Summary: Combolists are collections of stolen credentials pulled from multiple breaches and used for automated attacks. Learn how to neutralize them with proactive dark web monitoring.
A combolist is a core tool in a cybercriminal's arsenal. It's a collection of leaked email and password pairs gathered from multiple data breaches. These simple yet effective datasets are used to fuel automated attacks, such as credential stuffing and account takeovers.
The scale of the problem is staggering. According to our data, in just three quarters of 2025, we identified 13.6 billion email and password pairs, along with 29.7 billion passwords associated with these emails. That's 2.18 passwords for every single email address. It's statistical proof that password reuse is the exact vulnerability that attackers exploit.
But what exactly is a combolist? Where do attackers get them? And how do you stop them from being used to breach your business? Let’s find out.
Key takeaways
A combolist is a file containing usernames and passwords stolen from multiple data breaches.
Attackers use combolists for credential stuffing, brute-force attempts, and social engineering to gain unauthorized access to user accounts across various platforms.
Combolists are traded and shared on dark web markets, hacking forums, and Telegram channels.
The main risk for businesses comes from employees reusing passwords across many services.
Strong password policies, MFA, and dark web monitoring are the most effective defenses against automated attacks.
What is a combolist?
A combolist (also known as a combo list) is a massive, compiled database of usernames, email addresses, and corresponding passwords, all aggregated from multiple data breaches. Attackers collate this stolen data into a simple text file. The format is simple and effective: [email protected]: password.
The danger of combolists stems from a single human error: password reuse. A password stolen from a low-security gaming forum may be the exact same one used to protect a corporate email account.
Attackers exploit this vulnerability by feeding combolists into automated software for credential stuffing. These tools systematically test leaked login pairs against new targets, waiting for a match.
These lists vary in scope:
A mixed combolist pulls credentials from various sources and regions.
An international combolist contains data from many countries, making it ideal for broad, non-targeted attacks.
While possessing or distributing these lists is illegal, they remain a staple of the cybercrime economy. Their value is determined by freshness. A list with "new" credentials—passwords that have not yet been reset—is considered far more potent and commands a higher price.
Common combolists examples
The scale of these compiled lists can be massive, showing the extent of exposed credentials:
Collection #1-5: A well-known combolist released in 2019. It held over 770 million unique email addresses and 21 million unique passwords.
Exploit.in: A massive combolist that circulated on Russian-speaking hacking forums, containing hundreds of millions of credentials.
Anti-public combolist: A large compilation of over 1.3 billion credentials collected from numerous "public" leaks into a more effective list.
COMB (Compilation of many breaches): Considered one of the largest combolists ever. When it was leaked in 2021, it reportedly contained over 3.2 billion unique email and password pairs.
Our data also confirms that the pool of compromised credentials available to hackers is massive. The volume of newly exposed data is growing rapidly, with the number of emails and passwords collected in Q3 2025 being more than double that of Q1. This trend confirms that the threat related to combo lists continues to increase.
The rise of ULP combolists
While older combolists relied on a simple "email: password" format, the market has now shifted toward "ULP" (URL: login: password) lists. This format became a dominant trend in 2025 as infostealer-based attacks increased significantly.
Because infostealers capture the specific website address alongside the credentials, ULP lists tell attackers exactly which website to target. This precision saves them time compared to traditional lists, making credential stuffing attacks faster and more dangerous.
How combolists are created and distributed
Combo lists don't appear from thin air. They are the end product of a long supply chain of cybercrime. While data breaches are a common source, the rapid growth of these lists is now fueled by infostealer malware.
Creation
Data breaches: This is the most common source. Attackers breach a website's database and steal its entire user list.
Infostealer malware: This is a key driver for "fresh" credentials. Malicious software infects a victim's device and steals saved passwords, cookies, and other data.
Phishing attacks: Attackers lure victims to fake login pages to trick them into entering their credentials directly.
Social engineering: This involves tricking individuals into revealing their login information.
Distribution
Once a combolist is created, it's shared through various underground channels.
Shared freely: Lists are often shared for free on Telegram channels and hacking forums. This is often done to build a reputation within the cybercrime community.
