Summary: Infostealer malware steals sensitive data, such as login credentials or banking details, from devices, leading to data breaches, financial loss, and unauthorized access.
Infostealer malware is a major cybersecurity risk. This threat can bypass the security features in a standard browser, leaving your business vulnerable to attacks. Relying solely on built-in browser security is not enough to prevent data breaches, financial loss, or reputational damage.
Recent industry data confirms the growing danger. IBM's 2025 X-Force Threat Intelligence Index reports a significant surge in this tactic, with an 84% increase in emails delivering infostealer malware. The report also highlights that 30% of intrusions now involve using valid credentials.
Understanding how infostealers work is the first step toward effective protection. Let’s look at how they operate and what you can do to prevent an attack.
What is infostealer malware?
Infostealer malware is a type of malicious software designed to steal sensitive information from infected devices. Cybercriminals, particularly initial access brokers (IABs), use it to collect passwords, banking details, personal files, and other private data, which they can sell to other threat actors, use for fraud, or exploit in further attacks.
Once deployed, the infostealer malware communicates with a command and control (C2) server, which allows attackers to exfiltrate data stolen from the compromised device and issue further commands. IABs often leverage infostealers to gain unauthorized entry into corporate networks, then either provide the stolen data to ransomware groups or sell access to other cybercriminals.
Initial access brokers spread infostealer malware through phishing emails, fake downloads, or malicious websites. Some advanced versions can even adapt their tactics based on the system they infect, making them harder to detect. Because they operate so quietly, infostealers pose a serious risk. A single infection can lead to identity theft, financial loss, or unauthorized access to critical systems.
The history of infostealer malware
Infostealer malware has been around for nearly two decades, evolving alongside the internet and online threats. It emerged in 2007 with Zeus (also called Zbot), a powerful Trojan designed to steal online banking credentials. The malware became a massive threat. When its source code leaked in 2011, hackers swiftly copied and modified it, creating a wave of new infostealers.
By 2008, infostealers began targeting more than just banking information. Koobface, another early infostealer, targeted the login credentials of social media users on platforms like Facebook, Twitter, MySpace, and email services like Gmail. It spread by hijacking social media accounts and tricking users' friends or connections into clicking suspicious links.
Today, infostealers are more advanced and operate within a sophisticated malware-as-a-service (MaaS) ecosystem. Many modern botnets, which are large networks of infected computers, possess infostealing capabilities, even if their main purpose is different. These threats now go beyond stealing banking information and social media credentials, which puts both individuals and businesses at risk, making infostealers a critical concern for enterprise cybersecurity.
What information does infostealer malware collect?
Once inside a device, infostealer malware gathers a wide range of information, including:
Login credentials and session cookies.
Application credentials and metadata.
Financial information.
Personally identifiable information (PII).
Browser fingerprints.
Device information.
Private browsing data.
Personal files.
File Transfer Protocol (FTP) information.
Login credentials and session cookies
Infostealers target login information, such as emails and passwords, VPN credentials, and session cookies—small files that keep users logged in to websites and online services. Cybercriminals use session cookies to hijack personal and corporate accounts and gain unauthorized access to email, banking, social media, and other sensitive platforms, all without needing a password or two-factor authentication (2FA).
Application credentials and metadata
Infostealers don't just target browser-based credentials. They also steal data stored by applications directly on a user's device. Popular targets include platforms like Steam, Discord, and Telegram, which store login credentials, authentication tokens, and metadata in specific directories rather than session cookies. Attackers can extract details such as stored accounts, user settings, login history, and even metadata like the number of games owned on Steam.
Financial information
Many users store financial information, such as credit card details, banking credentials, and cryptocurrency wallet data, in their browsers for convenience. Infostealers can extract this data and give hackers access to bank accounts, online payment services, and cryptocurrency wallets. Access to this information can lead to significant financial loss.
Personally identifiable information (PII)
Personally identifiable information (PII), such as Social Security numbers and addresses, is often a key target for identity theft. Criminals use it to impersonate victims, apply for loans, open fraudulent accounts, or commit other crimes. Stolen PII is highly valuable, which is why cybercriminals often sell it in bulk on hacker forums, marketplaces, and encrypted messaging platforms.
Browser fingerprints
Infostealers can collect unique browser details, known as fingerprints, including settings, installed browser extensions, and system configurations. Attackers use this data to mimic a victim's device, making their activities appear legitimate and helping them bypass security measures. Some cybercriminals use anti-detect browsers to replicate stolen browser fingerprints, which allows them to evade fraud detection and security checks.
