What is supply chain risk management?
Supply chain risk management (SCRM) is the practice of identifying, monitoring, and mitigating threats that could compromise your extended business ecosystem. Every organization relies on vendors, suppliers, partners, and SaaS tools, each introducing potential cybersecurity vulnerabilities. A breach at a cloud service provider, a compromised logistics partner, or exposed supplier credentials can quickly ripple back to your business.
NordStellar helps reduce these risks by continuously monitoring supply chain–related keywords, such as vendor names or product mentions, across the dark web. This proactive visibility enables organizations to detect exposures or planned attacks before they escalate — forming the foundation of effective cybersecurity supply chain risk management (C-SCRM).
Importance of supply chain risk management
Mitigate costly data breaches and cyber threats
Almost every business depends on SaaS platforms and third-party tools to function, from email services to cloud storage. Proactive monitoring helps uncover supplier vulnerabilities early, preventing cyber incidents that could lead to significant financial and reputational damage.
Strengthen compliance across third-party networks
Regulators now expect organizations to manage not only their own security but also the risks posed by their vendors. Strong supply chain risk management helps identify and monitor those third-party risks while supporting compliance with frameworks such as NIS2, DORA, and SOC 2.
Reduce supply chain disruptions and downtime
Cyber incidents at a single supplier can halt production, delay services, or block customer access. By spotting vulnerabilities before they escalate, businesses can minimize downtime, protect operations, and keep their supply chain running smoothly.
Address industry-wide risks before they spread
Some threats target entire sectors, not just a single company. Effective SCRM means monitoring collective risks across your sector to stay ahead of evolving threats that may hit competitors or similar businesses.
Evaluate vendors through dark web intelligence
Businesses can evaluate potential partners by scanning the dark web for vendor-related exposures, leaks, or threat discussions. This helps ensure that only secure vendors are selected and onboarded.
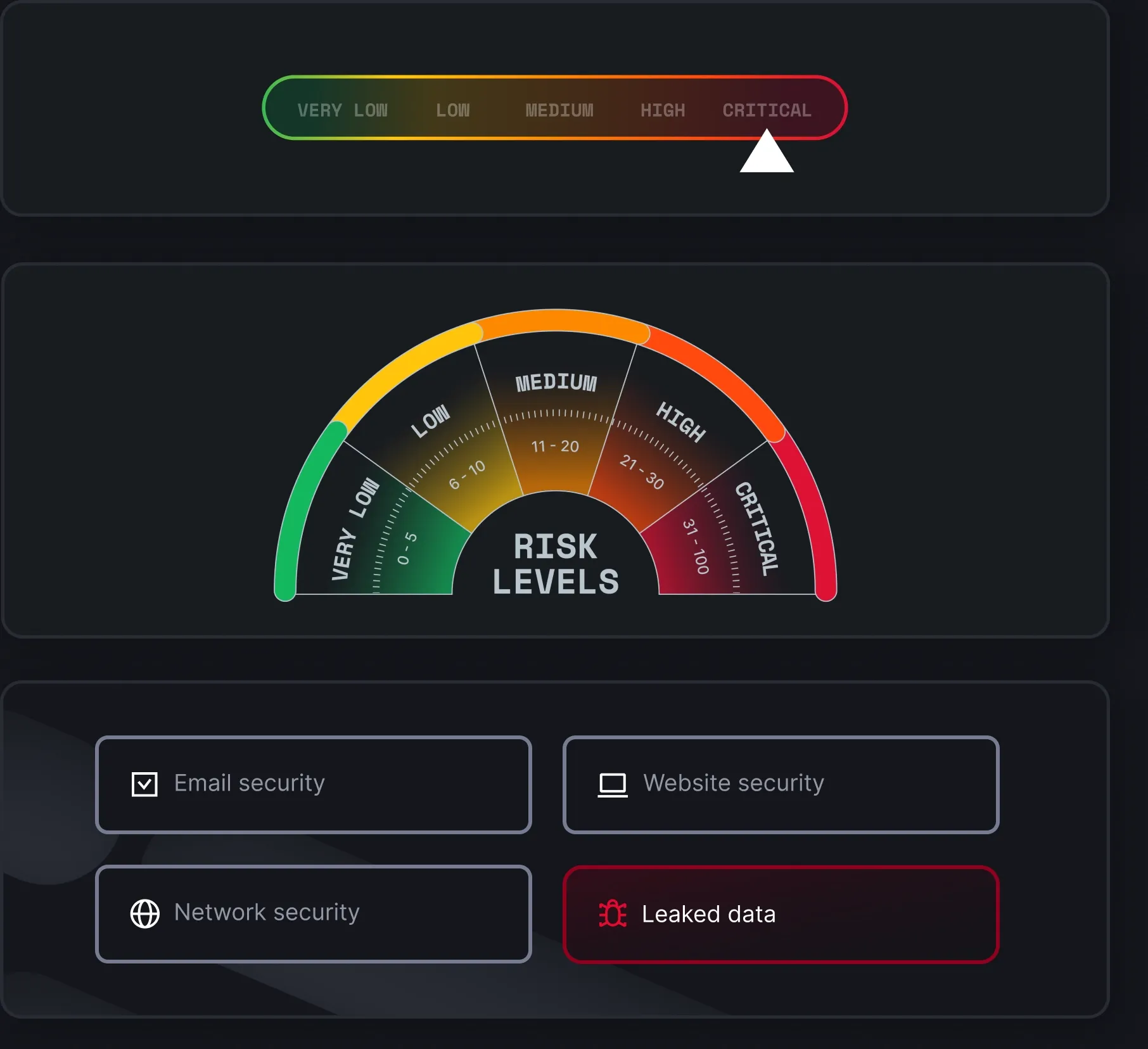
Curious about your company’s security posture?
Start with a free Risk Report from NordStellar — your first look into the threat landscape we help security teams navigate and stay ahead of.
What’s inside:
- Your personalized Cyber Risk Score
- Key insights across leaked data, email, web, and network security
- A snapshot of exposed or compromised data linked to your domain
