What are takedowns?
Takedown services remove online threats that misuse your brand or put your customers at risk. This can include phishing websites designed to mimic your brand, fake social media profiles impersonating your company, or counterfeit mobile apps published in app stores.
Threat actors create these assets to deceive customers, steal sensitive information, or damage your brand’s reputation. By identifying and removing them quickly, NordStellar helps you reduce the risk of fraud, protect your audience, and maintain trust in your brand.
How takedowns help you improve your brand security
Online threats don’t just exist in the background—they erode customer trust, open the door to fraud, and put sensitive data at risk. The longer malicious content stays online, the greater the damage to your brand and reputation. Takedowns remove these threats at the source, cutting off attackers’ ability to exploit your name or assets.
Common risks include:
Phishing and fake websites
Deceive customers into sharing credentials, payment data, or other sensitive information.
Fake mobile applications
Distribute malware or harvest user data under the guise of a legitimate app.
Fraudulent social media profiles
Impersonate your brand to mislead audiences and promote scams.
VIP impersonation accounts
Target executives and high-profile staff to increase credibility and reach.
How NordStellar's takedown process works
Detect & review
Continuous scanning across the web, social platforms, and app stores. Monthly findings are delivered with periodic reports; critical issues are escalated immediately.
Validate & collect evidence
We confirm impersonation or abuse and compile proofs (URLs, screenshots, WHOIS/headers, policy grounds) to support removal.
Submit takedown requests
We file with registrars/hosts, social platforms, app stores, and search engines using the appropriate legal or abuse paths.
Remove & enforce
Providers review and remove/disable the content. We track status, follow up, and escalate if needed.
Confirm & report
You receive confirmation and a summary in your scheduled report, plus ongoing re‑upload monitoring.
Key solutions for brand protection
Web detection & domain takedown
Identify and remove phishing sites, lookalike domains, and other malicious web assets that misuse your brand or target your customers.
Social media takedown
Eliminate fake accounts, pages, and posts on Facebook, Instagram, X (Twitter), LinkedIn, etc., that impersonate your company, spread false information, or promote scams.
App store takedown
Remove counterfeit or malicious mobile apps from official app stores like Google Play and Apple App Store to protect users from fraud, malware, or data theft.
Why choose NordStellar for takedowns
Faster threat removal
We validate issues quickly and file with hosts, registrars, app stores, and social platforms using the right abuse channels and follow-ups.
Reduced fraud & reputational risk
Removing phishing sites, fake accounts, and rogue apps limits customer harm and protects your brand’s credibility.
Coverage across web, social & app stores
One service to address impersonation and abuse wherever it appears.
Lower operational workload
We handle detection, evidence collection, submissions, tracking, and escalation. Your team reviews clear summaries and outcomes.
Clear, scheduled reporting
Receive monthly reports with actions taken, current status, and next steps.
Executive & brand impersonation control
Take down VIP impersonation accounts and brand abuse that attackers use to mislead customers.
Evidence for audits & investigations
Each takedown includes documented proofs and a traceable record to support compliance and incident response.
Ongoing re-appearance monitoring
We watch for re-uploads and repeat offenders, helping you keep threats offline.
Explore more security solutions from NordStellar
NordStellar lets your cybersecurity team intervene at the earliest stages of an attack before any real damage is done.
