Is your organization’s data exposed online? Scan to find out
Try our free dark web scan to see what kind of leaked data NordStellar can find about your company.
Run a free dark web scan. Here’s how
Enter your work email to launch the scan
Start by entering your company email address to check for potential data exposure.
NordStellar scans the dark web for leaks
NordStellar searches the dark web for any leaked credentials or company mentions.
View results & protect your organization
See what’s been found and learn how NordStellar can help prevent future breaches.
How NordStellar’s dark web monitoring works
NordStellar’s dark web monitoring provides businesses with real-time visibility into stolen or leaked data. By continuously scanning the dark web, it helps you detect breaches early and prevent potential threats.
NordStellar constantly scans the deep and dark web sources — from hidden forums to Telegram channels and ransomware blogs — detecting new leaks the moment they appear. Instead of a single snapshot, continuous monitoring gives you ongoing awareness of new risks as they emerge.
Monitor mentions of your company, employees, or partners across thousands of sources. From domains and emails to specific keywords or vendors, NordStellar helps you identify potential risks with both one-time searches and ongoing tracking.
Get notified the moment a new threat is detected — directly in email, Slack, Microsoft Teams, or other preferred channels. Automated alerts ensure your security team can respond before an incident grows.
Each detected mention comes with rich context — including links, author, and source details, sometimes even screenshots — so you can take action with confidence.
Deep and dark web forums
With many years of experience monitoring the deep and dark web, NordStellar has access to one of the largest data pools, detecting emerging threats across thousands of dark web forums.
Dark web marketplaces
NordStellar closely monitors major dark web marketplaces. Gain early visibility into your company’s compromised information and sensitive data being sold illegally.
Telegram channels
NordStellar actively monitors tens of thousands of cybercrime Telegram channels used for fraud, phishing, and identity theft. Quickly detect threats and prevent potential incidents.
Ransomware blogs
Hundreds of ransomware blogs are tracked to help assess threats of ransomware and data leaks. Identify risks of your organization being targeted by ransomware and prevent these devastating attacks.
800B+
total assets recaptured from
100B+
leaked credentials
75M+
malware logs analyzed
40K+
sources monitored
How NordStellar's dark web monitoring benefits your company
Detects threats before they escalate
NordStellar scans thousands of dark web sources and alerts you instantly when leaked data or dark web threats appear – helping your team act before attackers do.
Covers more sources for better protection
With access to one of the largest dark web data pools, NordStellar offers broader visibility than most dark web monitoring tools on the market.
Tracks brand, partner & supplier mentions
Monitor for keywords related not only to your company but also to your partners/vendors, helping identify third-party exposures that could put you at risk.
Protects brand image & customer trust
By identifying threats early, NordStellar helps prevent data leaks and impersonation attempts that could damage your reputation or customer trust.
Trusted by leading teams across the globe
NordStellar’s threat exposure management platform has earned praise from both the organizations we serve and independent cybersecurity experts.
Explore Nordstellar’s security solutions
NordStellar replicates the information-gathering stage of a cyberattack, allowing you to know what your attackers might know. This way, your cybersecurity team is able to detect critical threats and intervene at the earliest stages of an attack — before any real damage is done.
