NordStellar
Cybersecurity
Cybercrime-as-a-service: the business model behind digital attacks

Summary: Cybercrime-as-a-service mirrors the SaaS model, selling attack tools on the dark web. Learn how it works and how to defend your business.
Cybercrime-as-a-service (CaaS) is the dark side of modern software development. While the SaaS business model offers low-cost and flexible solutions, CaaS provides similar benefits for cybercriminals.
Thanks to CaaS, executing data breaches or distributed denial-of-service attacks has never been easier, challenging companies to upgrade their security measures. This article will explain how CaaS works and who is behind it, before exploring practical security responses.
What is cybercrime-as-a-service (CaaS)
Cybercrime-as-a-service is a threat model in which vendors provide services or tools to enable attacks by third-party clients. CaaS vendors generally sell products via pay-per-use or subscription models and use dark web marketplaces to conceal transactions.
CaaS operations allow attacks by unskilled criminal groups, expanding the community of threat actors. They cover many cyber threats, including ransomware, DDoS attacks, and credential theft. This makes cybercrime-as-a-service a critical part of the global threat landscape.
How the service model works in cybercrime
Cybercrime-as-a-service (CaaS) functions similarly to conventional third-party applications or cloud services. This familiarity is one reason why CaaS is spreading rapidly. Once restricted to specialist hackers, advanced tools are now available to novice threat actors.
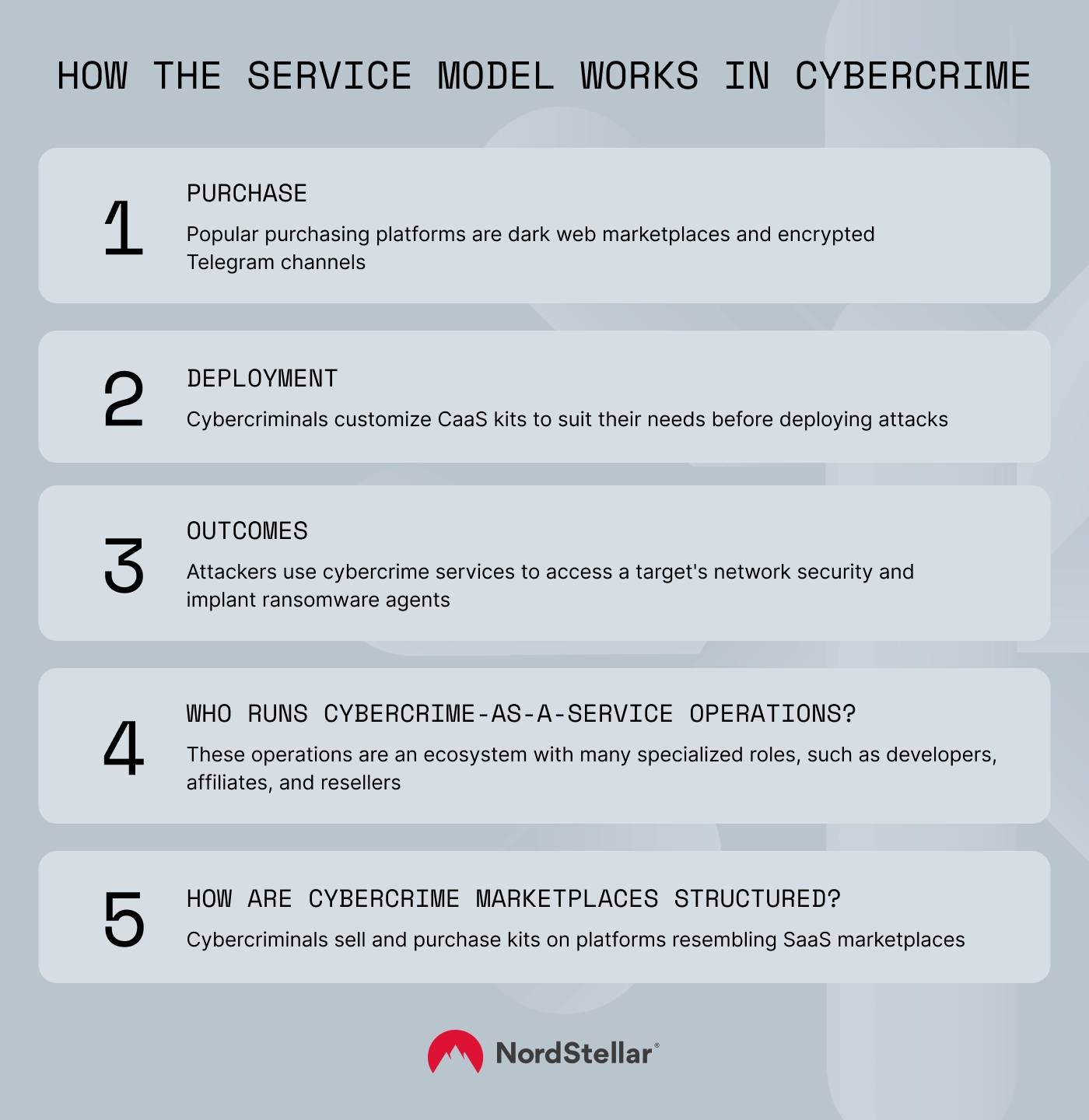
CaaS attacks follow a lifecycle that starts with purchasing and ends with successful cyber attacks:
Purchase
Vendors create kits that include the tools needed to mount cyber-attacks. They offer these products for sale via encrypted sites. Popular purchasing platforms include dark web marketplaces and encrypted communication tools like Telegram channels.
