Join 1000+ MSPs/MSSPs, resellers, and technology advisors ir our network
Expand your offerings with NordStellar
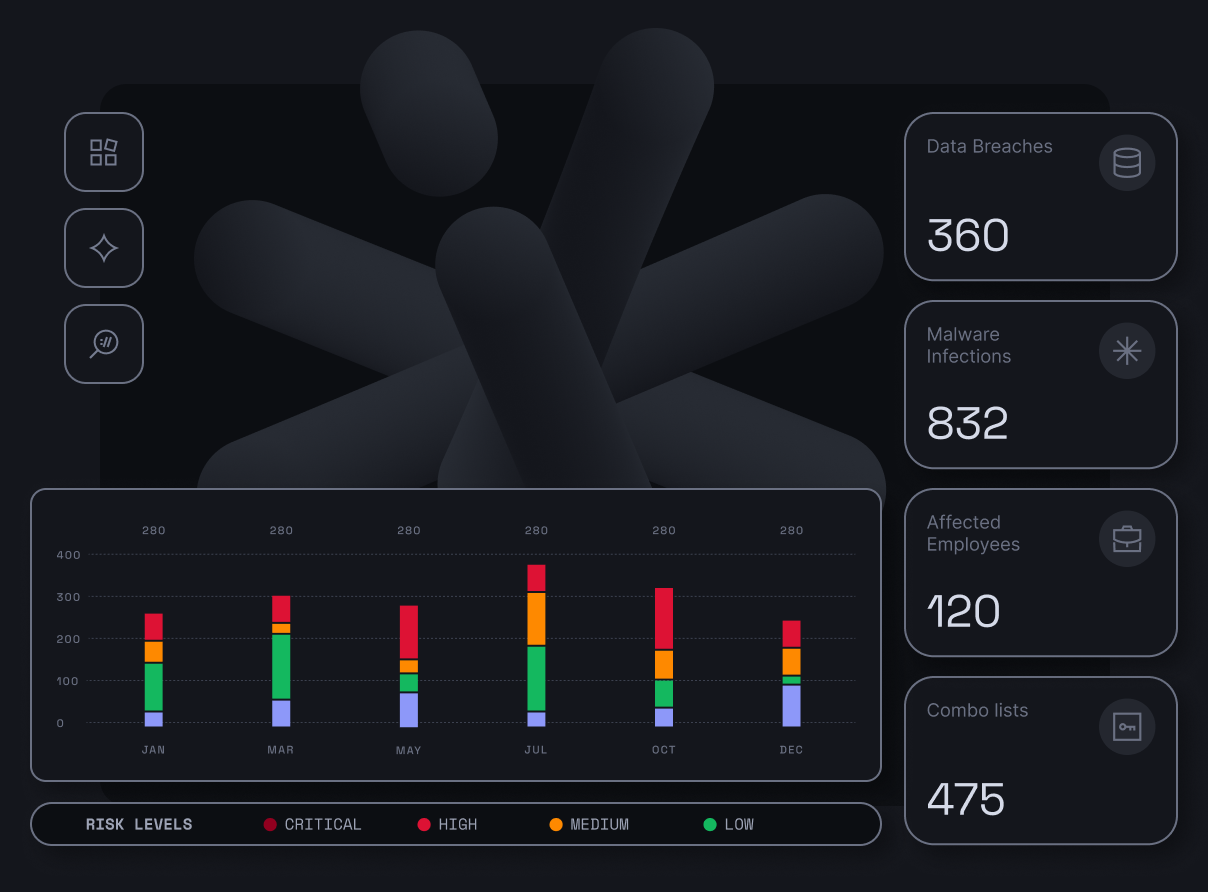
NordStellar replicates the information gathering stage of a cyberattack, providing your clients with insight into what attackers might know. This empowers you to detect critical threats early and take action before any damage is done.