How NordStellar helps secure your supply chain
Real-time dark web monitoring for supplier risks
NordStellar tracks various keywords, such as company names, product names, or digital assets, across the dark web. It continuously scans ransomware blogs, forums, marketplaces, and private channels, delivering real-time alerts with full context, source, and threat actor details.
Detect vulnerabilities before they escalate
From leaked credentials and sensitive documents to supplier brand mentions, NordStellar uncovers exposures being discussed or traded underground. Early warnings allow you to address risks before they turn into large-scale breaches.
Spot ransomware attacks on vendors and partners
The platform monitors ransomware blogs, so if a partner or supplier is listed, you’re immediately alerted, helping you assess the impact and protect sensitive data shared with that vendor.
Track evolving trends across the dark web
NordStellar monitors dark web activity tied to vendors and industry, identifying any potential exploits and vulnerabilities. This visibility into emerging threats helps guide strategic decisions and strengthens resilience across your ecosystem.
Protect operations with secure vendor choices
NordStellar provides insights into vendor exposure on the dark web, helping you choose partners with stronger security practices. By avoiding high-risk suppliers, you reduce the chance of disruptions and protect the continuity of your operations.
Understanding the supply chain risk management process
Monitor suppliers and the vendor ecosystem
Continuously track your supply chain for exposures such as leaked credentials, sensitive documents, or counterfeit mentions detected on the dark web.
Threat detection and risk analysis
Receive real-time alerts with full context when supplier-related findings appear. Investigate the source and assess the potential impact.
Remediation and risk mitigation
Use NordStellar’s insights to take targeted actions, whether engaging vendors or improving processes, helping safeguard operations and meet compliance requirements.
Who can benefit from supply chain risk management?
All organizations that rely on suppliers, vendors, or partners can gain from proactive supply chain risk management. The need spans across industries, from highly regulated sectors to consumer-focused businesses.
Manufacturing
Finance
Technology & IT Services
Retail & Consumer Goods
Entertainment & Media
Energy
Public sector
Critical infrastructure
Explore more security solutions from NordStellar
Beyond supply chain risk management, NordStellar offers a full suite of threat exposure solutions to strengthen your cybersecurity posture and safeguard every part of your digital ecosystem.
