
Rūta Tamošaitytė
Copywriter
Cybersecurity

Summary: Ransomware surged 45% in 2025, led by Qilin and new groups targeting US manufacturing SMBs. See why proactive monitoring is essential for defense.
As we step into the new year, we compared the 2025 data to the previous year. The trend is clear: ransomware attacks jumped by 45% in just twelve months. US-based small and medium manufacturers bore the brunt of these attacks—particularly those in general manufacturing, machinery, and the electronics and electrical sectors.
Below, we review last year’s victim profiles and share insights from NordStellar cybersecurity expert Vakaris Noreika. Then, we’ll take a closer look at the specific trends from Q4.
Ransomware is a malicious software that restricts access to a computer system or data by encrypting files or locking systems, holding them hostage for a payout. It usually creeps in via email phishing, social engineering, malvertising, and exploit kits. Once in, cybercriminals threaten to publish the company's data if the ransom isn’t paid on time.
The problem is, paying doesn't guarantee safety. Attackers often refuse to hand over the decryption key or just lock the files again for a second ransom. It leaves companies facing financial loss, legal trouble, and a ruined reputation.
The continued rise in incidents shows that ransomware remains highly profitable, incentivizing cybercriminals to ramp up activity. Our latest findings reveal that the number of ransomware incidents in 2025 soared compared to 2024. The data shows that in 2025, 9,251 ransomware cases were recorded on the dark web, a 45% increase from 6,395 cases recorded in 2024.
The number of ransomware cases peaked in the last quarter of 2025. December set a two‑year record with 1,004 incidents in a single month.
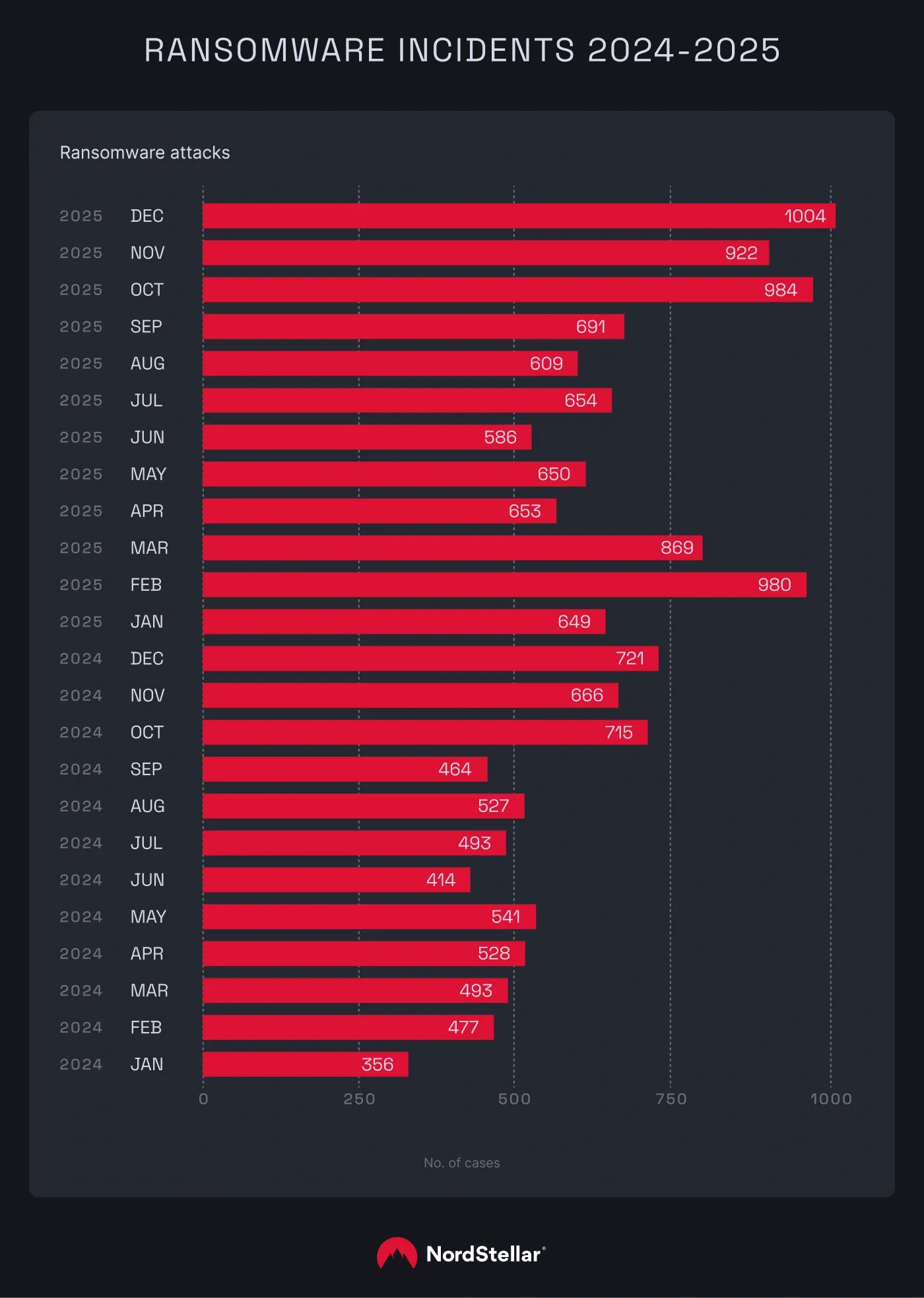
"In the final quarter of 2025, ransomware groups exploited end-of-year cybersecurity gaps caused by reduced staffing and monitoring," says Vakaris Noreika. "However, the trend has been upward the whole year. Ransomware actors are growing more aggressive—given the surge in 2025, ransomware incidents in 2026 are likely to exceed 12,000."
According to Noreika, the number of ransomware groups is also increasing. The recorded ransomware incidents in 2025 could be traced back to 134 different groups—a 30% increase from the 103 groups seen in 2024.
In this section, we take a closer look at the targets, breaking them down by country, industry, and business size.
Let’s start with a look at ransomware by country. The US remains the primary target, accounting for 64% of all global cases. In 2025, we recorded 3,255 incidents—a 28% increase from the previous year. Other regions also saw shifts. Canada followed with 352 cases (up by 46%), while Germany experienced a sharp 97% jump with 270 incidents. The UK (up 2%) and France (up 46%) rounded out the top five.
