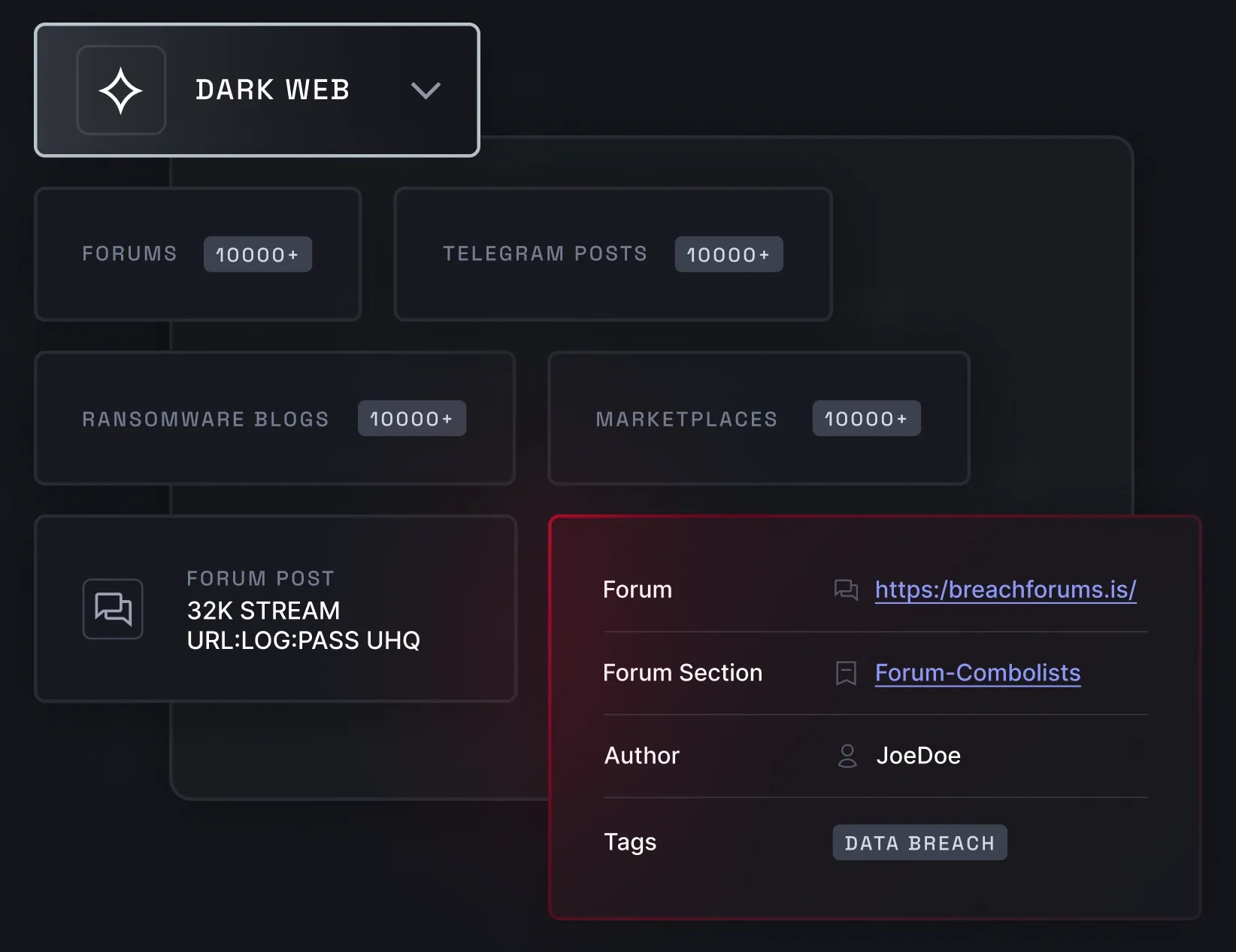
Dark web monitoring
With NordStellar’s dark web monitoring, you can detect leaked credentials and sensitive data from thousands of sources, such as the deep and dark web, cybercriminal forums, and Telegram channels. Dark web monitoring supports threat intelligence, incident detection, and response requirements in standards, such as NIS 2 and DORA.