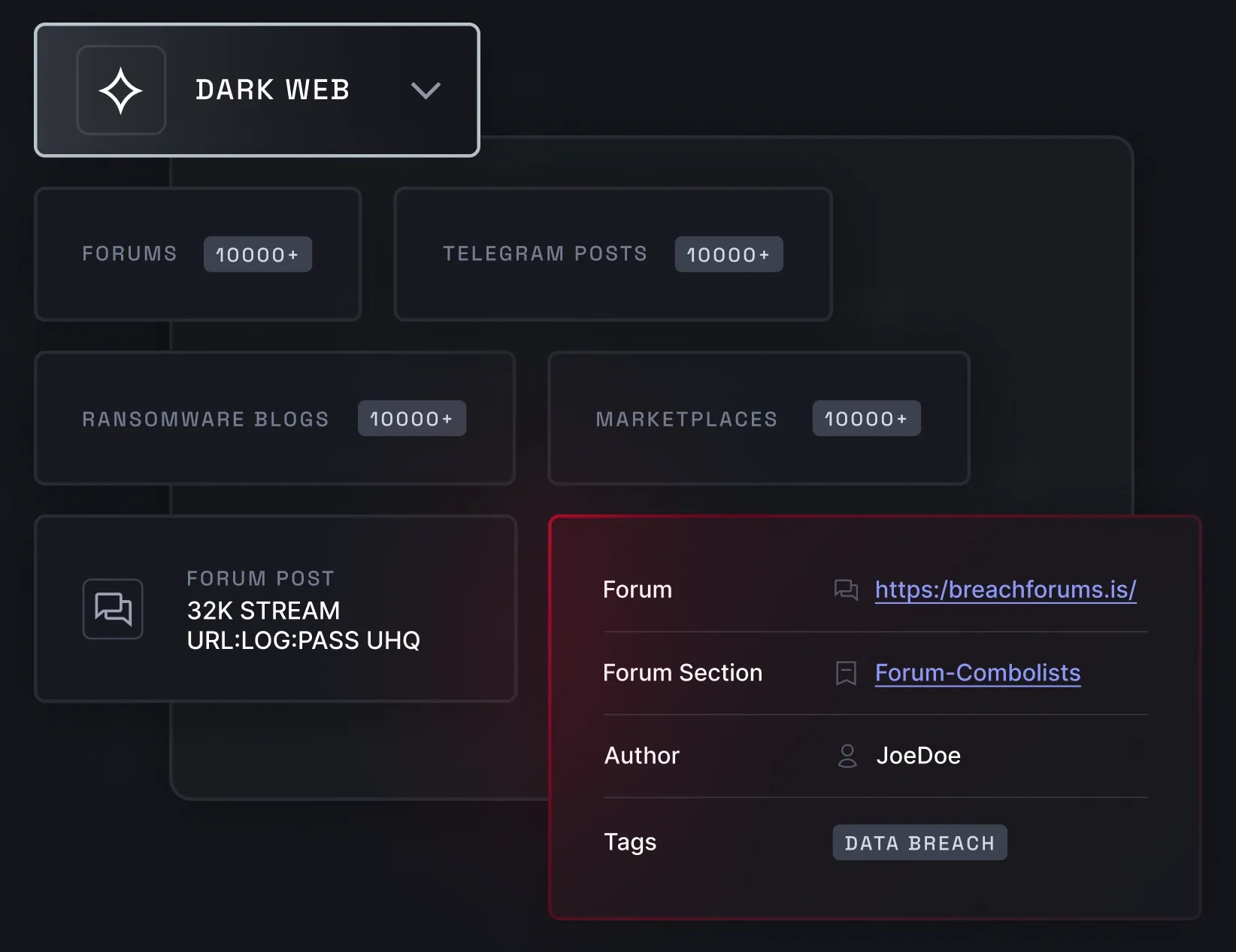
Dark web monitoring
Dark web monitoring allows you to track all keywords associated with your business across deep and dark web communities, such as hacker forums, illicit marketplaces, and Telegram channels. It helps you uncover brand mentions, issues with vendors, and leaked information about your VIP personnel.