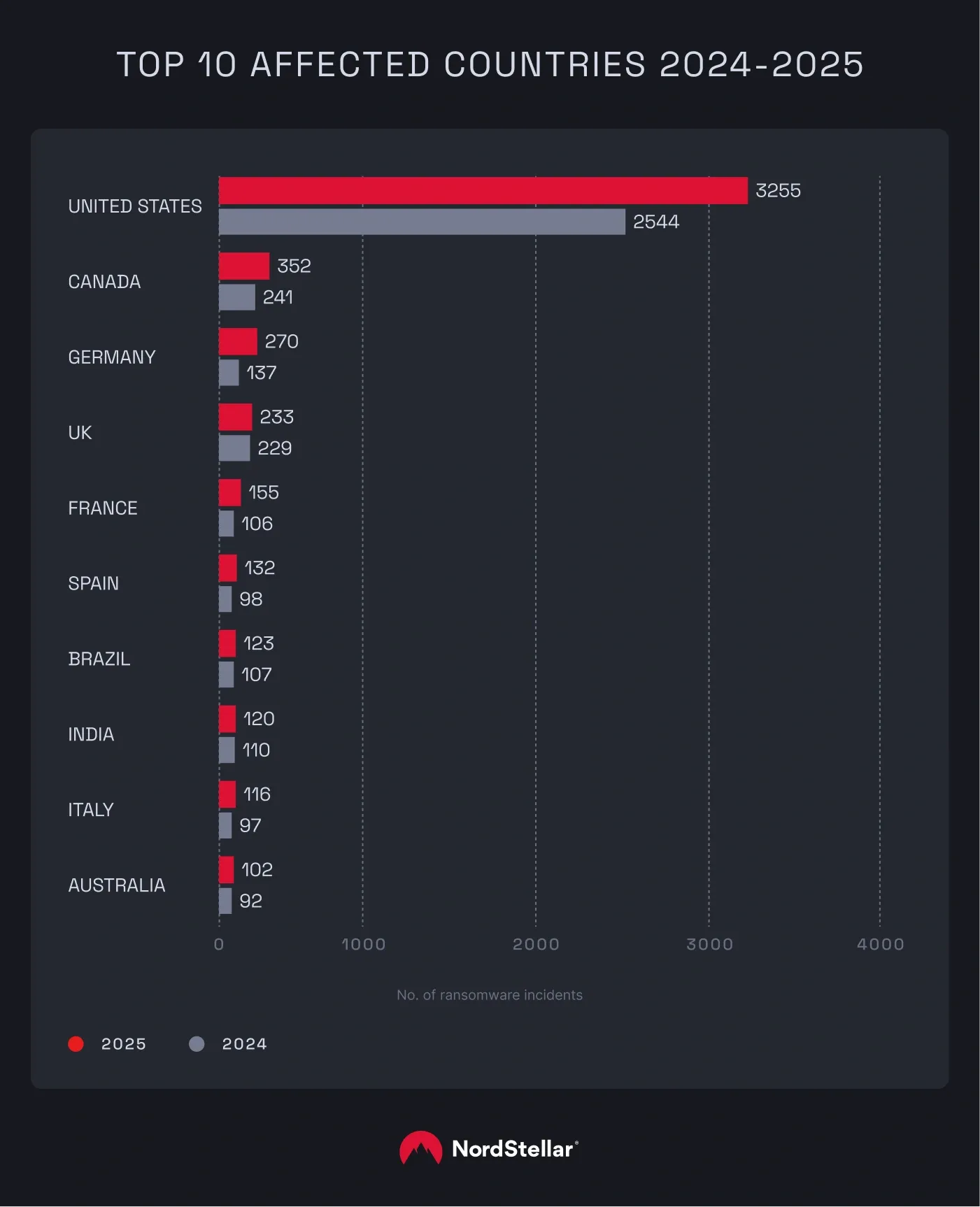
The findings mirror data from the past two years: the high volume of US attacks is likely due to the country’s concentration of profitable businesses and strict regulations, which make these organizations high-profile targets.
In 2025, the trend for SMBs remains unchanged—companies with fewer than 200 employees and revenues up to $25 million experienced the most attacks, a trend that mirrors our 2024 findings.
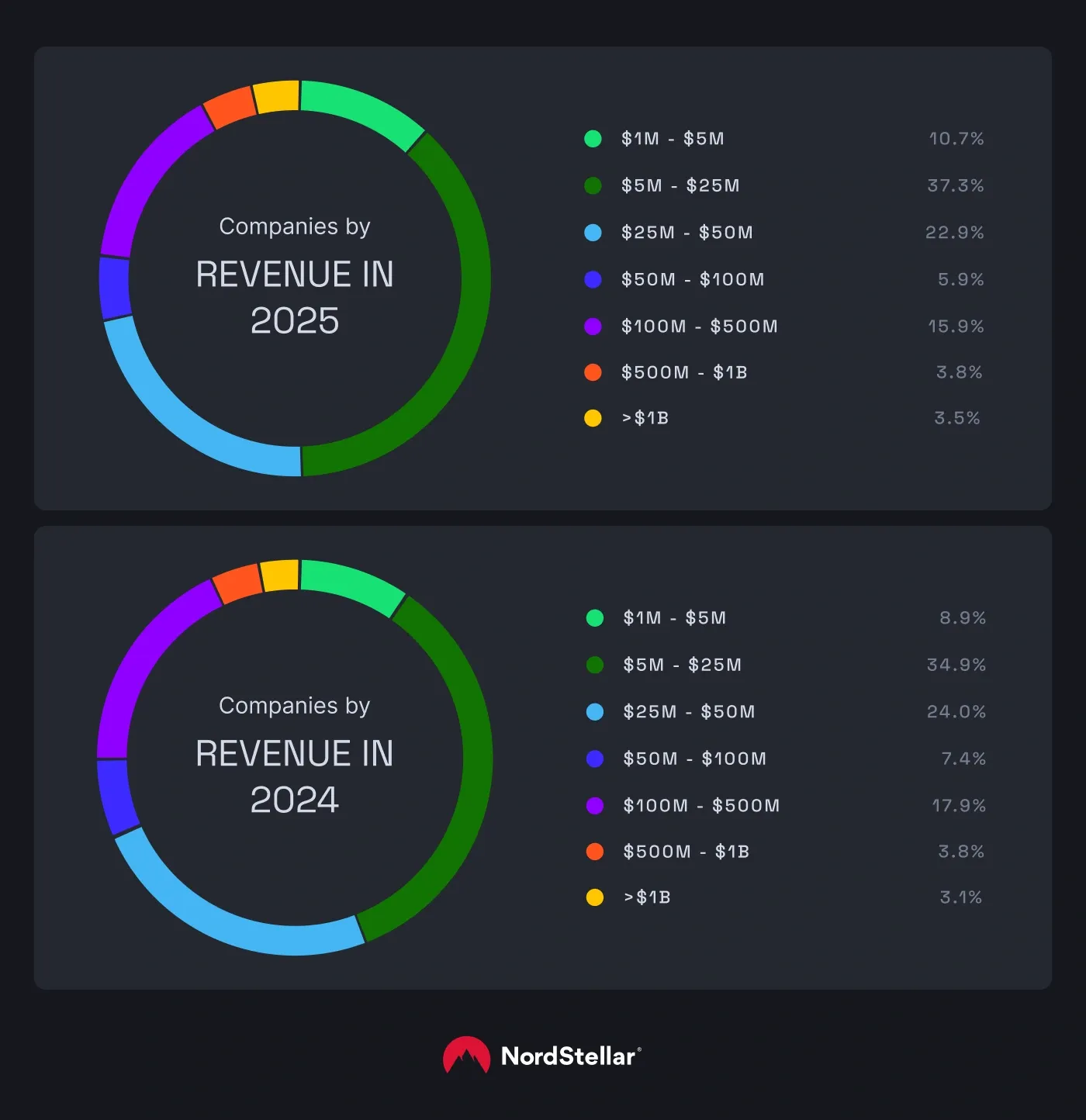
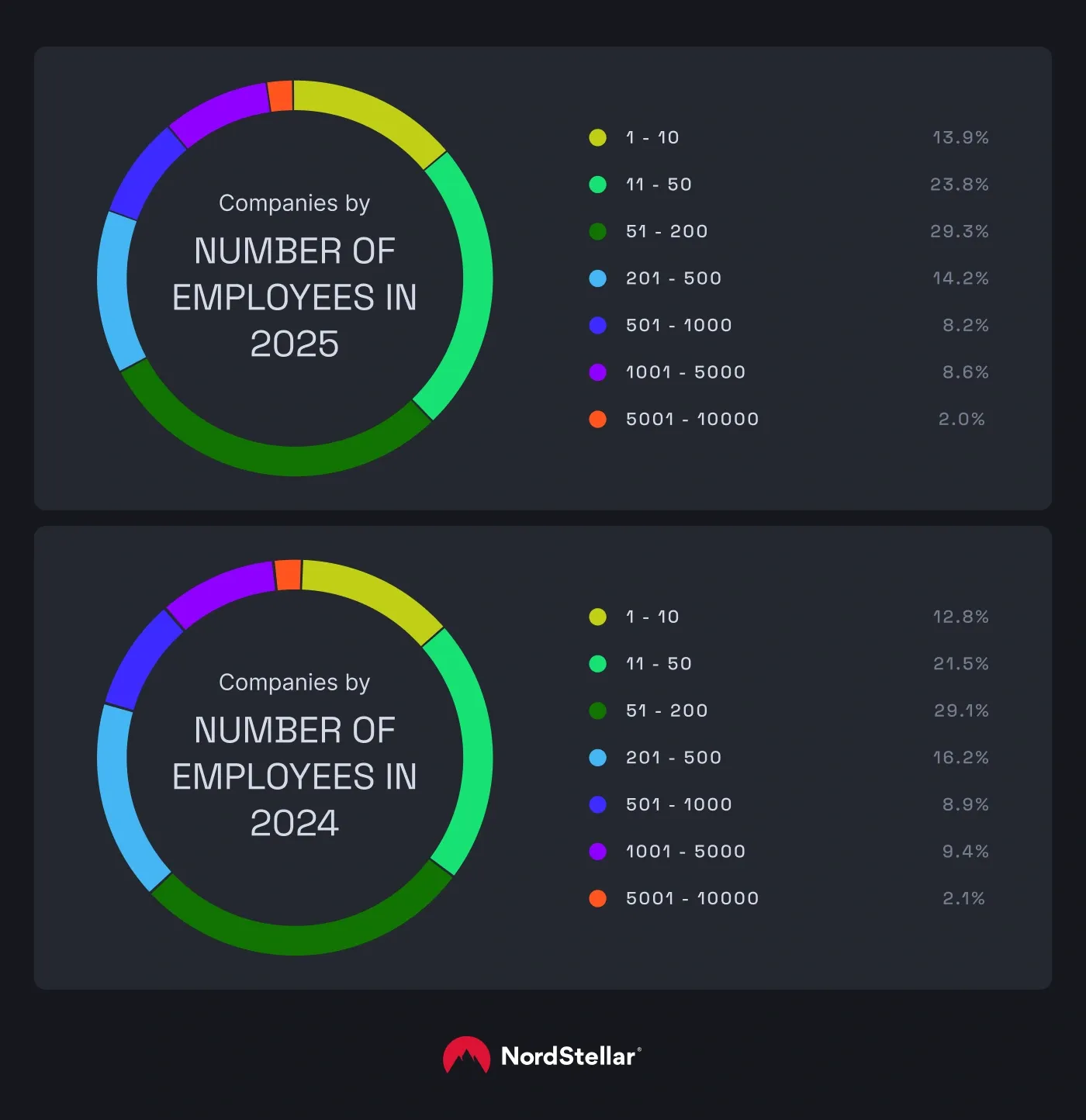
“SMBs are attractive targets for ransomware attacks because they often lack security staff and tools and operate within limited cybersecurity budgets—all of which are essential to safeguard their systems," says Noreika. "Smaller organizations are also more likely to rely on outdated software, have limited security monitoring, and rely on external vendors for IT support. Consequently, when attacked, they're more likely to pay ransoms quickly to avoid business disruptions, which is why ransomware groups keep targeting them.”