Related articles

Joanna KrysińskaMar 5, 202514 min read

Agnė SrėbaliūtėSep 18, 20258 min read
How threat actors use combolists
Attackers use combolists for a wide range of attacks, from automated brute-force attacks to highly targeted strikes, such as phishing or identity theft.
Credential-based attacks
This is the most common use for a combolist.
Credential stuffing: An automated attack where software "stuffs" millions of email-password pairs from a combolist into the login forms of different websites, like banks, e-commerce sites, or corporate networks. Attackers are betting you reused your password.
Brute-force attack: Using password lists (including combolists) as a “dictionary”, a tool that systematically guesses passwords against a single account until it finds a match.
Password spraying: A variation where an attacker tries a single, common password (or one from a combolist) against many different accounts, hoping for a single hit.
Account takeover (ATO): This is the ultimate goal. By finding a working credential pair, the attacker gains complete, unauthorized control of a user's account.
Phishing and social engineering attacks
Beyond simply gaining access, combolists enable secondary attacks, such as mass phishing and social engineering attacks. The email addresses are an especially valuable resource for these attacks. Threat actors are aware that these users have already been compromised elsewhere, making them prime targets for additional social engineering attacks.
Ransomware attacks
Combolists are often a key part of the initial access phase for major cyber-attacks. Ransomware groups use them to find a single valid credential for a corporate VPN or Remote Desktop Protocol (RDP) account.
This one "foot in the door" is all they need. From there, they can infiltrate the network and eventually deploy their payload. Some may even use a Ransomware-as-a-Service (RaaS) kit purchased on the dark web.
For example, analyzing how the Akira ransomware group works often reveals that its initial access brokers rely on purchasing compromised credentials—credentials that are frequently sourced from combolists and infostealer logs.
How to mitigate risks from combolists
The threat from combolists is not just persistent; it's accelerating. Our research shows the password-to-email ratio in leaked data jumped from 1.39 in 2024 to 2.18 in 2025.
This clearly shows that the core vulnerability—password reuse—remains a growing problem. While the sheer volume of breached data fluctuates, the danger of that data is increasing. For businesses, this means the risk is external, evolving. Here is how you can mitigate these threats:
Implement a strong password policy
Mandate that employees use complex and, most importantly, unique passwords for every service. A credential from a combolist is useless if that password was only ever used on one breached, low-value site.