Device information
Infostealers can gather details about your device, including information about its operating system and hardware. Attackers can use this data to identify vulnerabilities, making it easier for them to launch targeted attacks or exploit your system.
Private browsing data
Even when you use private browsing, infostealers can still track your session data and search history. Hackers can use this information to profile you and then target you with tailored phishing scams or other malicious attacks.
Personal files
Your personal files, such as documents, photos, and videos, are valuable not only to you but also to cybercriminals. Infostealers can steal these files and exploit them for blackmail, fraud, or identity theft.
File Transfer Protocol (FTP) information
If cybercriminals steal your File Transfer Protocol (FTP) credentials, they can gain access to your servers and take control of your website or network. They may steal or modify important files, upload malware, and disrupt your system.
What is a stealer log?
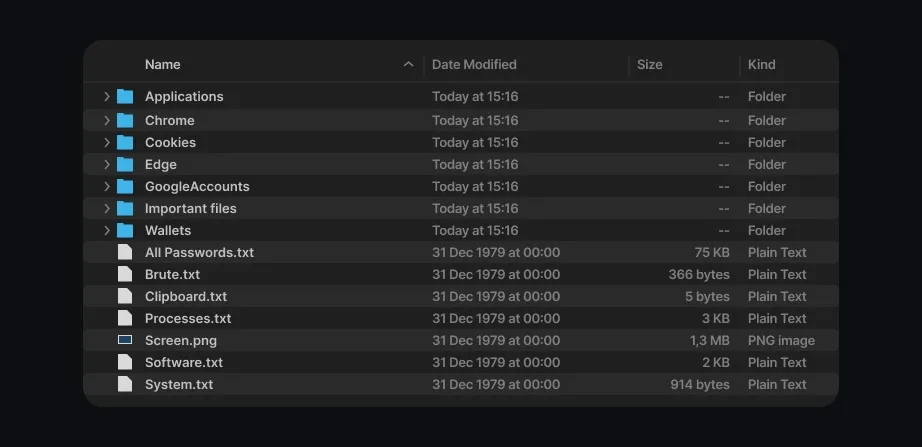
Once an infostealer collects data, it compiles everything into a stealer log, a file containing a detailed record of the victim's sensitive information. This log captures a complete snapshot of the victim's device, including saved passwords, browsing history, session cookies, and system details.
Cybercriminals distribute these logs on underground forums, marketplaces, and encrypted messaging platforms. Other hackers then use them for credential stuffing, financial fraud, cryptocurrency theft, or large-scale corporate breaches.
How does infostealer malware work?
We can break down how infostealer malware works into four stages:
Malware deployment
Data collection
Data exportation
Data distribution and exploitation
Stage 1: Malware deployment
The first stage is malware deployment. Initial access brokers distribute infostealer malware through:
Phishing emails.
Malicious websites.
Malvertising.
Infected software.
Fake updates.
Drive-by downloads.
USB drives.
Stage 2: Data collection
Once malware is deployed, the next stage is data collection. Common methods attackers use to collect data include:
Keylogging. The malware secretly records every keystroke typed on a keyboard. Hackers later filter this data to find passwords, credit card numbers, and private messages.
Browser session hijacking. Infostealers can steal session cookies from a browser, which allows attackers to log in to a victim's account without needing a password.
Credential dumping. Many users allow their browsers to save login credentials for convenience. Infostealers extract these saved credentials, sometimes decrypting them before sending the data to hackers.
Form grabbing. Infostealers intercept login credentials, payment details, and other sensitive information typed into web forms before encryption takes effect. This method is especially dangerous for online banking and shopping sites.
Email harvesting. Infostealers scan email inboxes and stored documents for email addresses. Cybercriminals use these addresses for phishing campaigns or sell them in bulk on the dark web.
Clipboard hijacking. Some malware monitors clipboard activity. If a user copies a password or a cryptocurrency wallet address, the malware can steal it or replace it with an address controlled by the hacker.
Crypto-wallet theft. Some infostealers search for cryptocurrency wallets stored on a computer. Once they locate wallet files or private keys, hackers can drain the victim's crypto holdings within seconds.
Screen capturing. Instead of extracting text, some malware takes screenshots of sensitive information while it's displayed on the screen. This method can capture bank account details, email content, and even 2FA codes that appear as images.
Man-in-the-browser attacks. Advanced infostealers inject malicious code into the browser, which allows hackers to modify payment details, alter transactions, or steal data in real time — all without the victim noticing.