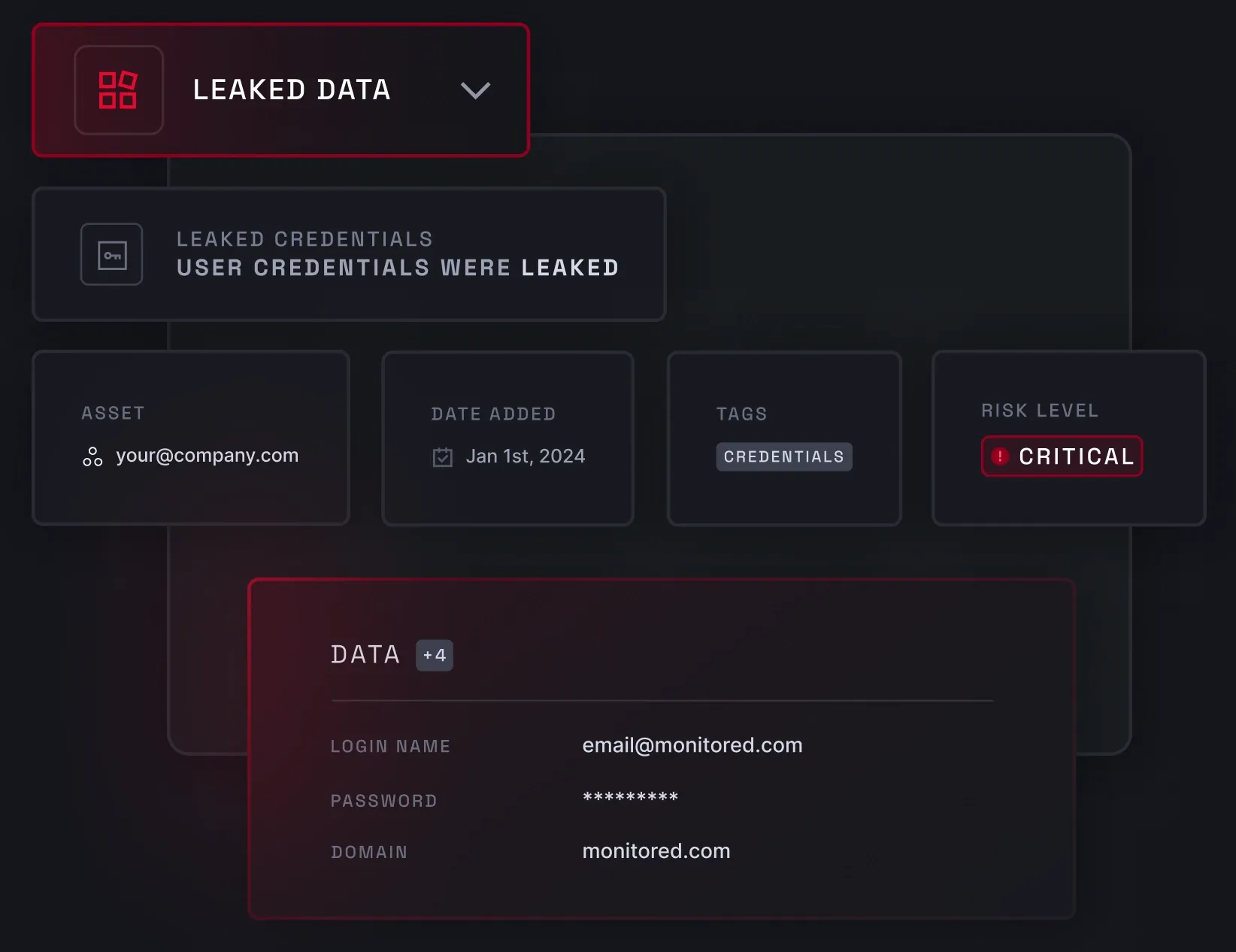
Data breach monitoring
Data breach monitoring enables you to detect breaches early, allowing your company to meet regulatory requirements for timely breach notification and containment. As a part of ISO 27002’s Section 5.7 threat intelligence control guidelines, it monitors for information security threats such as leaked employee and consumer credentials, malware logs, and exposed credit card information.
