Malware detection based on threat intelligence
- Uncover hidden infostealer malware that slipped through the cracks of traditional antimalware measures, such as EDR, XDR, and MDR.
- Identify devices and employee accounts affected by infostealers, helping you direct your cybersecurity efforts.
- Get full context on incidents, including information on infected devices and exfiltrated data, to help with your cyber response.
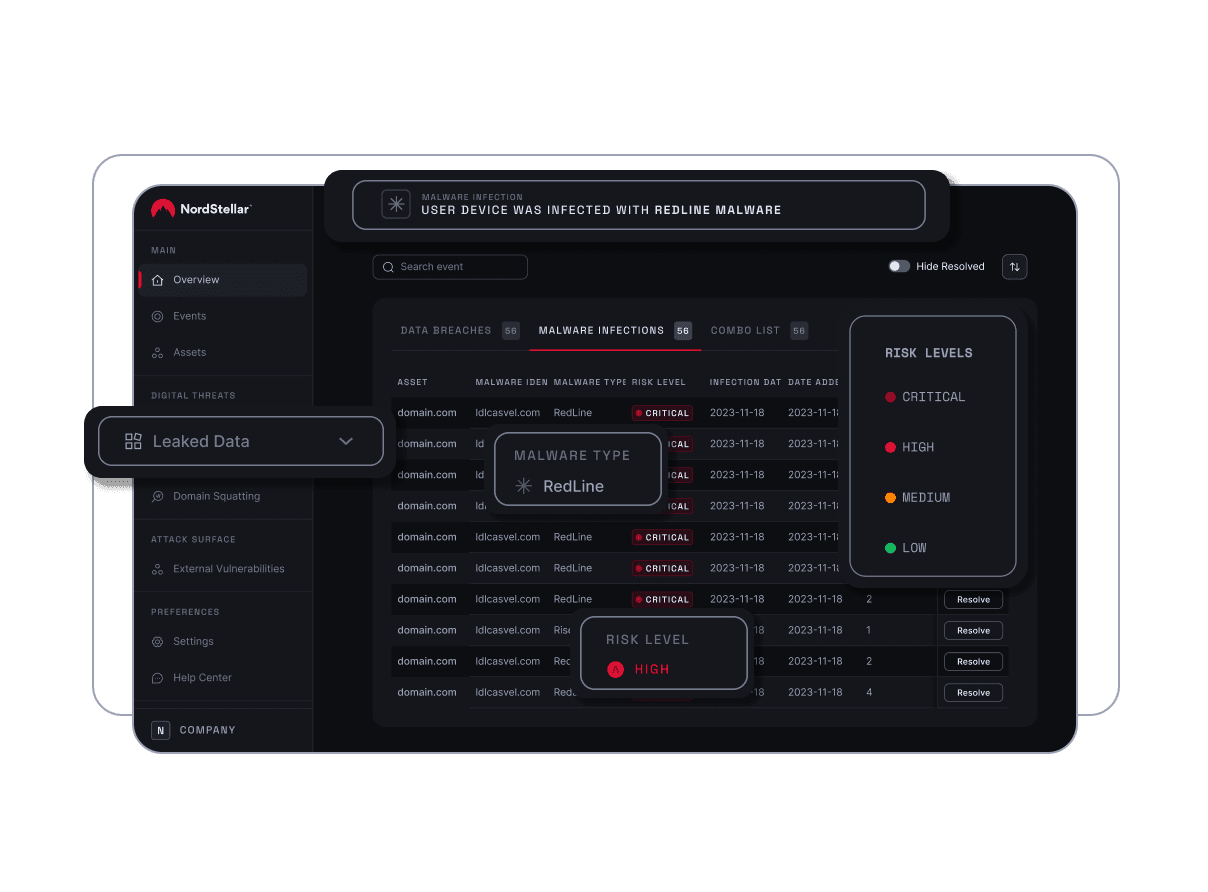
What is NordStellar's malware detection?
Malware detection traditionally refers to the process of scanning managed endpoints and network infrastructure for signs of malware. But NordStellar operates on a completely different plane. Our malware detection is based on continuously monitoring the criminal underground (including dark web forums, hacker Telegram channels, and data marketplaces) for infostealer logs linked to your organization — evidence of active malware infection.
These infostealer logs contain compromised information, ready for exploitation by threat actors. NordStellar’s malware detection solution focuses on recognizing these unique data artifacts, attributing them to specific infostealer families, and immediately correlating them with your organizational footprint.