The manufacturing sector continues to be the primary target for ransomware. In 2025, the industry saw 1,156 incidents—a 32% increase from the previous year. This sector now accounts for 19.3% of all recorded cases, maintaining its position as the most targeted industry for two years running. This happens because of the sector’s unique risk profile: high revenue potential paired with underdeveloped security frameworks and limited operational resilience. We will touch on this more in-depth in the next section.
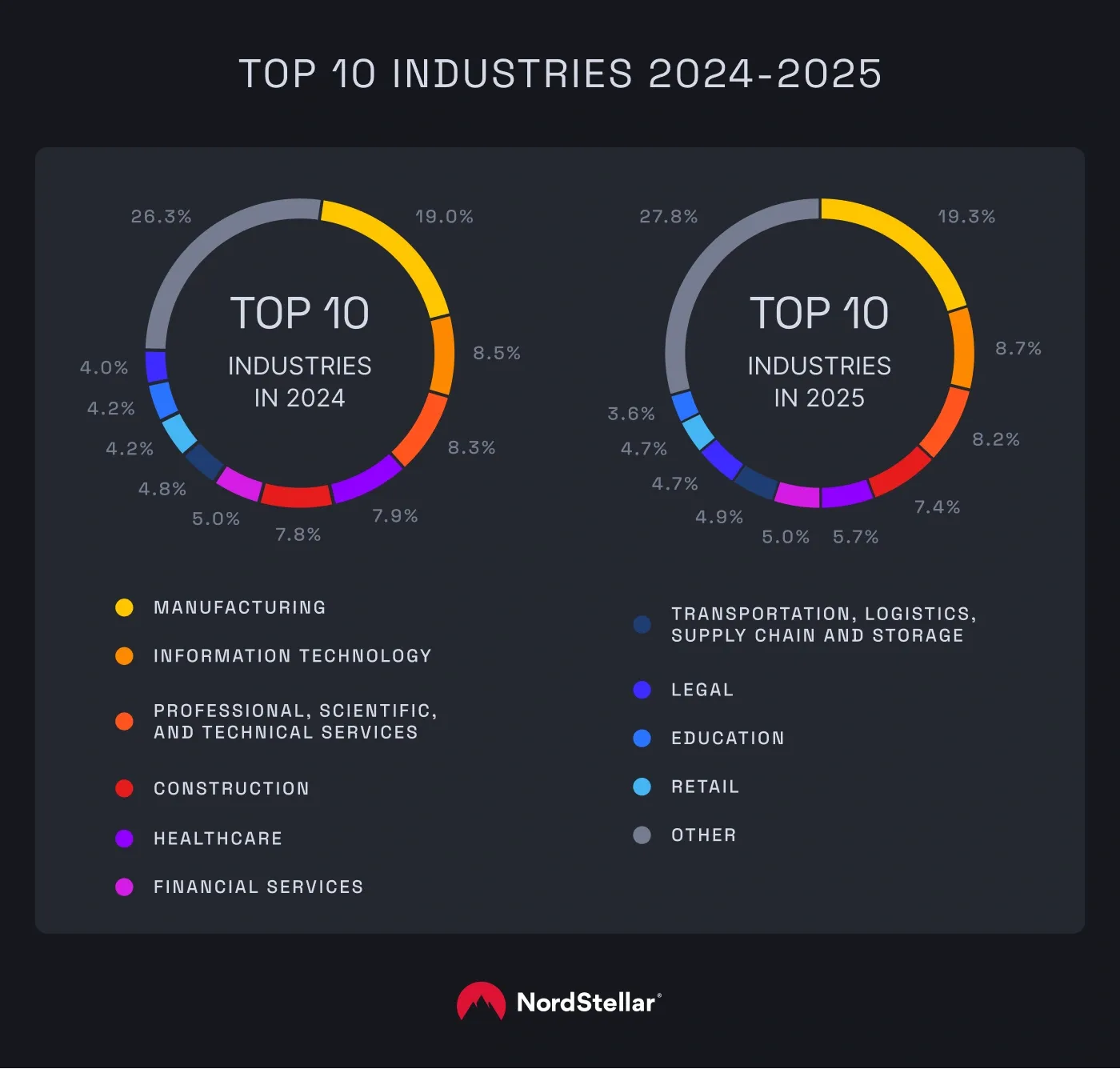
The IT sector followed with 524 cases, marking a sharp 35% rise from 2024. Other sectors saw similar upward trends: professional and scientific services rose by 30% (494 incidents), while construction grew by 24% with 443 recorded attacks. Healthcare was the only outlier in this group, seeing a slight 6% decrease with 339 incidents.