Stage 3: Data exportation
Once infostealer malware collects sensitive information, the next step is to transmit it to the attacker's server. This can be done through various methods, including:
HTTP/HTTPS request.
FTP transfers.
Email.
Peer-to-peer (P2P) networks.
Cloud storage services.
The Tor network.
Remote desktop protocol (RDP).
Social media or messaging platforms.
Stage 4: Data distribution and exploitation
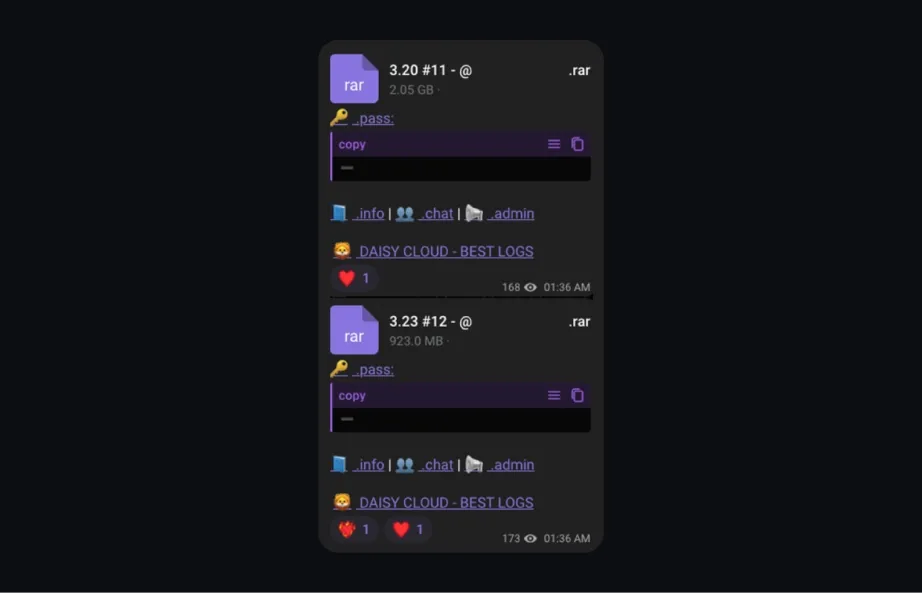
Once cybercriminals export stolen data, they quickly transfer it to centralized marketplaces or decentralized platforms. Centralized marketplaces, often found on the dark web, allow cybercriminals to sell logs individually. However, criminals rarely use dark web forums for log-selling.
Decentralized platforms, such as peer-to-peer networks like Telegram, are more popular because they offer greater anonymity and make transactions harder to trace. On these platforms, logs are often sold in bulk.
Once attackers have the data, they can use it for various malicious purposes, such as:
Identity theft.
Financial fraud.
Phishing attacks.
Ransomware attacks.
Sextortion or blackmail.
Families associated with infostealer malware
Infostealer malware comes in many forms, with hundreds—possibly thousands—of different strains. Some are well-known and widely studied, while others are designed to target specific individuals, industries, or regions.
Malware strains often work alongside other types of malware to maximize damage. These other types of malware include:
Downloaders and Trojan droppers. Some infostealers don't infect devices directly. Instead, they are delivered by a downloader or trojan dropper, often disguised as legitimate software.
Trojans. Many infostealers behave like trojans, tricking users into installing them by pretending to be useful software, game cracks, or pirated files.
Botnets. Cybercriminals use botnets to distribute infostealers, infecting and controlling thousands of compromised machines.
Keyloggers. While keyloggers can function as standalone malware, many infostealers include keylogging features to record passwords, payment details, and other sensitive information.
Infostealer malware examples
Infostealer malware has evolved over the years, adapting to security defenses and targeting different types of data. Some of the most infamous infostealers include:
SpyEye (2010). Developed as a rival to Zeus, SpyEye specialized in stealing financial data and featured form-grabbing and keylogging capabilities.
Tinba (2012). Also known as the Tiny Banker, Tinba was a lightweight yet highly effective malware that stole banking credentials and evaded detection due to its small size.
HawkEye (2013). Marketed initially as a keylogger, HawkEye expanded to steal email credentials, financial data, and system information. It was widely sold on hacking forums.
Agent Tesla (2014). Agent Tesla is a powerful infostealer and keylogger that can extract credentials from browsers, email clients, and VPN software. It remains active today.
CoreBot (2015). Initially developed as a simple infostealer, CoreBot quickly evolved into modular malware capable of stealing credentials, injecting malicious code, and executing additional payloads.