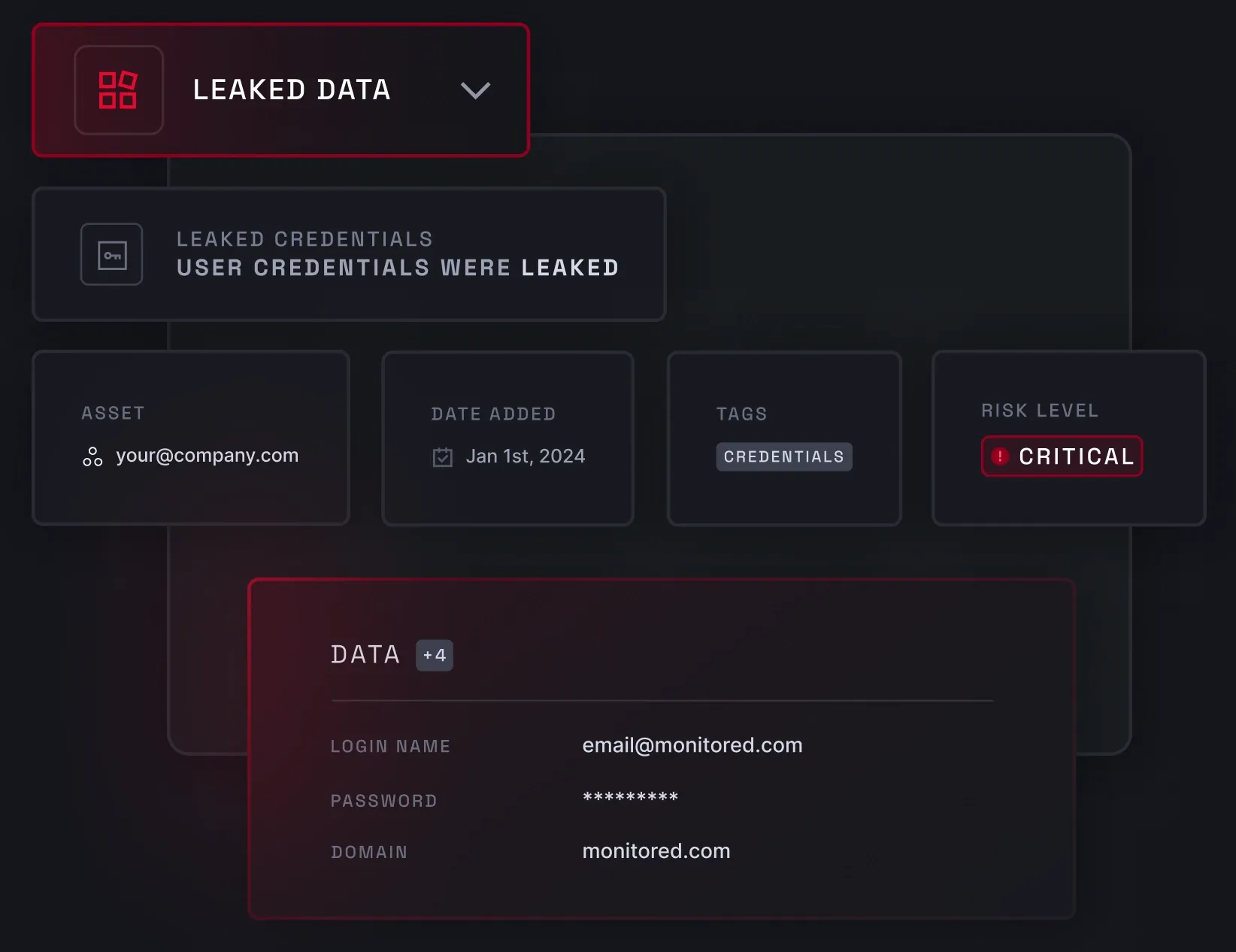
Data breach monitoring
Data breach monitoring involves scanning the deep and dark web for leaked sensitive information linked to your business. To spot breached data, NordStellar checks infostealer malware logs, leaked databases, and collections of stolen credentials combinations. This solution provides real-time monitoring and the full context of past and present attacks.