Because manufacturing consistently leads as the top target for two years in a row, we dug deeper into the data. We found that cybercriminals are increasingly focused on what seems to be a sweet spot for them: SMBs.
Companies with up to 200 employees and $25M in revenue, operating in the general manufacturing industry, were the most targeted. Second came smaller businesses in the machinery manufacturing sector, accounting for 10% of all industry attacks. Finally, SMBs operating in the appliances, electrical, and electronics manufacturing sector followed closely with 9,9% of all ransomware attacks on the industry.
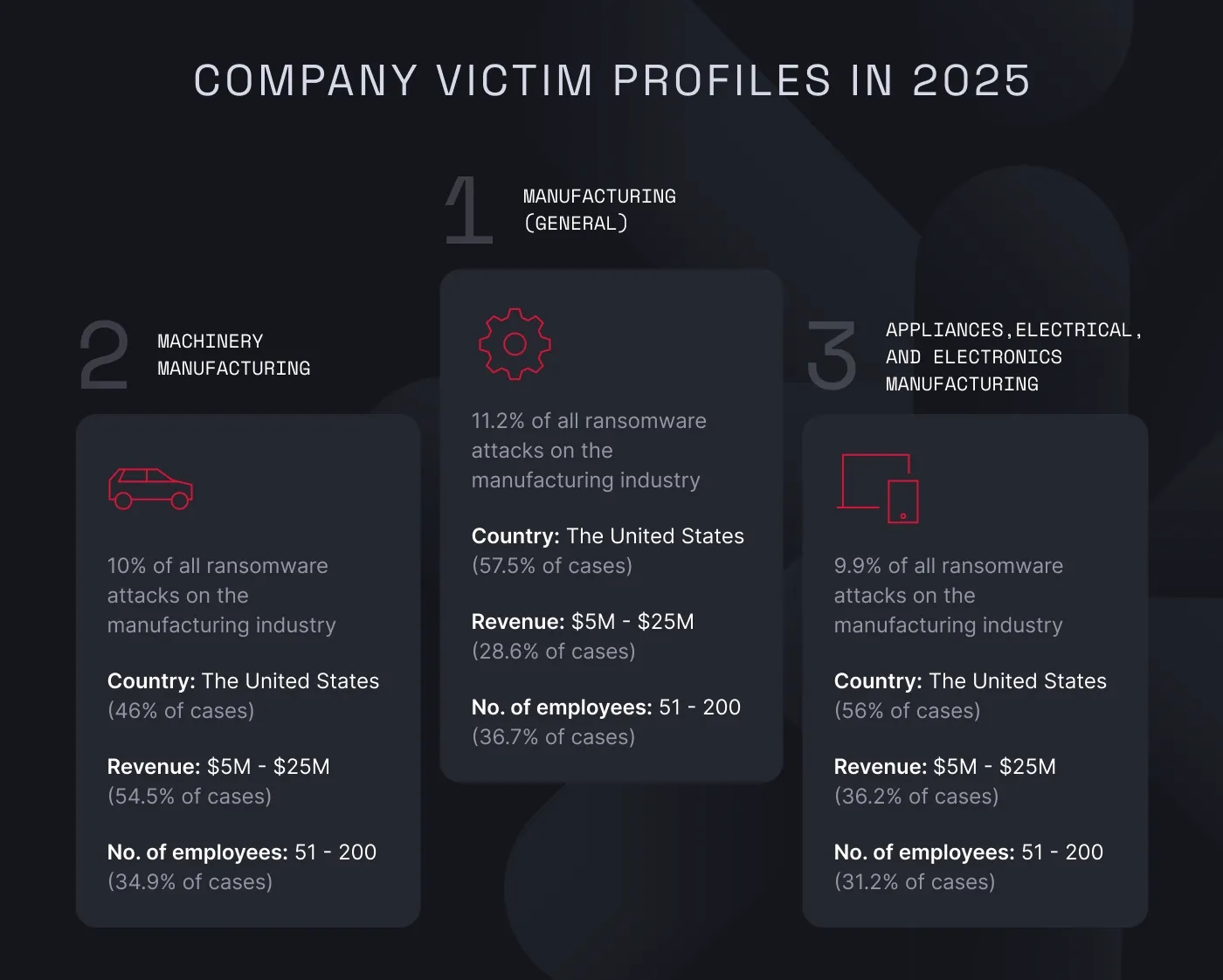
"Cybercriminals prioritize choosing targets that offer the biggest payoff for the least amount of effort, and SMBs in the manufacturing industry fit this perfectly—they generate enough revenue to pay large ransoms but usually don't have the capacity to implement strong security measures or fast recovery options," says Noreika.
This creates a high-pressure environment where every minute of downtime counts. Because production lines can’t stop for long without causing significant financial losses, many organizations feel forced to give in to attackers' demands just to keep operations running.
Additionally, the risk profile also shifts as these businesses modernize: "Machinery and industrial equipment manufacturers were also heavily targeted—this could be the result of expanded digitalization and remote connectivity in production environments," says Noreika. "Meanwhile, appliance and electronics manufacturers are facing a higher risk of experiencing a cyberattack due to complex supplier integration and cloud-based operations."
Ultimately, these interconnected environments increase the likelihood of lateral compromise, where a single weak point in a shared network or third‑party access port can expose the entire operation.
Qilin carried out the most attacks in 2025, with 1,066 cases—a 408% increase compared to 2024. This Russia-linked RaaS criminal operation works with affiliates to encrypt and exfiltrate data from the victim companies.