FormBook (2016). Known for its form-grabbing capabilities, FormBook targeted both businesses and individuals, stealing login credentials and other sensitive information.
Lokibot (2016). This widely distributed malware focused on stealing login credentials, payment data, and cryptocurrency wallet information. It was often delivered through phishing emails.
Arkei Stealer (2018). Arkei was designed to steal credentials, browser-stored data, and cryptocurrency wallets. It later became the foundation for other malware.
Raccoon Stealer (2019). Sold as a service on underground forums, Raccoon infostealer malware extracted passwords, cookies, and credit card data from infected devices. It was highly customizable, which allowed cybercriminals to adjust what it stole.
RedLine Stealer (2020). One of the most active infostealers today,
RedLine malware targets browser-stored passwords, cryptocurrency wallets, and autofill data. It commonly spreads through cracked software and malicious email attachments.
Vidar (2021). Based initially on Arkei, Vidar infostealer malware expanded to steal credentials, cookies, and financial data. It frequently delivers other malware as a second-stage attack.
Lumma Stealer (2022). Lumma Stealer operates as a malware-as-a-service (MaaS) and steals browser credentials, cryptocurrency wallets, and autofill data. Cybercriminals continually update it to bypass security tools.
Stealc (2023). A relatively new infostealer, Stealc is essentially a copycat of the Vidar and Raccoon infostealers. It steals browser credentials, session cookies, and cryptocurrency wallets while maintaining a low detection rate.
Related articles

Aurelija EinorytėJan 15, 20258 min read

Lukas TamašiūnasJan 20, 20255 min read
What dangers does infostealer malware pose?
Infostealer malware is a major threat, often used to steal sensitive information. Cybercriminals, particularly initial access brokers, deploy it to infiltrate systems and then sell access to other malicious actors or send data to ransomware groups.
Once inside compromised systems, attackers can steal sensitive data, leading to financial loss, identity theft, and severe security breaches. For businesses, the consequences go beyond stolen credentials, potentially resulting in regulatory penalties, operational disruptions, and lasting reputational damage.
Dangers posed by the infostealer malware include:
Financial loss. Stolen banking credentials, credit card details, and cryptocurrency wallets can result in drained accounts and fraudulent transactions. Cybercriminals often sell this data on the dark web, allowing others to exploit it further.
Identity theft. Infostealers collect personal information like Social Security numbers, addresses, and phone numbers, which cybercriminals can use to impersonate victims, open fraudulent accounts, or commit tax fraud.
Account takeovers. Cybercriminals use stolen credentials and session cookies to access personal and business accounts. Once inside, they can lock out the rightful owner, transfer funds, or use the account for further attacks.
Business email compromise (BEC). Hackers can infiltrate corporate email accounts, posing as executives or employees to authorize fake transactions, manipulate vendors, or spread malware within the organization.
Data breaches. Businesses store vast amounts of sensitive customer and employee data. An infostealer attack can expose confidential records, leading to legal consequences, regulatory fines, and loss of customer trust.
Espionage and trade secrets theft. Attackers can steal intellectual property, internal communications, and strategic business plans, giving competitors or cybercriminal groups a significant advantage.
Supply chain attacks. Cybercriminals may use stolen credentials to infiltrate a business's network and attack its partners, vendors, or clients, extending the damage far beyond the initial breach.
Operational disruptions. Once malware infiltrates a system, businesses may need to shut down networks, revoke compromised credentials, and conduct forensic investigations, leading to downtime and lost productivity.
Who are the most common targets of infostealer malware?
Infostealers can target anyone, but businesses are among the most common victims. Recent infostealer malware statistics from SpyCloud's 2024 Malware & Ransomware Defense Report show a rise in attacks, proving that no industry is safe from these threats. Cybercriminals see businesses as high-value targets because they store lots of valuable information. A single breach can expose thousands of accounts, making organizations far more lucrative than individual victims.
Industries like finance, healthcare, e-commerce, and technology are frequent targets. Attackers steal banking credentials, medical records, and customer payment data, while technology firms are targeted for intellectual property and infrastructure access. Governments and defense organizations also face attacks aimed at espionage and classified data theft.
High-net-worth individuals, executives, and investors are frequently targeted due to their financial assets. Social media users and influencers are also at risk because stolen accounts can be used to spread scams or demand ransom. Gamers and cryptocurrency traders often fall victim to infostealers that steal gaming accounts, digital assets, and crypto wallet credentials.
Signs your systems are infected with infostealers
Infostealer malware operates quickly and quietly, often on devices outside your direct control. Because traditional security alerts are rarely triggered, early detection relies on recognizing the subtle signals.