Buyers can choose between several different kits depending on their goals and budget. CaaS vendors typically offer ransomware-as-a-service kits, tools to spread malware, and phishing kits featuring templates for fake websites and login portals.
Purchases typically take place via hard-to-trace cryptocurrencies. Transactions could be one-off purchases, but subscriptions are common. Marketplaces also often apply escrow models to enforce standards and resolve disputes.
Deployment
Cybercriminals customize CaaS kits to suit their needs before deploying attacks via their favored method. Forms of deployment include:
- Drive-by downloads: Cybercrime services create credible websites to deceive victims and deploy downloads containing malicious payloads.
- Phishing emails. Automated kits send personalized phishing emails to mount targeted attacks on victims. Emails persuade victims to download infected attachments, provide login credentials via fake websites, or take other risky actions.
- Malvertising. CaaS kits deploy fake ads that are infected with malicious software. Malware spreads as users visit websites hosting the ads, enabling secondary data theft or ransomware attacks.
In the above deployment methods, off-the-shelf kits do the technical work (bypassing encryption, anonymizing attackers, or creating convincing fake assets).
CaaS kits also implant malicious tools on target systems. They seek ways to achieve lateral movement and discover sensitive data, often deploying credential theft tools to expand their reach. Backdoors also enable unskilled attackers to achieve persistence and execute sophisticated attacks.
Outcomes
After deploying threats and achieving persistence, cybercriminals can launch many types of cyberattacks.
For example, criminals use cybercrime services for gaining access to a target's network security and implanting ransomware agents. These agents encrypt sensitive data or infrastructure until victims pay a ransom.
CaaS can also enable distributed denial-of-service (DDoS) attacks against network systems. Cybercriminals can extract data from cloud databases, use stolen financial credentials to make illicit transfers, or launch crypto-jacking attacks.
Who runs cybercrime-as-a-service operations?
Security experts estimate that cybercrime-as-a-service vendors earn over $23 billion annually, with an annual growth rate of over 12 percent. The market is increasingly complex, creating an ecosystem with many specialized roles.
Developers handle the production aspect of CaaS. For example, developers might create and update malware to stay ahead of cybersecurity measures. Other development teams focus on building botnets or exploit kits to target recently discovered vulnerabilities.
Affiliates tend to handle marketing and sales for developers. Marketers advertise CaaS products on the dark web and Telegram, along with prices and payment plans. Affiliates often earn commissions from successful attacks (sometimes as high as 30 percent).
Resellers operate independently from developers and affiliates. They sell products directly to customers, often those with less tech knowledge or awareness of the cybercrime landscape. Resellers may combine CaaS sales with tech support to attract buyers. They also buy in bulk and resell subscriptions at significant discounts.
Where does that leave the customers who actually purchase off-the-shelf CaaS products? Many buyers are new entrants to the cybercrime ecosystem. So-called "script kiddies" with few skills use CaaS kits to launch previously inaccessible attacks.
However, organized cybercriminals also rely on CaaS products to expand their operations. These criminals act like conventional businesses, seeking ways to cut costs and maximize revenues.
How are cybercrime marketplaces structured?
Cybercrime-as-a-service has developed into a sophisticated market with corporate actors and a diverse customer base. Cybercriminals sell and purchase kits on platforms closely resembling SaaS marketplaces, offering similar tools to inform and serve buyers.
For instance, CaaS marketplaces feature a UI for browsing products and prices, with admins overseeing activities to ensure consistency and remove scammers. Admins vet sellers before they can list, while customer feedback generates trust ratings for every vendor.
Like SaaS marketplaces, CaaS platforms have strict terms of service. Breaches result in eviction and permanent bans. As mentioned earlier, escrow systems provide reassurance for buyers and vendors alike.
Markets also provide customer support to resolve disputes or enable smooth payments. Some provide tutorials for buyers (for example, using stolen credentials to gain network access).