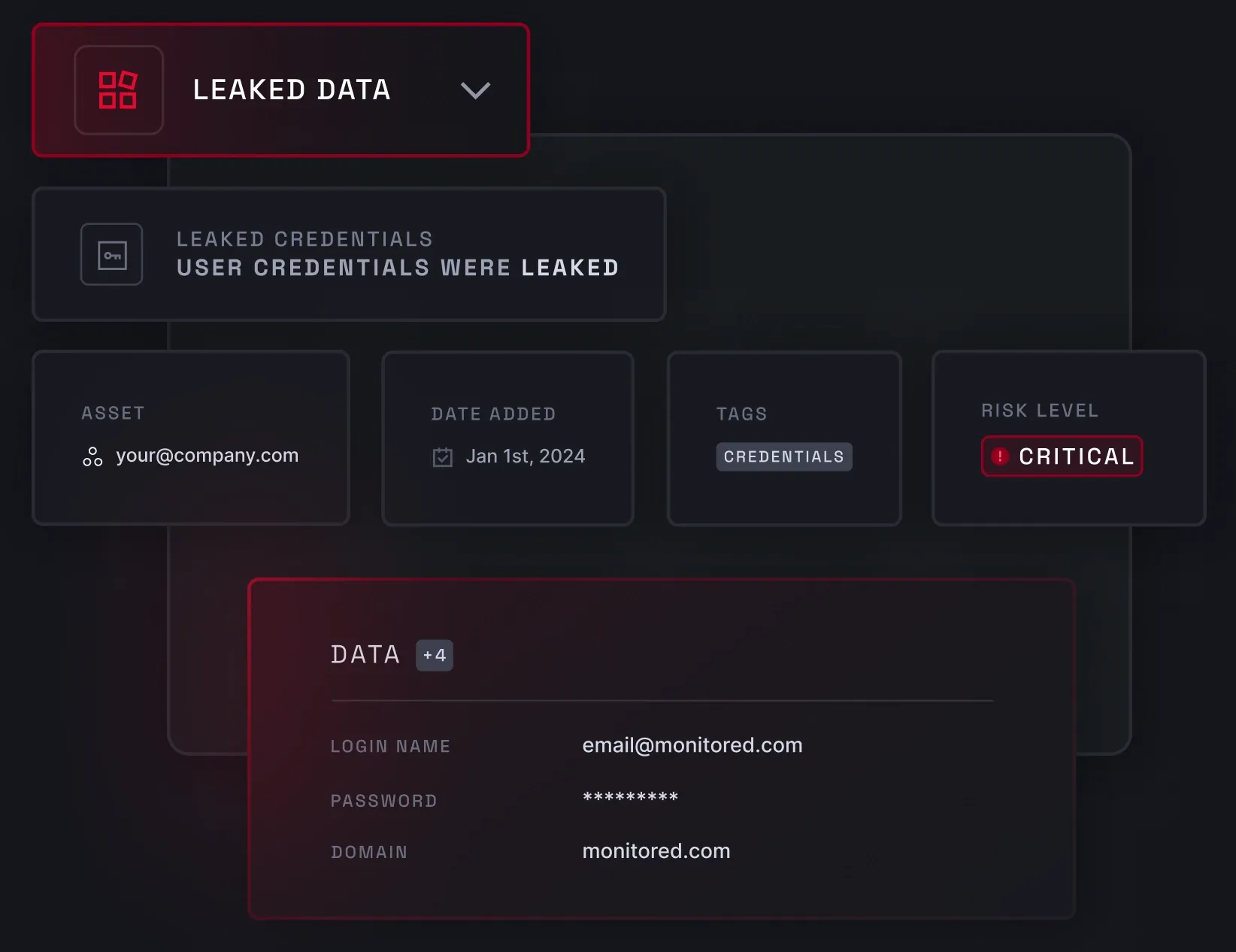
Data breach monitoring involves scanning the deep and dark web for leaked sensitive information linked to your business. To spot breached data, NordStellar checks infostealer malware logs, leaked databases, and collections of stolen credentials combinations. This solution provides real-time monitoring and the full context of past and present attacks.
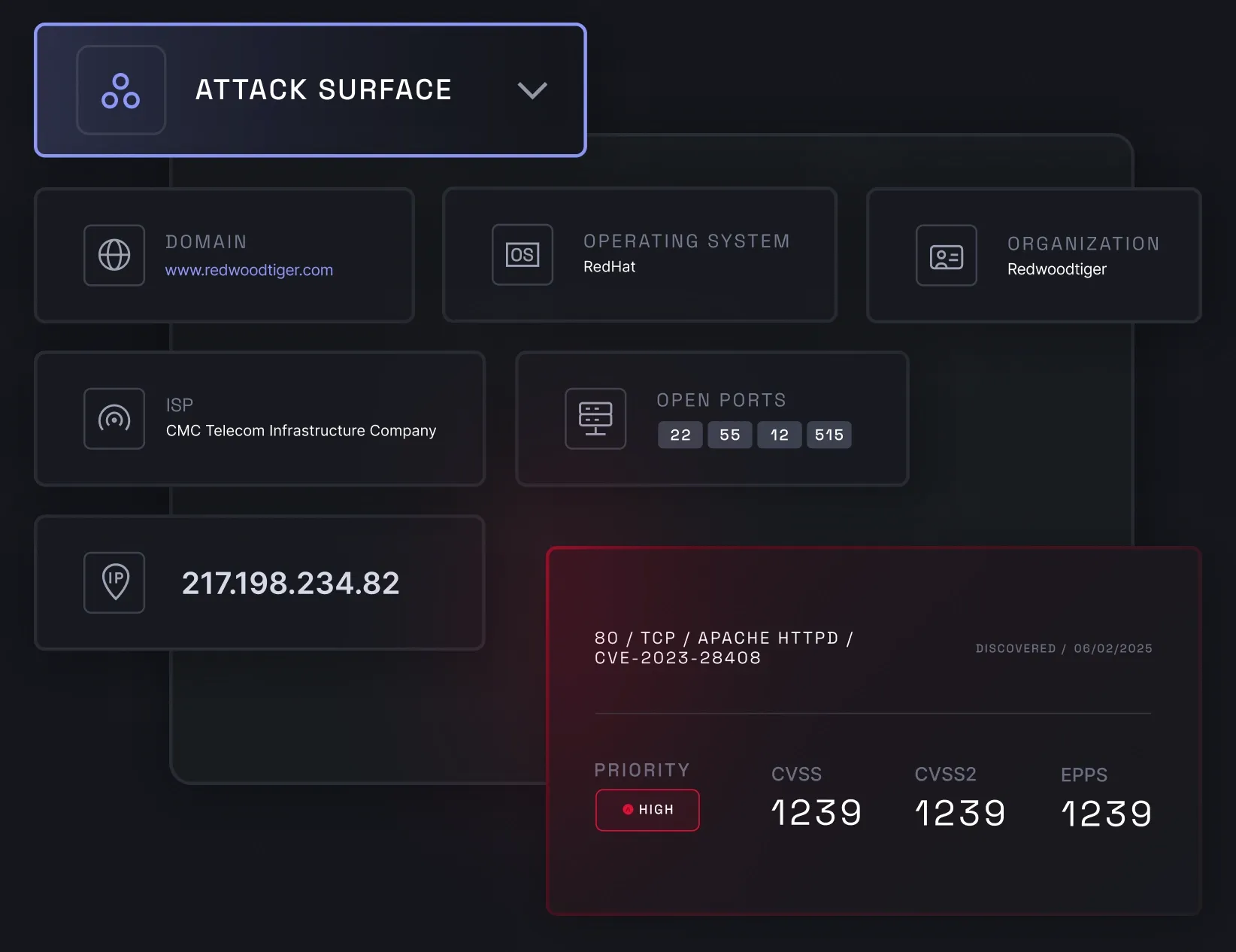
Attack surface management (ASM) helps you monitor your business's external attack surface to prevent potential cyber risks. It lets you efficiently manage your company's internet-facing assets, such as IP addresses with open ports and outdated technologies, by identifying vulnerabilities and security gaps within them.
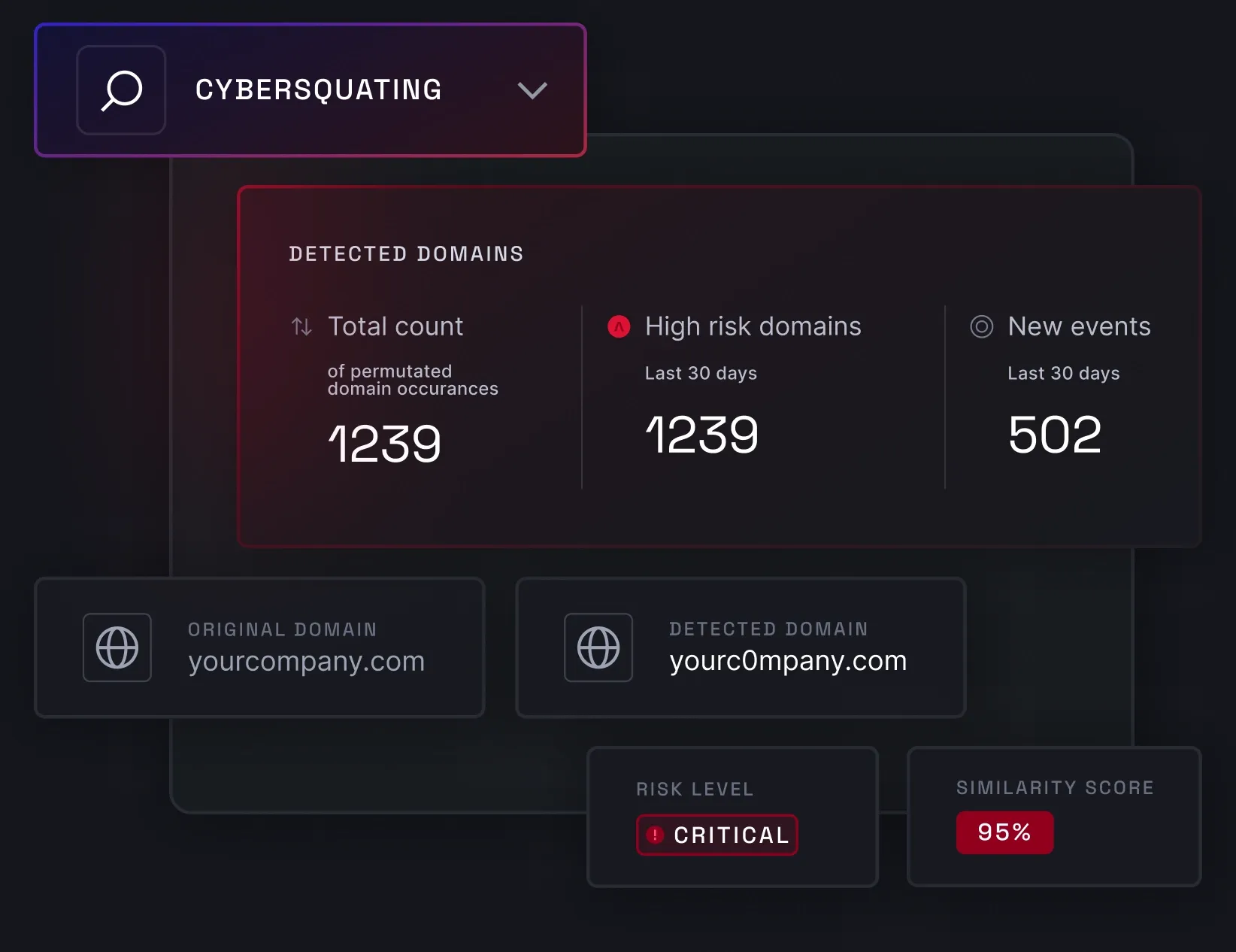
Cybersquatting detection helps you recognize and prevent threat actors from impersonating your brand. Using content and visual similarity algorithms enriched with AI, NordStellar can detect various domain manipulations and issue real-time alerts, providing a detailed view of each suspicious domain.
Choose the best plan for your business needs
Essential
Get your small to mid-size team started with threat exposure management and see exactly where your business is exposed.