While infostealers are designed to avoid detection, they leave clear indicators if you know where to look.
Here are common signs that an infostealer has targeted your organization:
Unusual login patterns. Watch for logins from strange locations, at odd hours, or from unrecognized devices.
Suspicious account behavior. A single user account logged in from multiple countries at once is a major red flag.
Phishing attacks. Be cautious of phishing emails that come from legitimate, active employee accounts.
Strange activity on privileged accounts. This includes unexpected attempts to change security settings or access sensitive systems.
Login attempts from old accounts. Attackers often test stolen credentials using the accounts of inactive or former employees.
Unknown devices on your network. Look for personal or unmanaged devices suddenly appearing in your logs and accessing company resources.
Individually, these signs may not confirm an infostealer infection. However, when viewed together, they paint a clear picture. Your security depends on connecting these signals before a minor incident becomes a major breach.
How to protect against infostealer malware attacks
Protecting your organization from infostealers requires a layered defense that combines strong technical controls, employee awareness, and proactive monitoring. Here are the essential steps to take..
Step 1: Detect infostealer malware early
Many infostealers operate undetected for weeks or months. Early recognition of infection signs can stop an attack before it escalates.
Watch for unusual activity. Unexpected logouts, failed login attempts, or unauthorized transactions could indicate a breach.
Monitor system performance. Sudden slowdowns, increased CPU usage, or strange processes running in the background may suggest active malware.
Step 2: Implement strong security measures
A multi-layered security strategy significantly reduces the risk of infostealer malware.
Enforce the use of strong, unique passwords. A password manager can help prevent credential reuse and reduce the impact if one account is compromised.
Enable multi-factor authentication (MFA). Even if an infostealer steals a password, MFA can block unauthorized access to an account. However, keep in mind that MFA won't help if the infostealer has stolen active session cookies as well.
Reduce exposure to cyber threats. Attack surface management monitors external-facing assets, such as domains and IP addresses, to identify vulnerabilities before attackers exploit them.
Step 3: Prevent account takeovers and session hijacking
Cybercriminals use stolen credentials and session cookies to gain unauthorized access to business accounts and bypass security measures.
Monitor for compromised credentials. Account takeover prevention scans the deep and dark web for exposed employee, customer, and partner credentials to prevent unauthorized access.
Stop session hijacking before it escalates. Session hijacking prevention detects malware-infected users, identifies stolen session cookies, and invalidates compromised sessions to block attackers from taking control.
Step 4: Avoid opening suspicious attachments and links
Phishing emails and malicious downloads are the most common ways infostealers spread.
Don't open unknown email attachments. Even files that appear harmless (such as PDFs or Word documents) can contain embedded malware.
Don't open malicious links. Hover over URLs before clicking to verify their legitimacy.
Detect dark web threats before they escalate. Dark web monitoring tracks business-related keywords across illicit markets, hacker forums, and cybercriminal communities to provide early warnings of targeted attacks.
Step 5: Regularly update software and systems
Outdated software contains vulnerabilities that infostealers exploit.
Keep operating systems and applications up to date. Install security patches as soon as they become available.
Restrict software downloads. Prevent employees from installing unauthorized programs that could introduce malware.
Step 6: Conduct employee security training
Many malware infections occur due to human error, such as clicking on malicious links, reusing passwords, or downloading malicious files.
Train employees to recognize phishing attempts. Cyber awareness reduces accidental infections.
Simulate real-world attacks. Conduct internal phishing tests to measure security awareness.
Establish clear security policies. Define rules for handling sensitive information, downloading software, and reporting suspicious activity.
Infostealer malware is a silent threat, stealing credentials and sensitive data before you even realize it. Contact the NordStellar team to get complete visibility over your cyber threats.
FAQ
What are the most common signs of infostealer malware infections?
The most common signs are anomalies in user and system behavior, such as suspicious login patterns from new locations, phishing emails sent from legitimate internal accounts, and login attempts using old or disabled credentials.
Which industries are most targeted by infostealers?
Attackers usually target industries with high-value data, such as finance, healthcare, e-commerce, and technology. Threat actors seek payment information, patient records, and intellectual property from these sectors. Government and defense organizations are also frequent targets for espionage.
Where is stolen data from infostealers sold?
Stolen data is sold as "stealer logs" on underground platforms. While some individual logs are sold on dark web marketplaces, bulk sales typically happen on encrypted messaging apps like Telegram, which offer cybercriminals greater anonymity.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she loves explaining complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.