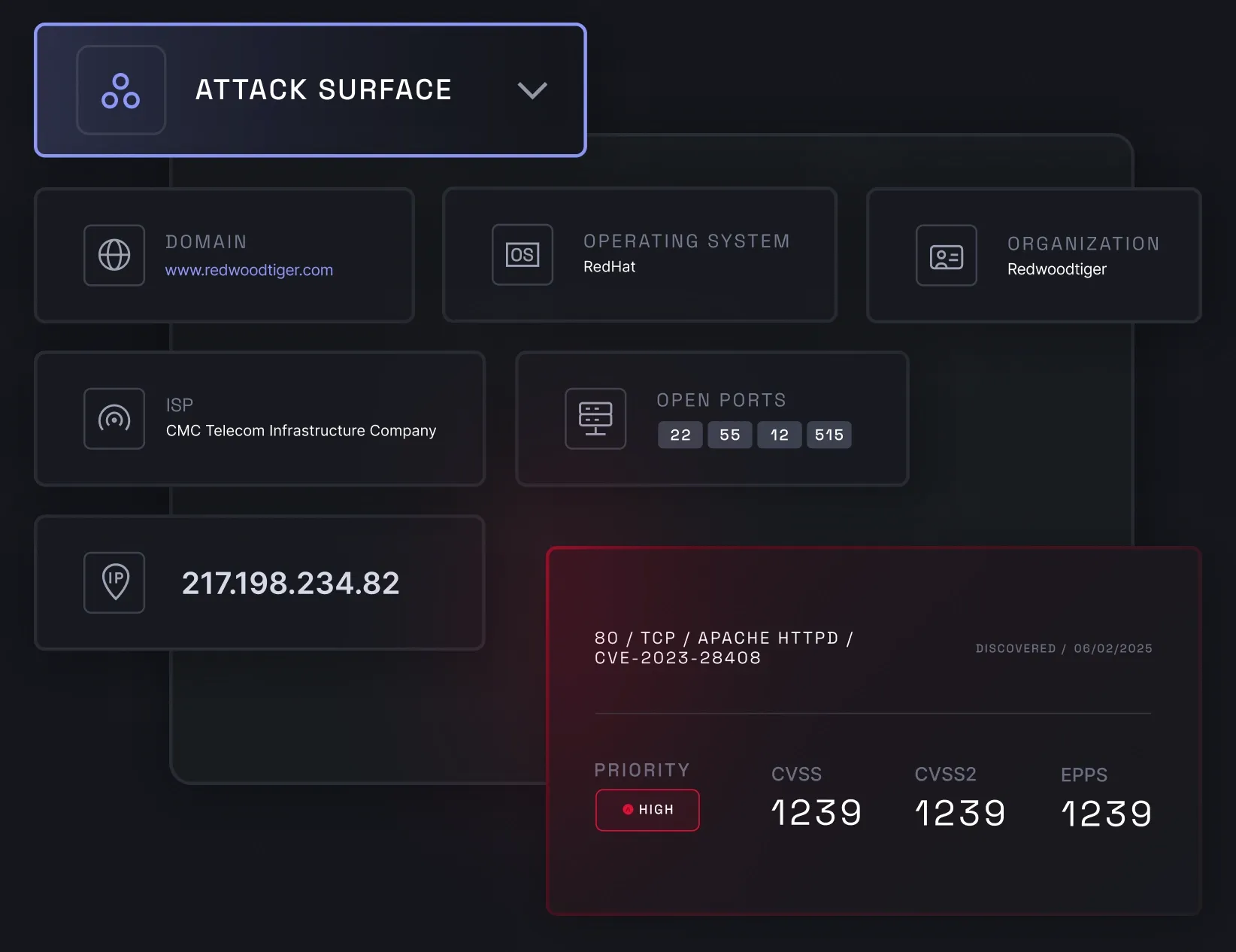
Attack surface management
Attack surface management helps you monitor your business's external attack surface and detect threats early. Through automatic asset discovery, such as domain enumeration, it ensures continuous visibility into your organization’s internet-facing assets, such as IP addresses with open ports and outdated technologies. This helps you reduce exposure and meet risk assessment and prevention requirements in many compliance standards, such as DORA and ISO 27001.