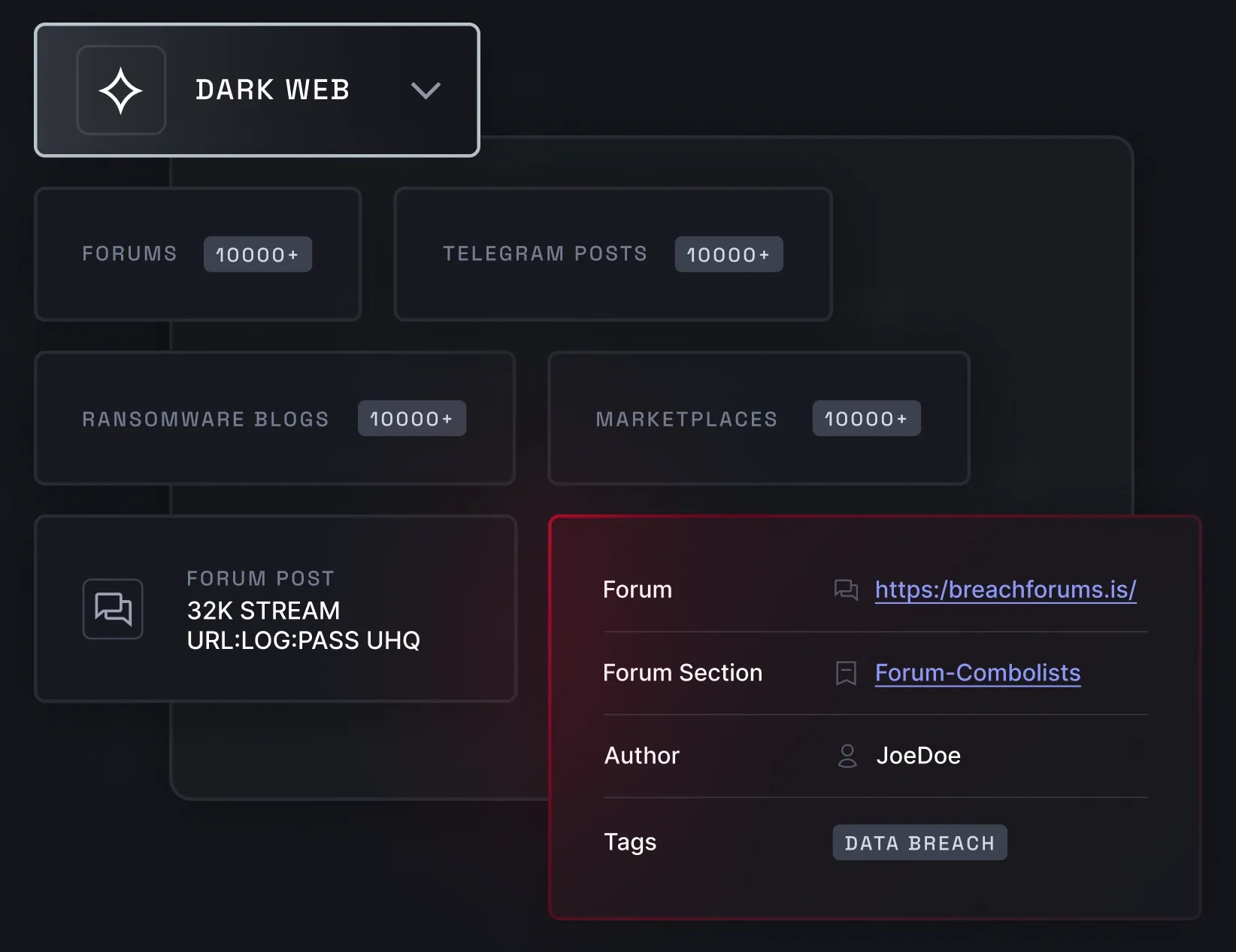
Dark web monitoring
Dark web monitoring allows you to track all keywords associated with your business across deep and dark web communities, such as hacker forums, illicit marketplaces, and Telegram channels. It helps you uncover brand mentions, issues with vendors, and leaked information about your VIP personnel.