Unlike traditional SaaS marketplaces, platforms may be inaccessible without an invite. CaaS vendors operate in the dark web, and trading may require Tor browsers. Cryptocurrency is also standard, and often the only available payment method.
Why cybercrime-as-a-service poses a real risk to businesses
The rise of cybercrime-as-a-service markets is impressive. Underground markets are also extremely harmful to large and small enterprises.
Most significantly, CaaS has changed the rules of the game for cybercriminals. Attacks that once required experienced hackers and expensive tools are now available at discounted prices to unskilled actors.
CaaS users also impact operations in many ways.
Ransomware attacks lead to costly ransoms and put data at risk. Malware steals login credentials and enables network-wide attacks. Infiltrators access sensitive data and expose customer records, while DDoS attacks result in operational downtime, compromising website availability.
Key services available in the cybercrime-as-a-service model
Another aspect of CaaS that worries enterprise cybersecurity specialists is the ability to combine multiple attack techniques. CaaS kits are highly flexible and could include:
- Ransomware-as-a-service: Developers lease ransomware tools to attackers who can use them to encrypt target systems and demand ransom payments.
- Phishing kits and phishing-as-a-service: Products allow users to create fake websites and convincing emails, with the ability to send messages in bulk while using personalized information.
- Infostealer kits: Infostealer malware extracts login credentials, credit card data, and other sensitive information.
- Malware-as-a-service: Attackers can rent specialist malware, including malvertising tools, spyware, keyloggers, and trojans.
- DDoS-for-hire: Buyers rent botnet capacity for single or multiple denial-of-service attacks that take down targeted infrastructure.
- Botnets-as-a-service: Vendors sell botnet capacity for DDoS, surveillance, spamming, or cryptojacking. Botnets come with command and control tools to manage large-scale attacks.
- Hacking-as-a-service: Vendors provide the tools to infiltrate specific targets. HaaS often functions on a results-based model, with payments when attacks succeed.
What signs suggest your business is being targeted
The effects of CaaS attacks are severe. Companies can lose control of assets, suffer data breaches, or be overwhelmed by malicious traffic. Understanding the symptoms of CaaS attacks is critical to protect data and respond effectively.
Use the following checklist to determine whether a CaaS attack is imminent:
- Leaked credentials: If your user or employee data is available on dark web marketplaces, an attack could be underway.
- Credential stuffing attacks: In the early stages, attackers assault login portals before gaining access. Check for spikes in failed login attempts across multiple user accounts.
- Unusual logins: Security systems detect logins at strange times or unusual locations, while device posture checks identify unapproved devices.
- API anomalies: Cloud APIs experience a spike in unauthorized API calls, while attackers make unrequested changes to cloud deployments.
- Targeted phishing: Employees receive unexpected surges in emails from clients or colleagues. They may report unusual numbers of approval notifications, or suspicious SMS messages.
- Dark web chatter: Sophisticated threat management tools like NordStellar monitor discussions on dark web forums. Regular mentions of your business often indicate an attack is in progress.
Defensive strategies against cybercrime-as-a-service
Companies are not powerless in the fight against cybercriminals, but you need streamlined plans for threat detection, prevention, and response.
- Monitor the dark web for potential threats. CaaS attacks originate in the shadows. Cyber threat intelligence solutions monitor the dark web for leaked data and mentions of your business, giving you prior warning about possible attacks.
- Strengthen your endpoint security. CaaS attacks target vulnerable endpoints. Protect endpoints with robust access controls (MFA, device posture security, strong password policies). Implement next-generation firewalls (NGFWs) to monitor traffic and detect suspicious content.
- Update employee training. CaaS attacks often rely on phishing to access networks and deploy malware. You can prevent many attacks by training staff to identify malicious emails, voice calls, or SMS messages.
- Simulate CaaS incidents. Workshop on cyberattacks to ensure you are well-placed to respond. Remember that CaaS can involve multiple threats. Simulate ransomware, DDoS, and phishing attacks simultaneously.
- Protect network assets with Zero Trust controls. Prevent lateral movement within the network by applying network segmentation. Implement access controls based on Zero Trust principles. Only allow access to users with a legitimate business need, and block everyone else by default.
Final thoughts
Cybercrime is now a corporate venture. Hackers develop and distribute tools like conventional SaaS vendors, while threat actors are organized, efficient, and capable of large-scale campaigns. Moreover, thanks to CaaS marketplaces, advanced skills are no longer required.
The rise of CaaS has made the threat landscape even more hazardous. Companies need a strategic and layered approach combining dark web monitoring with effective defensive measures to defend network assets.
Many businesses will need sustained investment to overhaul their defenses. NordStellar can help you make the right investments and achieve your security aims. Contact our team to discuss threat management solutions that counter CaaS threats.