From
$5000
YEAR*
Growth
Stay ahead of threats as your business scales with continuous monitoring of growing assets and deeper insights.
Reach out to sales
Brand Protect+
Add this to your Essential or Growth plan to quickly detect brand impersonations and get them taken down before they spread.
Reach out to sales
FAQ
Dark web monitoring is a solution that continuously scans hidden sources – like forums, marketplaces, and ransomware blogs – for exposed company data such as credentials or domain mentions. By alerting you the moment sensitive information appears, NordStellar helps your team respond quickly and prevent potential cyber incidents.
Yes. Dark web monitoring is completely safe because it doesn’t expose or share your company’s sensitive data. NordStellar monitors external sources – such as dark web forums, marketplaces, and ransomware blogs – and matches them against known identifiers like domains or email addresses without accessing your internal systems.
A one-time scan gives you a snapshot of your current exposure, but monitoring the dark web ensures ongoing visibility as new leaks and mentions appear daily. Alerting you the moment new risks emerge helps you respond before threats cause actual harm.
If NordStellar detects exposed data, your security team should immediately reset any compromised passwords, investigate potential breaches, and review access controls. The platform provides full context – including source links and timestamps – to help verify and contain the exposure quickly.
The free dark web scanner is a quick online tool that lets you see an example of leaked data linked to your company email. NordStellar’s full dark web monitoring solution provides continuous, automated scanning across thousands of sources, real-time alerts, and detailed intelligence for ongoing protection.
Yes, the free scan is completely secure. It only checks your work email against existing breach databases and does not collect, share, or store sensitive information beyond what’s needed to show your results.
You’ll see a summary of whether your company email appears in known breaches, along with examples of exposed data types. The report offers a preview of the insights available in NordStellar’s full dark web monitoring platform.
No. Your email is used only to perform the scan and generate your report. NordStellar does not store or reuse your information once the results are displayed.