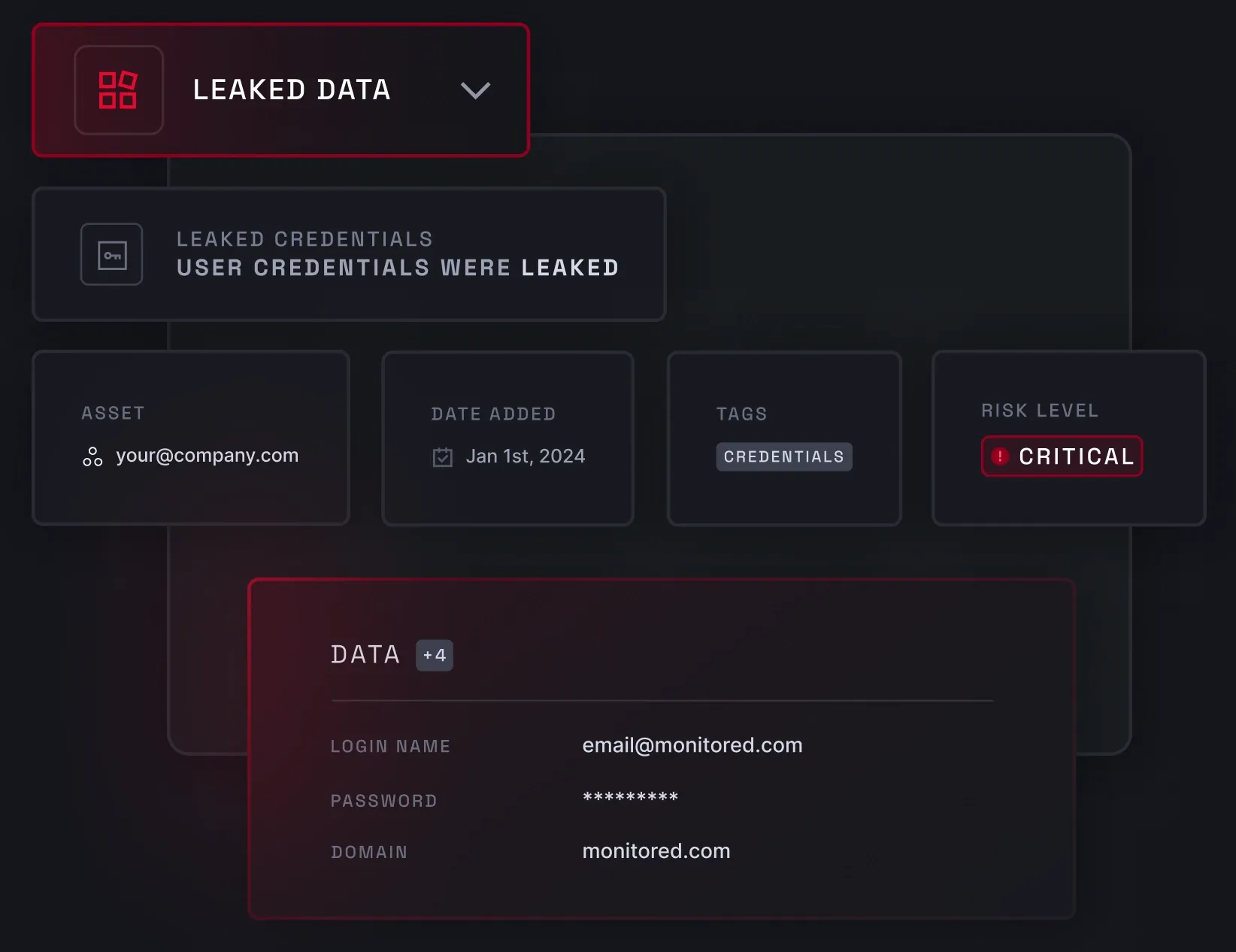
Data breach monitoring
Data breach monitoring involves scanning the deep and dark web for leaked sensitive information linked to your business. To spot breached data, NordStellar checks infostealer malware logs, leaked databases, and collections of stolen credentials combinations. This solution provides real-time monitoring and the full context of past and present attacks.