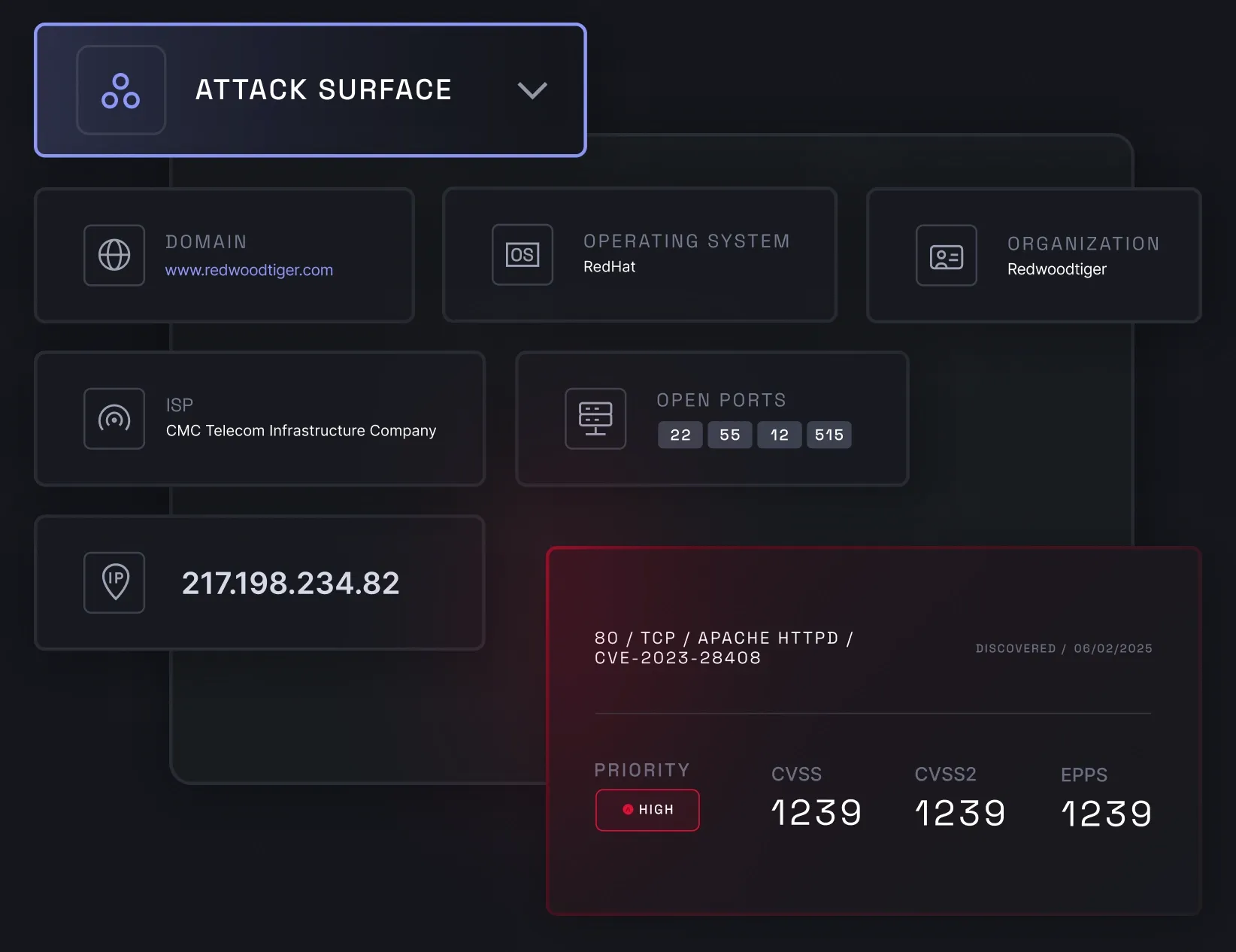
Attack surface management
Attack surface management (ASM) helps you monitor your business's external attack surface to prevent potential cyber risks. It lets you efficiently manage your company's internet-facing assets, such as IP addresses with open ports and outdated technologies, by identifying vulnerabilities and security gaps within them.