Akira followed closely behind with 947 recorded cases—a significant 125% increase from the previous year. We also saw a massive resurgence from Cl0p, whose leaked cases jumped by 525% to 594.
However, the most notable shift came from newer players like Safepay. This rapidly growing threat actor saw a staggering 775% increase in activity, recording 464 cases in 2025. Rounding out the top group was INC Ransom, which maintained a steady upward trend with 442 cases, up 83% compared to 2024.
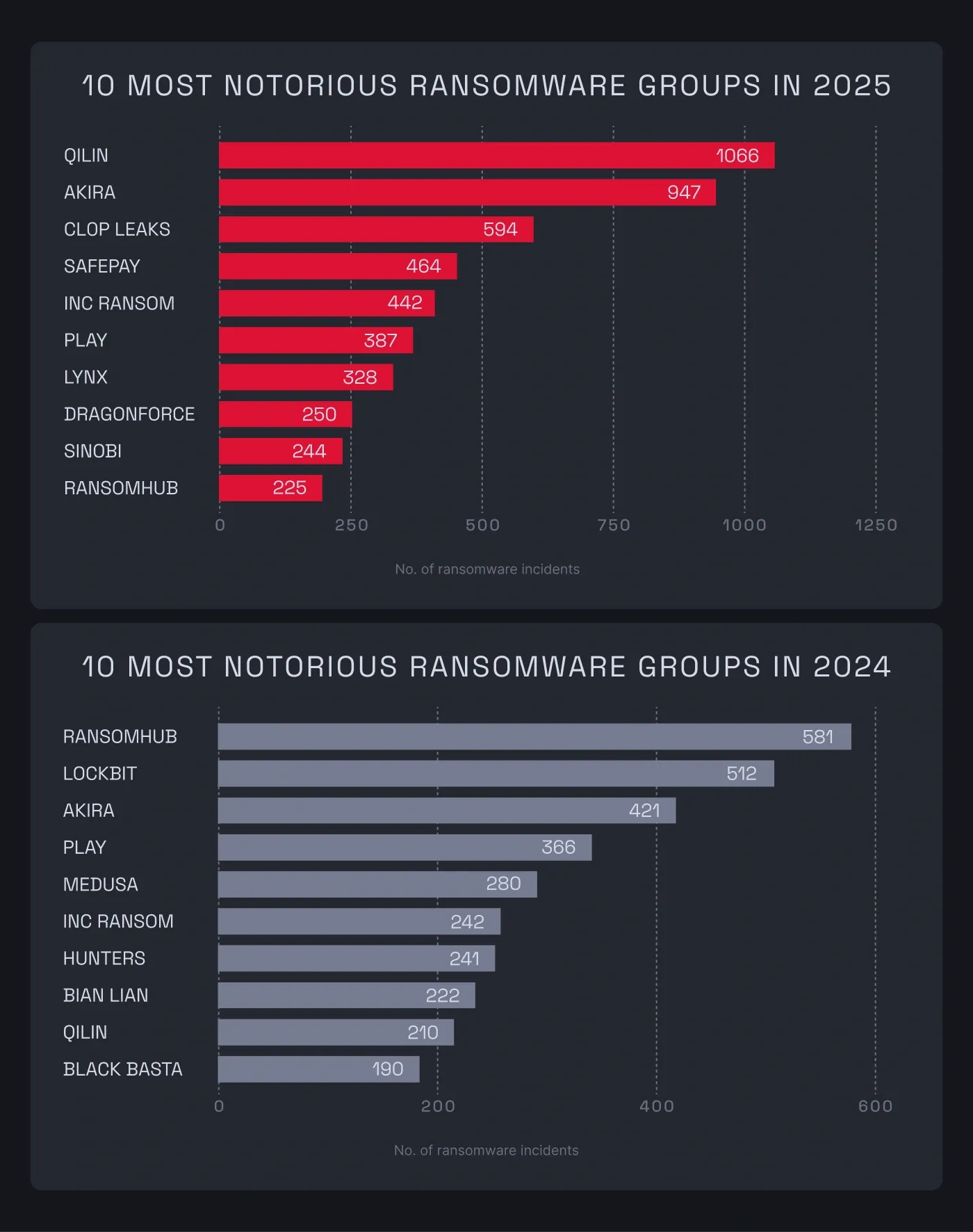
"The changes in the ransomware threat actor landscape reflect how competitive the ransomware-as-a-service world has become," says Noreika. "Groups like Qilin experienced significant growth because many affiliates joined their operations after other platforms were shut down or became less profitable. Affiliates choose which ransomware to use based on better payment structure, support, the reliability of the tools provided, or the reputation of success."
The growth of groups like Akira points to a common pattern. As Noreika explains, new ransomware names often emerge when existing groups rebrand or launch fresh operations to evade law enforcement.
For example, we witnessed such a dynamic with LockBit, one of the most active groups in 2024. Their activity declined in 2025 following successful law enforcement interventions. This suggests that while the names on the list may change, the underlying threat simply adapts to stay under the radar.
The end of 2025 saw a sharp rise in ransomware activity, with cases peaking in the final quarter. Our research recorded 2,910 incidents during this period—a 38% increase compared to Q4 of the previous year. Even more notable was the jump within 2025 itself; the final three months saw a 49% increase in attacks compared to the July-September period.
This year-end surge reinforces a trend we observed throughout 2025: small and medium-sized manufacturers remained the primary target. As these organizations pushed to meet end-of-year production goals, cybercriminals appeared to be capitalizing on the increased pressure and potential oversight in security protocols.
Now, let’s review this last quarter in greater detail by slicing the data by country, business size, and industry.