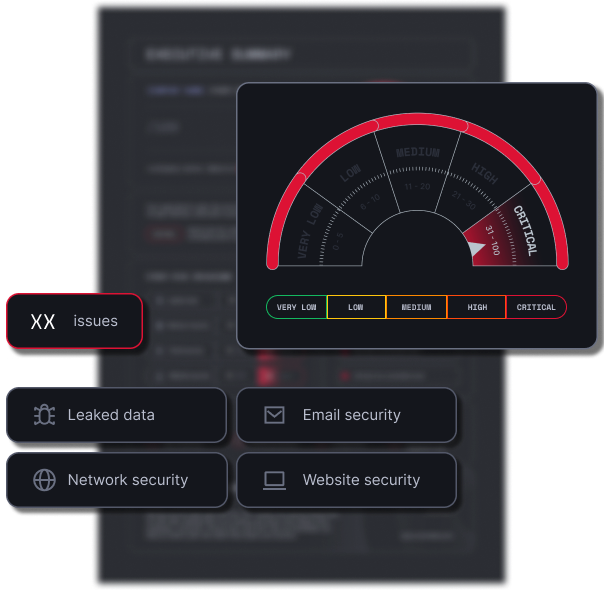
Curious about your company’s security posture?
Start with a free Risk Report from NordStellar — your first look into the threat landscape we help security teams navigate and stay ahead of.
What’s inside:
- Your personalized Cyber Risk Score
- Key insights across leaked data, email, web, and network security
- A snapshot of exposed or compromised data linked to your domain
How does NordStellar’s malware detection work?
NordStellar’s malware detection solution is based on post-infection detection using threat intelligence from the dark web.
MONITORING
NordStellar continuously monitors external threat sources (like darknet sites, underground marketplaces, private and public channels on encrypted messaging platforms, and leak boards) for signs that information from your organization has been compromised.
DATA INGESTION
Our system rapidly ingests the raw infostealer log data, then uses advanced parsing and normalization algorithms to extract relevant data points, such as credential pairs, session cookies, financial data, and personally identifiable information.
ATTRIBUTION
NordStellar transforms the bare facts into useful findings, giving your security team actionable intelligence. We filter out irrelevant data, identify the malware used in the attack, and seek out additional details (such as timestamps and leak sources) for more context.
ALERTS
NordStellar immediately generates prioritized alerts when malware activity linked to your assets is detected. Your security teams may be notified over regular channels, such as email or Slack, or get direct API calls to SIEM, SOAR, or TIP platforms.
REMEDIATION
Validated intelligence gives your security team the context needed to launch a targeted response to the threat. With the information provided, you can mitigate immediate risks (for example, by changing the affected credentials), contain the infection, and strengthen your defences against future attacks.
Why antivirus, EDR, XDR, and MDR solutions can't fully protect against infostealing malware
While antivirus, endpoint detection and response (EDR), extended detection and response (XDR), and managed detection and response (MDR) solutions all have their place in your cybersecurity framework, they can leave gaps in your defenses:
Post-compromise blind spots
EDR and XDR focus on detecting attacks in progress, but they are poorly positioned to track down infostealers that manage to slip through. They may not alert you to the fact that your sensitive data is now being sold on the dark web — or that the infecti
MFA bypass via session cookies
Modern infostealers can steal active browser session cookies to bypass MFA security and gain direct access to legitimate sessions. Endpoint-focused tools that don't analyze external post-compromise indicators will not protect you from this threat.
"Patient zero" (often off-network)
Many initial infections occur on personal devices used for corporate access (BYOD) or less-monitored remote endpoints. The initial attack and exfiltration can be carried out outside of secure networks to bypass EDR.
No external validation
EDR, XDR, and MDR alert you to suspicious activity — but they cannot confirm if the compromised credentials being used were bought on the dark web. Without a trusted external intelligence source, this gives threat actors a verified pathway into your envir
Outdated cybersecurity databases
A lot of antivirus software relies on known or pattern-matching malware signatures for detection — but infostealers evolve quickly, making it hard for antivirus tools to keep up.
What can NordStellar’s malware detection reveal?
NordStellar provides actionable, real-time threat intelligence derived directly from the dark web. This information closes a critical visibility gap in your organization’s cyberdefenses.
Details about potentially infected machines, including operating systems, hardware, and IP addresses.
Names, addresses, phone numbers, and other PII that can be used for identity theft, social engineering, or targeted phishing.
The type of malware used in the attack, diagnosed from over 40 of the most prominent infostealer malware families.
Leaked usernames, passwords, and other authentication factors directly associated with your corporate domains, SaaS applications, and VPNs.
Credit card numbers, banking credentials, and cryptocurrency wallet details that could expose owners to direct financial loss or fraud.
Logins and tokens from popular applications like Steam, Discord, and Telegram, which might serve as pivot points for attackers.
Indicators of active session cookie compromise, which attackers use to bypass MFA and gain unauthorized access to accounts without a password.
The benefits of NordStellar’s malware detection
Real-time threat alerts
Our platform continuously scans data from deep and dark web sources (such as hacker forums, Telegram channels, and ransomware blogs) to identify infostealer leaks and alert your security team to malware.