Dark web monitoring allows you to track all keywords associated with your client’s business across deep and dark web communities. It helps you uncover your client’s brand mentions, issues with vendors, and leaked information about your client’s VIP personnel.

Data breach monitoring involves scanning the deep and dark web for leaked sensitive information linked to your client’s business. To spot breached data, NordStellar checks infostealer malware logs, leaked databases, and collections of stolen credentials combinations. This solution provides real-time monitoring and the full context of past and present attacks.

Attack surface management (ASM) helps you monitor your client’s business’s external attack surface to prevent potential cyber risks. It lets you efficiently manage your client’s company’s internet-facing assets, such as IP addresses with open ports and outdated technologies, by identifying vulnerabilities and security gaps within them.

Cybersquatting detection helps you recognize and prevent threat actors from impersonating your client’s brand. Using content and visual similarity algorithms enriched with AI, NordStellar can detect various domain manipulations and issue real-time alerts, providing a detailed view of each suspicious domain.
Why choose NordStellar?
Data at a glance
Detailed insights from one of the largest data pools, combining various data sources with vast coverage around the deep and dark web.
Instant detection
Reduced data leak detection times with 24/7 automated, real-time monitoring.
Compliance made easy
Simplified compliance with regulations like DORA, NIS 2, SOC 2, and ISO 27001.
Experts you can trust
Proven threat intelligence expertise backed by Nord Security, the creators of NordVPN.
Explore partnership opportunities with NordStellar
MSP and MSSP
Get an intuitive multi-tenant management portal without any upfront investments, post-paid monthly billing, trial accounts for your clients, and an NFR license for your company’s needs.
Value Added Resellers
Get dedicated account manager, extensive support and training, NFR licenses, SPIFF, MDF, deal registration, event participation, and cybersecurity education for your team and partners – resources designed to expand your reach
Distributors
Get dedicated account manager, extensive support and training, NFR licenses, SPIFF, MDF, and deal registration, event participation, marketing investment, and cybersecurity education for your team and partners.
Technology advisors
Receive deal registration, high-profit commissions, free trials for end-customers, and SPIFF through Telarus, Avant, and Intelisys in the US.
Become a partner
Over 1,000 partners already rely on us—become one of them. Just fill out the form and we’ll handle the rest. Enjoy Partner Program benefits:
Easy onboarding for your clients
High entry margins to grow your profits
Hardware-free solution
Dedicated training and 24/7 tech-minded support
offer a full suite of trusted solutions
Nord Business Suite brings together powerful cybersecurity solutions—designed for business, built for ease. With a unified user experience across all products, your clients get up and running quickly, with minimal training and seamless onboarding.

Nordlayer
Network security platform for business
Nordpass
Password manager for business
Nordstellar
Threat exposure management platform
FAQ
Threat exposure management works by identifying the biggest risks faced by an organization and adopting security measures to reduce them. To do this, TEM platforms must be able to observe the business’s attack surface, determine which vulnerabilities to prioritize, and offer effective solutions to the most pressing problems.
For example, NordStellar continuously scans the deep and the dark web for keywords associated with your business, hunting for undiscovered data leaks and potential attack discussions. Dark web monitoring gives your business advance warning of these events, letting you take early action in accordance with your organization’s security policies to minimize the damage. Furthermore, any data breach discovered can be thoroughly analyzed to prevent similar incidents in the future.
Domains, email addresses, passwords, phone numbers, IP addresses, keywords.
A variety of deep & dark web sources, including forums and marketplaces, as well as Telegram, data breach databases, malware logs, combo lists, vulnerability databases, and external scans.
Configurable alerts can be delivered via platform notifications, email, Slack, or through API integration.
Designed for ease of use, with intuitive dashboards, visualizations, and a help center.
Yes, NordStellar's API allows for a wide range of integrations with various SIEM and SOAR platforms, like Splunk, QRadar, Datadog, Fortinet, Sentinel, Elastic, or Cortex.