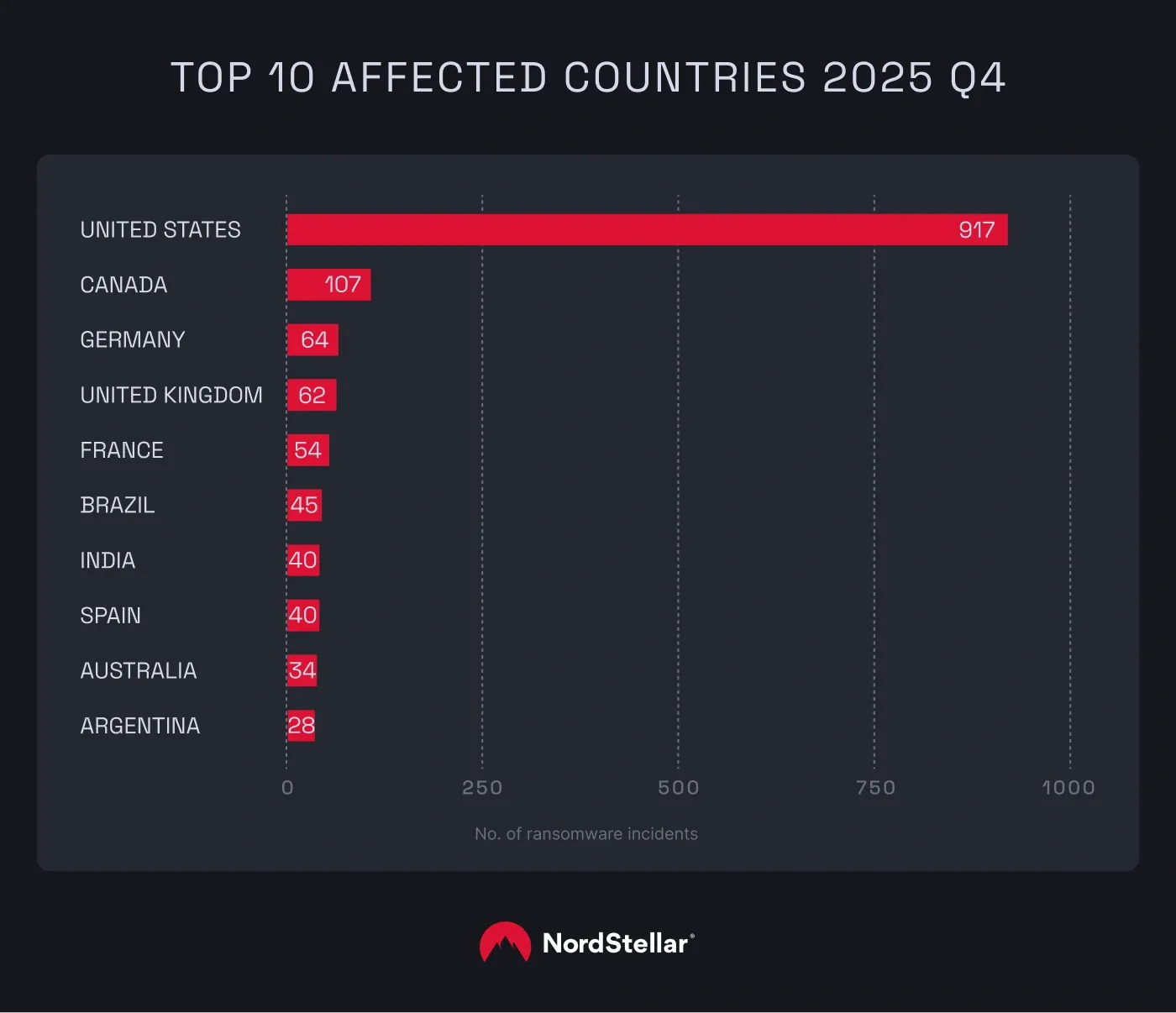
US businesses took the most brutal hit, with ransomware activity climbing steadily as the year drew to a close. After recording 686 incidents in Q3, the number of cases rose to 917 in Q4—a 34% increase in just three months. This surge aligns with the global peak we observed during the same period, confirming that the final quarter remains the most volatile window for American organizations.
The second-most-affected country was Canada, with 107 cases (a significant 73% increase from Q3, when there were just 62 cases). These countries were followed by Germany (64), the United Kingdom (62), and France (54).
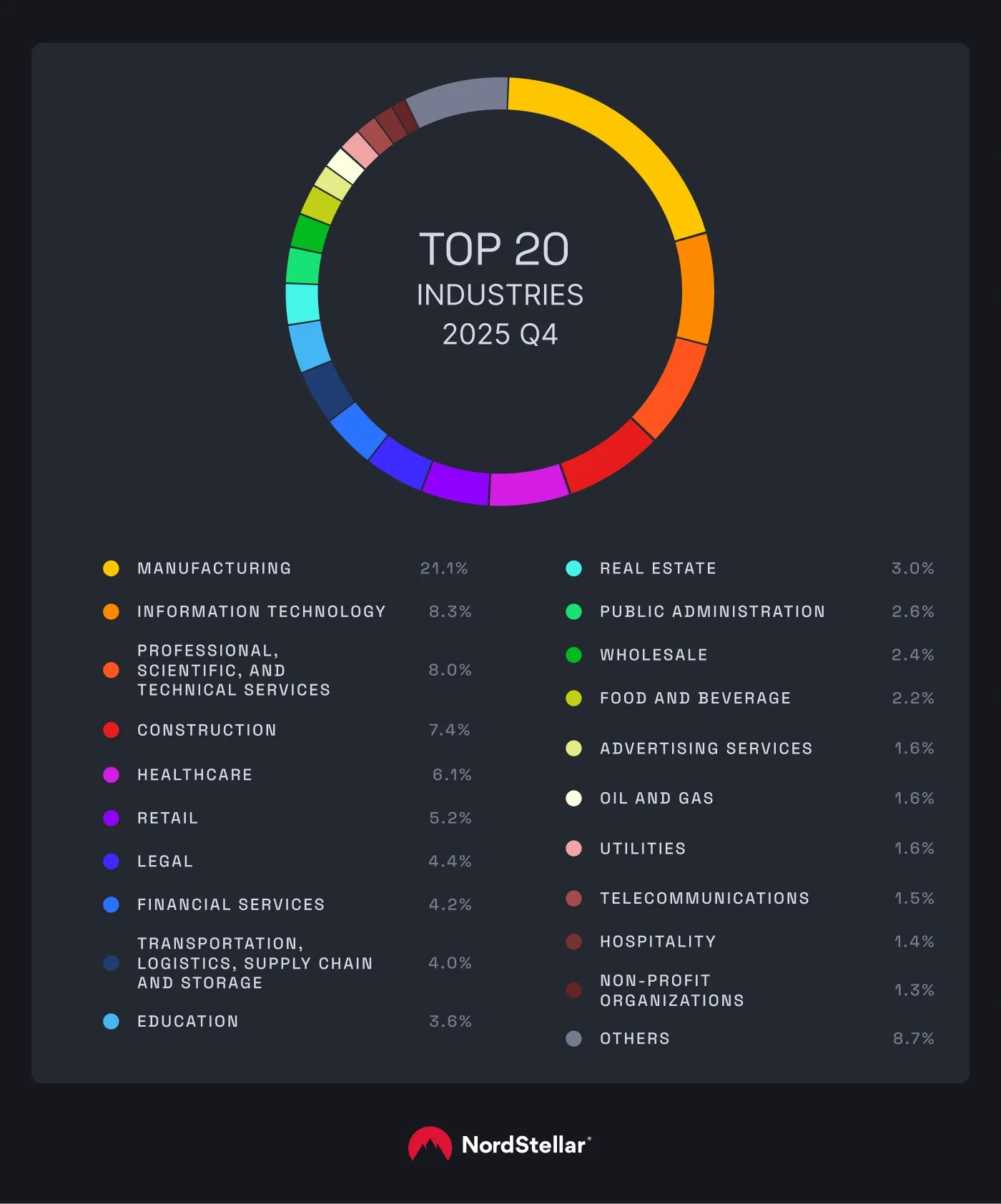
Consistent with our earlier findings, the manufacturing industry remained the most affected in Q4 2025. From 2025 Q3, we recorded 245 incidents, but that number climbed to 386 in October and December—a 58% increase. Other sectors significantly impacted included information technology (152 cases), professional, scientific, and technical services (147 cases), and construction (111 cases).