Immediate response to threats
By alerting you to infostealer activity, NordStellar lets you purge your systems of dangerous malware targeting login credentials, credit card details, and other sensitive information.
Reduced business disruption
Thanks to malware detection, your organization can root out budding issues before they escalate into costly, time-consuming problems. Smart prevention lets you enjoy smooth business operations without having to stop due to cyber incidents.
Who else will benefit from NordStellar’s malware detection?
NordStellar’s malware detection solution is not just for your cybersecurity team — it can greatly benefit your regular employees and customers.
Your employees
Quick detection of infostealer malware gives your staff enough warning to reset account passwords, lock down vulnerable devices, and install security patches. This early action can secure your organization’s end points and stop further infiltration by att
Your customers
By notifying your customers of leaked data quickly, you give them a chance to secure their personal and financial information before it’s exploited. Early transparency can mitigate the worst effects of infostealer incidents.
Explore more security solutions from NordStellar
NordStellar lets your cybersecurity team patch critical vulnerabilities and intervene at the earliest stages of an attack – before any real damage is done.

Dark web monitoring allows you to track all keywords associated with your business across deep and dark web communities, such as hacker forums, illicit marketplaces, and Telegram channels. It helps you uncover brand mentions, issues with vendors, and leaked information about your VIP personnel.

Data breach monitoring involves scanning the deep and dark web for leaked sensitive information linked to your business. To spot breached data, NordStellar checks infostealer malware logs, leaked databases, and collections of stolen credentials combinations. This solution provides real-time monitoring and the full context of past and present attacks.

Attack surface management (ASM) helps you monitor your business's external attack surface to prevent potential cyber risks. It lets you efficiently manage your company's internet-facing assets, such as IP addresses with open ports and outdated technologies, by identifying vulnerabilities and security gaps within them.

Cybersquatting detection helps you recognize and prevent threat actors from impersonating your brand. Using content and visual similarity algorithms enriched with AI, NordStellar can detect various domain manipulations and issue real-time alerts, providing a detailed view of each suspicious domain.
FAQ
“Malware” (a portmanteau of “malicious” and “software”) is the umbrella term for any kind of code that is deliberately inserted into a system to cause harm. The following are common malware types:
- Infostealers are a broad category of malware designed to extract sensitive information from victims. NordStellar’s malware detection solution is based on recognizing the activity of different types of infostealers.
- Spyware is a type of malware that collects information about the victim’s actions. Some malicious programs can be classified as both infostealers and spyware.
- Ransomware uses encryption to lock away important files or system functions until the victim agrees to pay a sum of money. Common ransomware attack vectors include malvertising campaigns, phishing emails, and browser exploits.
- Trojans (named after the fabled Trojan horse of antiquity) are a type of malware that try to pass off as another file to trick the victim into opening them.
- Adware is software that, like the name suggests, forcefully displays advertisements on the host device.
- Worms are programs that seek to spread through the network, infecting other devices at an exponential rate. They are instrumental in the creation of botnets.
Each malicious program causes the infected system to behave in different ways, although the vast majority of malware tries to operate under the radar. One simple sign that something is off is seeing your device’s fan turn on at strange times, indicating that a hidden program is working intently in the background. These clandestine operations may also cause your device to start freezing up or stuttering at random times.
Infostealing malware can affect both Windows and Mac devices — neither system is inherently more resilient to infostealers. While there may be more infostealer incidents reported on Windows, this is a consequence of the widespread popularity of the operating system, presenting more potential targets for attackers.
Botnets are networks of compromised systems operating on the instructions of the attacker, while infostealers are malware that secretly relays sensitive data from the infected computer. Both are dependent on each other — botnets need malware to control the system, while infostealers often require botnets to successfully transfer the data to the hackers’ servers.
Malware-as-a-service is a criminal business model where hackers offer pre-packaged malicious software for sale or rent. These services are frequently used by less tech-savvy individuals to carry out cyberattacks.
When you receive a malware alert from NordStellar, you should:
- Analyze the details, such as the strain of malware involved and what data was leaked.
- Contain the threat by blocking compromised accounts and taking the affected devices offline.
- Mitigate the damage — for example, by changing compromised credentials and revoking existing session cookies.
- Investigate the attack using the details in NordStellar’s malware alert.
- Fix the system with patches, cybersecurity software updates, and follow-up malware scans.
- Monitor the situation. Keep an eye on the affected assets for repeat attacks.
The best malware detection tools offer real-time protection and give you actionable data. Continuous monitoring is key to quickly identifying potential infections and dealing with the problem early. For example, NordStellar’s malware detection solution scours criminal channels, such as dark web marketplaces and underground chat rooms, for signs of your compromised data — and once it uncovers signs of infostealers at work, it gives you all the details you need to remedy the situation.