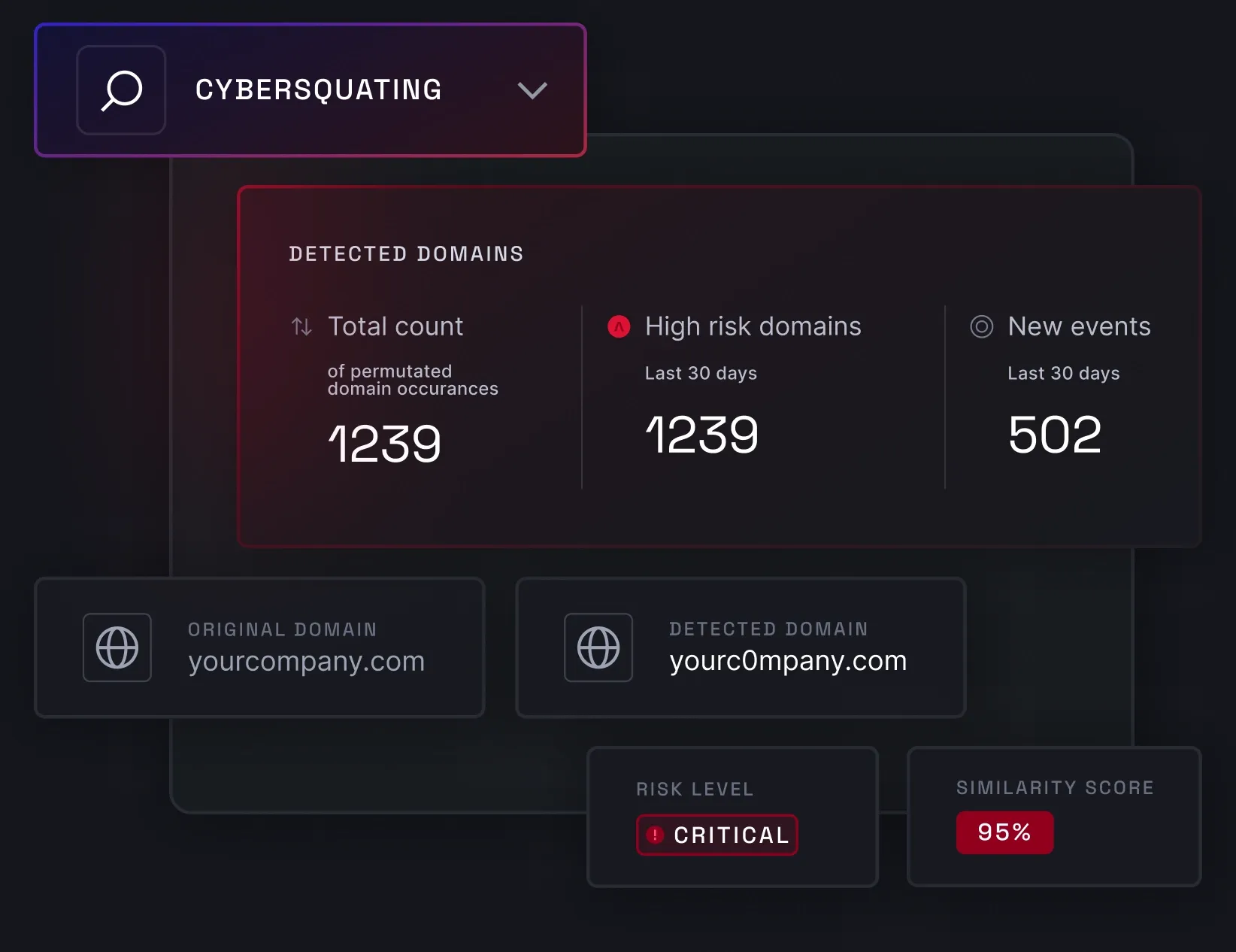
Cybersquatting detection
Cybersquatting detection helps you recognize and prevent threat actors from impersonating your brand. Using content and visual similarity algorithms enriched with AI, NordStellar can detect various domain manipulations and issue real-time alerts, providing a detailed view of each suspicious domain.
FAQ
Yes. Implementing supply chain monitoring solutions strengthens compliance in areas such as vendor management, supply chain security, and third-party risk, supporting standards like NIS 2, DORA, and SOC 2.
Yes. NordStellar’s supply chain risk management solution can be accessed via a platform or integrated via API to fit seamlessly into your existing workflows.
Threat intelligence uncovers risks such as leaked vendor data or planned attacks on the dark web. NordStellar delivers real-time alerts and actionable insights to help mitigate these threats.
You can set up monitoring for keywords like vendor names, partner brands, industries, or competitors. NordStellar then scans dark web sources and alerts you immediately with context, including the source, date, and full message.
Yes. On-demand cyber risk reports act as a supply chain risk assessment, giving you a quick view of a vendor’s security posture, including a Cyber Risk Score and insights on leaked data, email, web, and network security.