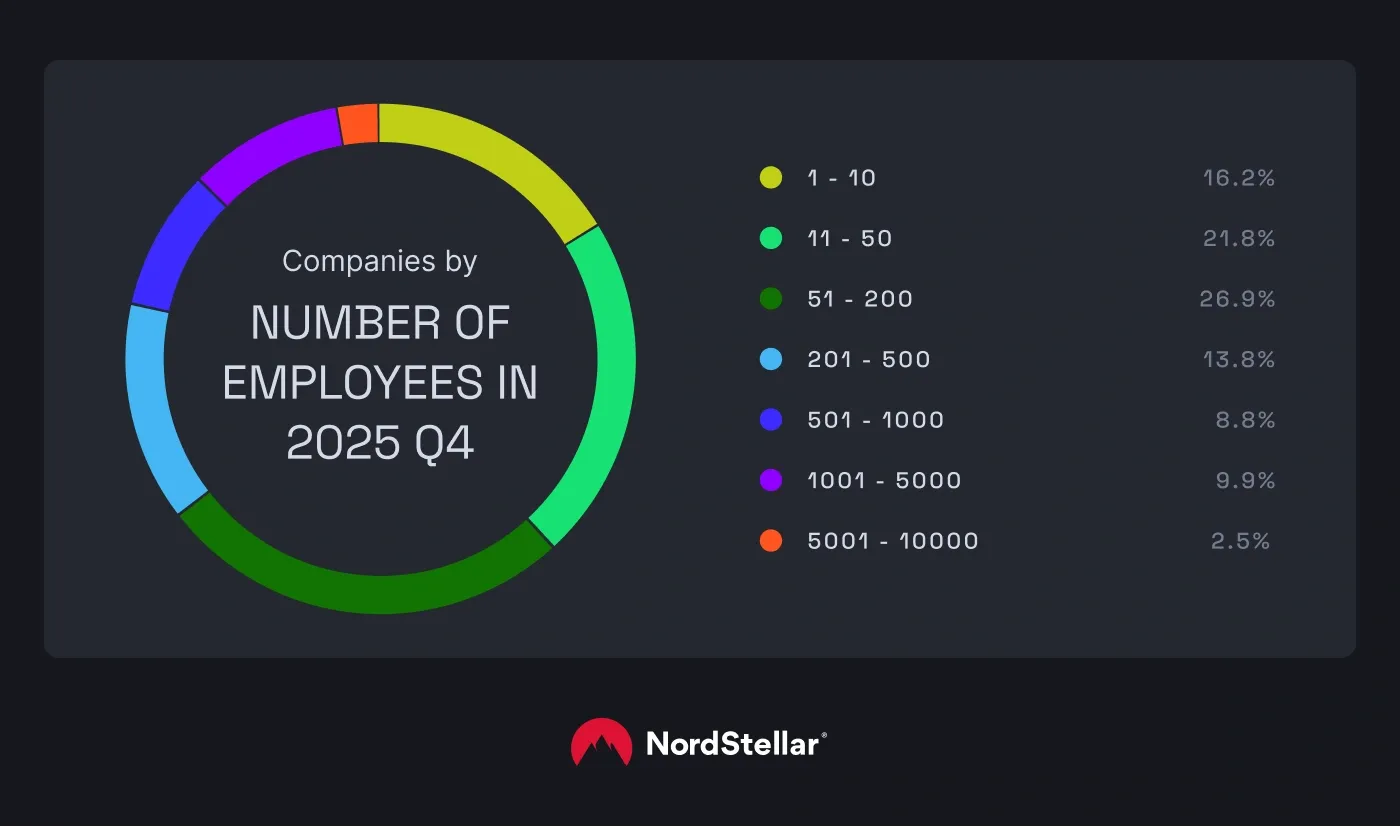
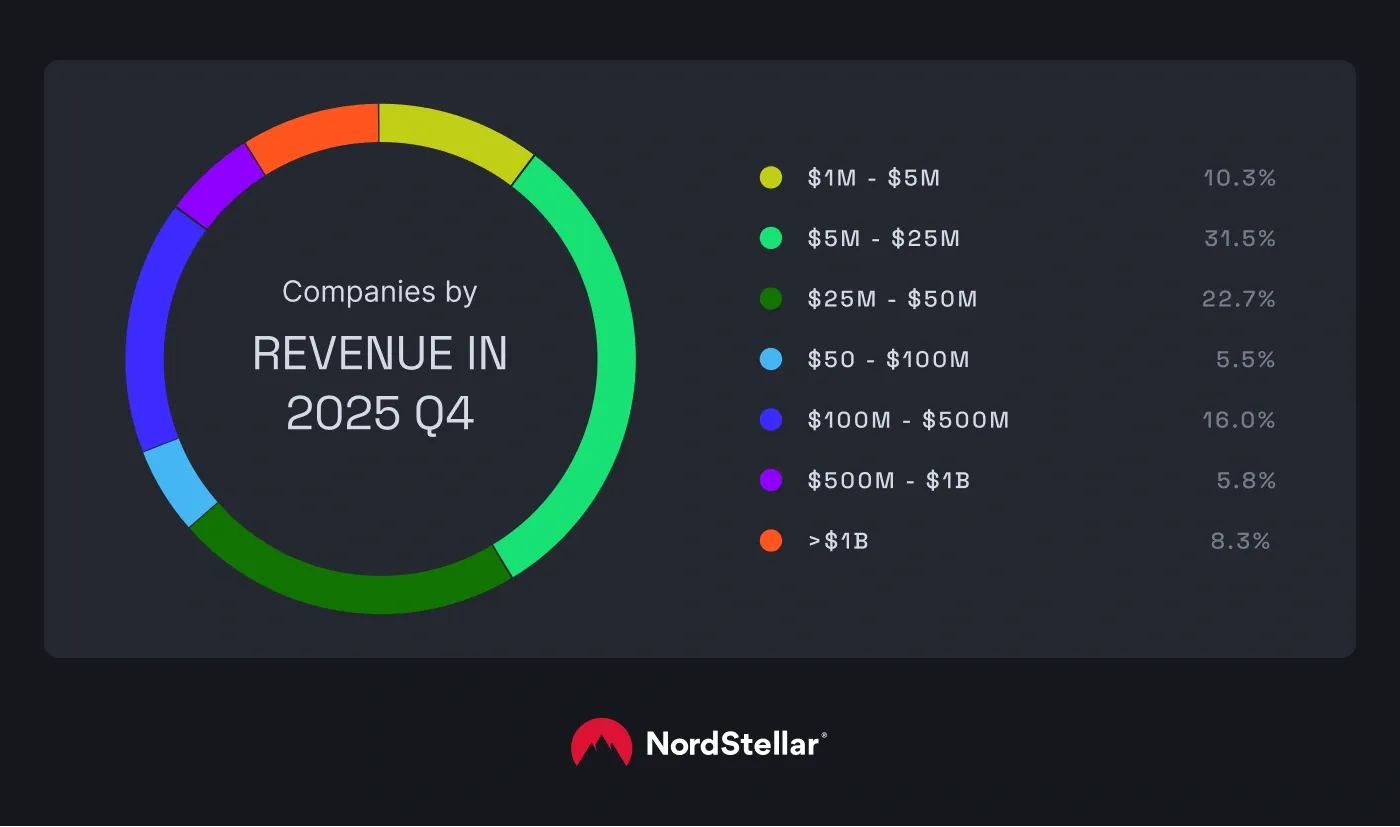
Ransomware data from the last quarter of 2025 revealed that SMBs were the prime targets. Specifically, organizations with 51–200 employees and revenues between $5M and $25M experienced the most attacks.
