What is threat exposure management?
Threat exposure management (TEM) is the practice of identifying, assessing, and mitigating risks in the IT space of your organization. TEM is a critical component of modern cybersecurity strategies, helping your business determine where to invest resources to efficiently protect its corporate assets.
By offering continuous threat exposure management, NordStellar makes sure that your security teams are ready to fend off attacks at any time. In the long run, you will find that preventing cyber threats from materializing is more effective than containing an attack in progress or dealing with the aftermath.
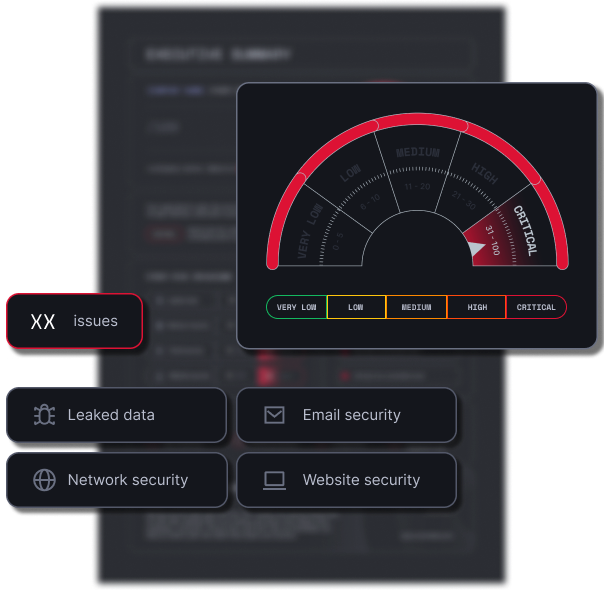
Curious about your company’s security posture?
Start with a free Risk Report from NordStellar — your first look into the threat landscape we help security teams navigate and stay ahead of.
What’s inside:
- Your personalized Cyber Risk Score
- Key insights across leaked data, email, web, and network security
- A snapshot of exposed or compromised data linked to your domain
Key elements of threat exposure management
While different TEM platforms use different tools to manage threat exposure, they all incorporate the following elements in some way to protect organizations against cyberattacks.
Effective TEM solutions check for threats constantly, using automated tools to monitor vulnerable areas in real time. By detecting threats early, TEM can stop cyberattacks before they escalate.
Very few organizations can make unlimited security investments, so TEM solutions must identify the biggest dangers facing an organization given its business practices and policies.
After identifying the potential risks, TEM solutions implement security measures (if necessary, changing the organization’s security posture) to minimize the organization’s attack surface.
TEM solutions process the data and present the results to your organization’s cybersecurity experts who will, in turn, communicate their conclusions to the appropriate decision makers.
Explore NordStellar’s security solutions
NordStellar lets your cybersecurity team patch critical vulnerabilities and intervene at the earliest stages of an attack – before any real damage is done.

Dark web monitoring allows you to track all keywords associated with your business across deep and dark web communities, such as hacker forums, illicit marketplaces, and Telegram channels. It helps you uncover brand mentions, issues with vendors, and leaked information about your VIP personnel.

Data breach monitoring involves scanning the deep and dark web for leaked sensitive information linked to your business. To spot breached data, NordStellar checks infostealer malware logs, leaked databases, and collections of stolen credentials combinations. This solution provides real-time monitoring and the full context of past and present attacks.

Attack surface management (ASM) helps you monitor your business's external attack surface to prevent potential cyber risks. It lets you efficiently manage your company's internet-facing assets, such as IP addresses with open ports and outdated technologies, by identifying vulnerabilities and security gaps within them.

Cybersquatting detection helps you recognize and prevent threat actors from impersonating your brand. Using content and visual similarity algorithms enriched with AI, NordStellar can detect various domain manipulations and issue real-time alerts, providing a detailed view of each suspicious domain.
The benefits of threat exposure management
Threat exposure management lets you see your organization through hackers’ eyes — and prepare accordingly. With NordStellar at your side, you will know what attackers are likely to target and how you can foil them.
EMPLOYEE & CONSUMER PROTECTION
Identify and mitigate risks from compromised employee and consumer data (including leaked or stolen credentials) with real-time monitoring and alerts.
COMPANY & BRAND PROTECTION
Track keywords related to your company across dark web forums, cybercrime communities, and Telegram channels to stay ahead of threats targeting your business.
INFRASTRUCTURE PROTECTION
Use automated asset discovery to map your infrastructure (such as IP addresses, open ports and outdated technologies) and employ real-time vulnerability detection to close security gaps.
REPUTATION PROTECTION
Detect malicious domain registrations seeking to impersonate your brand or targeting your customers to identify threats early and take proactive steps to protect yourself.
FAQ
NordStellar is a threat exposure management platform designed by renowned cybersecurity experts. NordStellar offers continuous threat exposure management, allowing organizations to respond to new challenges quickly and efficiently. With access to one of the largest dark web data pools in the industry for up-to-date threat intelligence, active attack surface monitoring, and domain squatting protection, NordStellar gives you the solutions you need to keep yourself safe.
Threat exposure management works by identifying the external threats faced by an organization and adopting security measures to reduce them. To do this, TEM platforms must be able to observe the business’s attack surface, determine which vulnerabilities to prioritize, and offer effective solutions to the most pressing problems.
For example, NordStellar continuously scans the deep web and the dark web for keywords associated with your business, hunting for undiscovered data leaks and potential attack discussions. Dark web monitoring gives your business advance warning of these events, letting you take early action in accordance with your organization’s security policies to minimize the damage. Furthermore, any data breach discovered can be thoroughly analyzed to prevent similar incidents in the future.
All organizations benefit from effective threat exposure management because, in the long run, prevention is a much more effective strategy than damage control. And as organizations grow in size, so do their attack surfaces — the potential threats grow exponentially as you add new employees, devices, and networks to your business structure.
The best threat exposure management solution must be able to perform continuous monitoring against developing threats. Your business’s attack surface shifts with each new asset you incorporate into your IT infrastructure, so yesterday’s assessment might not be sufficient to prepare for tomorrow’s problems.
NordStellar offers automated continuous monitoring solutions to let you see threats in real time. Drawing upon the experience of the people that created NordVPN and having access to one of the largest dark web data pools in the industry, NordStellar can help you see your business through hackers’ eyes — and protect it from their actions through proper security controls.