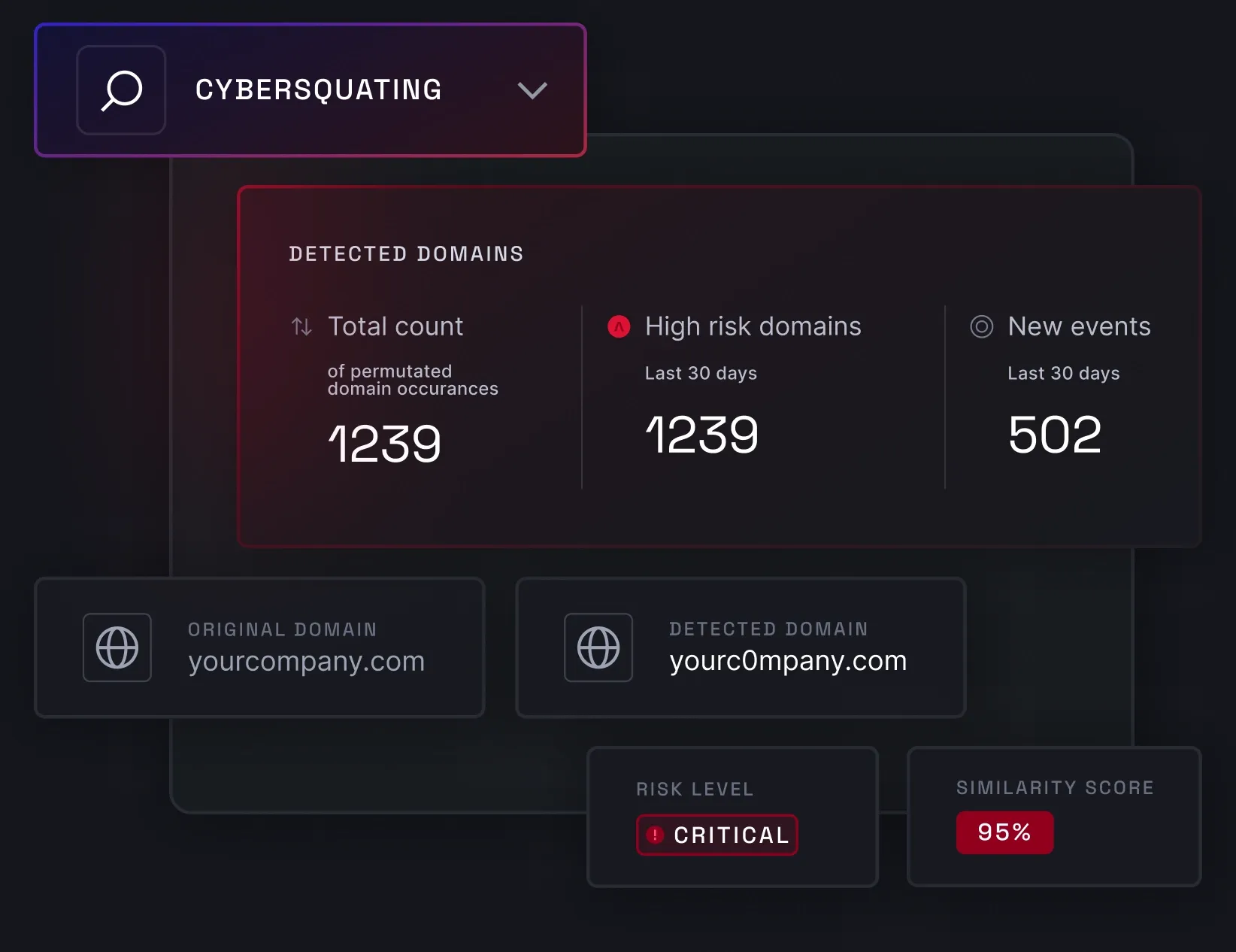
Cybersquatting detection
Cybersquatting detection finds lookalike domains, identifies fraud, and issues real-time alerts, providing a detailed view of every suspicious domain. It helps protect your brand reputation and ensures compliance with standards that require proactive domain and identity protection.
How NordStellar supports key regulations and standards
ISO 27001
NordStellar contributes to meeting the ISO 27001 standard by continuously analyzing external threat data. This includes monitoring the deep and dark web, identifying potential risks, and providing actionable insights to protect valuable company assets.
DORA
NordStellar supports proactive ICT risk management, the first pillar of the Digital Operational Resilience Act (DORA). It identifies vulnerabilities across your digital footprint and aids incident management, resilience testing, and third-party risk to help you meet DORA’s obligations.
NIS 2
NordStellar enhances visibility into external threats and helps organizations prevent, detect, and respond to incidents more efficiently. Automated threat monitoring and real-time alerts reduce response times and help significantly lower the potential impact on daily operations.
SOC 2
NordStellar contributes to SOC 2 compliance by detecting data leaks, providing continuous monitoring, and identifying impersonation domains. Real-time monitoring enables teams to detect and respond to risks before they impact security controls—a key audit requirement.
Key security compliance use cases with NordStellar
Why choose NordStellar
NordStellar helps organizations strengthen their compliance with industry standards and regulations by providing full visibility into external threat exposure management. It also helps meet evolving regulatory requirements by improving the company’s ability to manage third parties and respond to threats.
Frequently asked questions
Cybersecurity compliance helps protect your business from data breaches, costly penalties, and reputational damage. It builds trust with your customers by showing you prioritize security and ensure you're meeting the latest regulatory requirements.
Yes, NordStellar is suitable for all types of organizations. While medium-sized companies will likely get the most benefits from NordStellar, even small companies can use this solution to find and plug various vulnerabilities.
NordStellar provides risk assessments and monitoring tools that align with regulatory requirements, such as DORA, NIS 2, SOC 2, and ISO 27001. It also helps you detect risks more efficiently by automating external vulnerability scanning, dark web monitoring, and incident management.