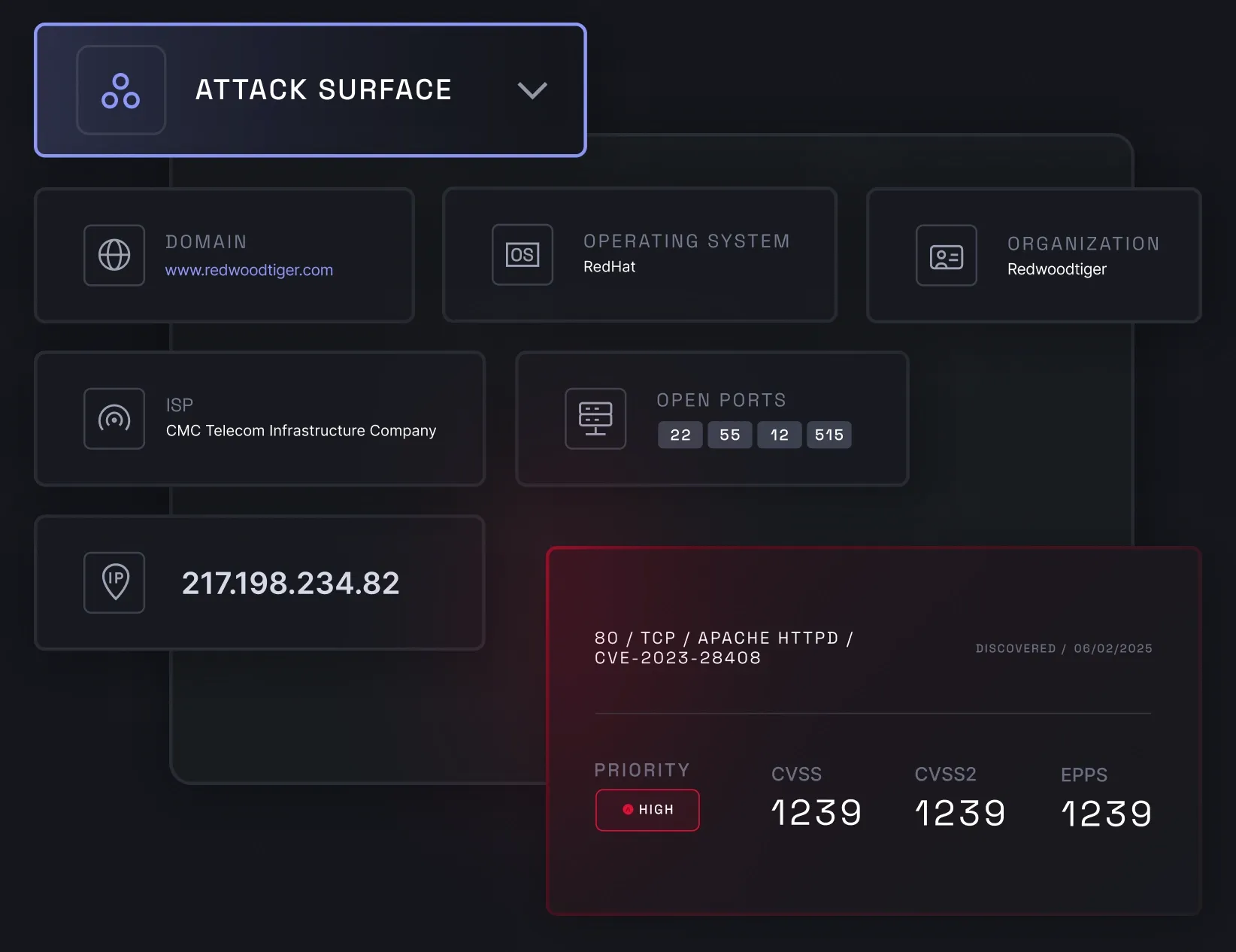
Attack surface management
Attack surface management (ASM) helps you monitor your business's external attack surface to prevent potential cyber risks. It lets you efficiently manage your company's internet-facing assets, such as IP addresses with open ports and outdated technologies, by identifying vulnerabilities and security gaps within them.
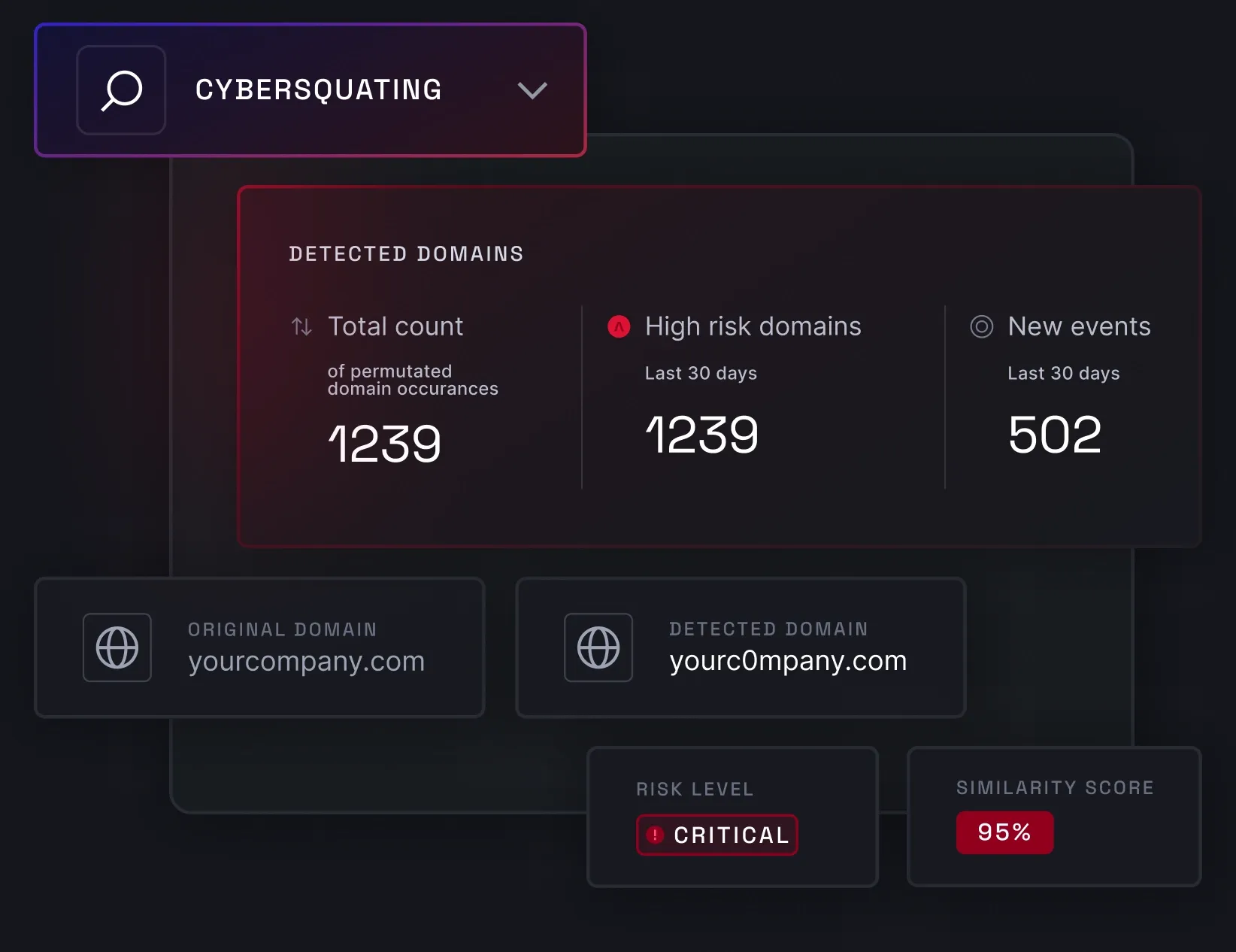
Cybersquatting detection
Cybersquatting detection helps you recognize and prevent threat actors from impersonating your brand. Using content and visual similarity algorithms enriched with AI, NordStellar can detect various domain manipulations and issue real-time alerts, providing a detailed view of each suspicious domain.
FAQ
The verification process typically includes confirming impersonation or abuse, capturing evidence (such as URLs and screenshots), and collecting necessary technical details (e.g., WHOIS/DNS or account/app IDs). This verification ensures we act on genuine threats and choose the fastest, most effective takedown path.
Both. We combine automated monitoring with expert review and action.
Automation: continuous scanning (web, social, app stores), data enrichment (WHOIS/DNS, account IDs), risk scoring, pre-filled submissions, status tracking, and monthly reporting.
Human expertise: verify impersonation/abuse, assemble evidence, select the fastest removal channel, tailor submissions to platform policies, handle follow-ups/appeals, and escalate unresponsive hosts.
This mix delivers speed from automation and accuracy from analysts, reducing false positives and improving takedown success rates.
We ensure compliance by acting only under your authorization, verifying brand ownership, and grounding every request in the correct legal and platform policies. We follow each provider’s notice-and-takedown procedures, submit only necessary evidence, protect personal data, and keep a clear audit trail of actions and outcomes. Complex cases are reviewed by specialists and coordinated with your legal team when needed to avoid overreach.
Threat monitoring provides visibility — detecting and reporting risks like phishing domains, fake accounts, or rogue apps so your team knows what’s out there. Takedown services act on those findings — verifying abuse, filing with hosts/platforms, and following through until the malicious content is removed (with re-appearance checks). In short: monitoring shows the problem; takedowns remove it.