Deploy a password manager
A strong password policy is only practical with a password manager. Encourage or provide a corporate password manager, like NordPass, to help employees generate and store unique passwords for all their accounts.
Enforce multi-factor authentication (MFA)
MFA is the single most effective defense against credential-based attacks. Even if an attacker has a valid username and password from a combolist, they can’t log in without the second factor, for example, a code from an authentication app or a physical key.
Activate dark web monitoring
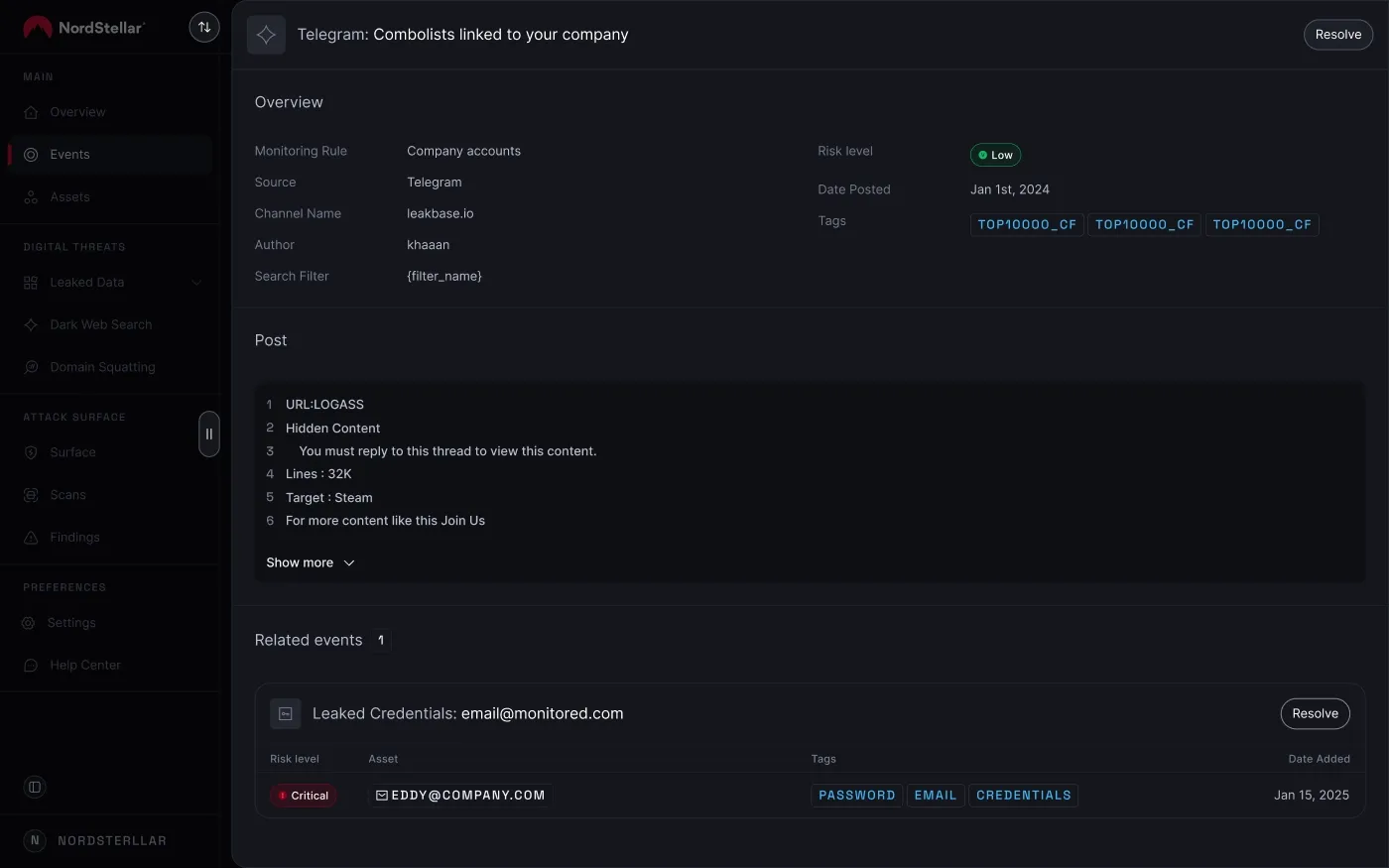
Since you can't stop your employees' data from appearing on combolists, the next best thing is to know when it happens. Proactive dark web monitoring scans the dark web for your company's domains, keywords, and credentials.
How NordStellar can help
NordStellar’s threat intelligence platform gives you direct visibility into the combolist threat.
Our continuous dark web monitoring scans the hidden forums, Telegram groups, and illicit marketplaces where combolists are traded. When credentials linked to your employees or customers appear in one of these lists, NordStellar sends an immediate alert.
This allows your security team to take action—such as forcing a password reset—before that leaked login information can be used in a credential stuffing attack, preventing an account takeover or network breach.
See what hackers already know. NordStellar provides continuous monitoring for leaked credentials from combolists and other breaches. Request your free trial today to see your company's exposure.
FAQ
What is a ULP file?
"ULP" stands for "User, Login, Password." It is essentially another name for a combolist, a file structured with user login details, typically in a user: password format.
What is an infostealer log?
An infostealer log is the complete data packet stolen by infostealer malware from a single infected device. It is much more comprehensive than a combolist entry and can include not just passwords but also session cookies, system information, cryptocurrency wallets, and browsing history.
What is the difference between a combolist, a ULP file, and an infostealer log?
Combolist / ULP File: These terms are interchangeable. They refer to a compiled list of username: password pairs, often aggregated from many different breaches and logs.
Infostealer Log: This is the raw data stolen from a single infected computer. Combolists are often created by processing, parsing, and compiling credentials from thousands of individual infostealer logs.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she loves explaining complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.