As we mentioned in the victim profile section, these figures remain high because companies with lower revenues may be more likely to meet attackers' demands. Since they can’t afford the downtime, data loss, or reputational and financial damage, they often view paying the ransom as the only option to survive. And this makes them a more attractive target for ransomware attackers.
Qilin remained the top threat to industrial organizations throughout the end of the year, holding the number one spot for the second consecutive quarter. Our research shows the group’s activity more than doubled in the final months of 2025, with recorded cases jumping from 241 in Q3 to 489 in Q4—a 103% increase.
This rapid growth is no accident. By combining active affiliate recruitment with a mature infrastructure for negotiations and data leaks, Qilin has established itself as a highly efficient and dangerous RaaS operation.
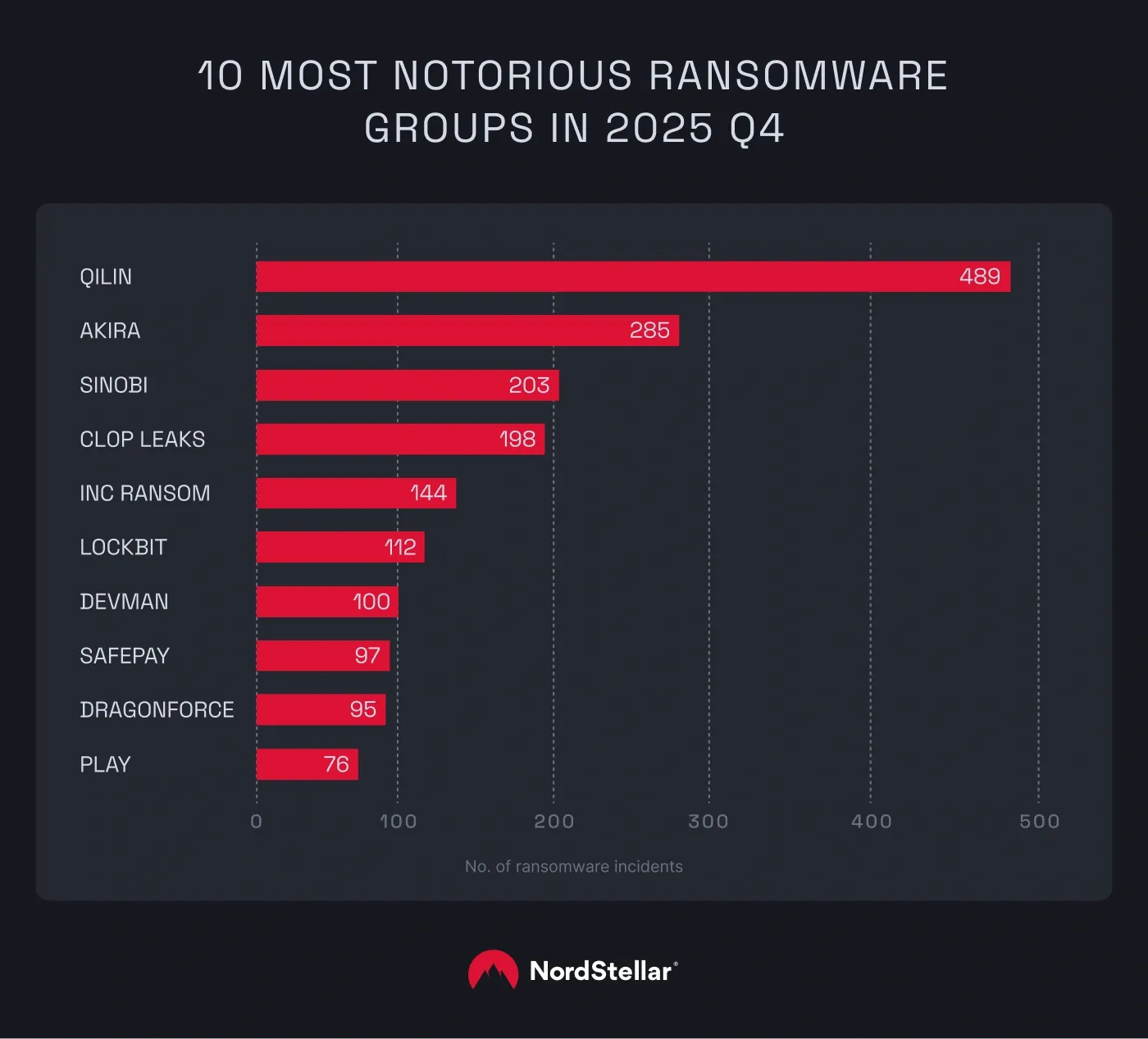
The next comes Akira which holds the second spot with 285 ransomware incidents, followed closely by Sinobi, another ransomware group, with 203 incidents. Then follows Cl0p Leaks with 198 incidents, and Inc Ransom with 144.
The final quarter of 2025 signaled a shift as new and resurgent groups began to challenge established players. A prime example is Sinobi, which emerged in mid-2025. While its name is a stylized reference to the Japanese shinobi (ninja), its activity patterns and linguistic artifacts suggest it likely operates out of Russia or Eastern Europe.
Evidence suggests Sinobi is a direct successor or rebrand of the Lynx group. Lynx ranked 6th last quarter with 74 recorded incidents. Sinobi’s rapid ascent to the top three this quarter confirms that when groups often disappear, they often simply evolve under a new identity to evade pressure while retaining their technical expertise.
Given the persistence of ransomware attack trends, it's clear that this threat is here to stay. So, what can you do to protect your business?
"The success of end-of-year attacks is concerning — this will likely motivate ransomware groups to repeat these timing patterns at the end of 2026 as well," says Noreika. "Businesses, especially SMBs and those operating in industries where operational downtime is unacceptable, or that handle high-value data, should be on high alert and reassess their preparedness to combat ransomware."
To increase their resilience against ransomware attacks, Noreika advises companies to strengthen their basic security hygiene. This includes updating and patching systems and applications, using multi-factor authentication, implementing password management policies, and enforcing a zero-trust framework to prevent malware from spreading laterally.
"For early threat prevention and detection, intelligence is key — it enables businesses to patch critical vulnerabilities and detect indicators of compromise as soon as possible," says Noreika. "Data leaked onto the dark web may expose credentials or sensitive details that attackers can exploit to gain unauthorized access. An early alert enables organizations to reset passwords, revoke access keys, disable compromised accounts, and support faster incident response."
Noreika explains that having a ransomware incident response plan is crucial for reducing the scope of damage from an attack as soon as possible. He also emphasizes the importance of having a recovery plan as well as backing up critical data to minimize operational downtime.
We continuously monitor over 200 blogs run by ransomware groups. The ransomware data available on these blogs typically includes the names of the attacked companies, descriptions of the incidents, and sometimes samples of the stolen files to prove the legitimacy of the attack. These groups publish their victims’ names as a tactic to pressure them into paying the ransom. They often add a countdown timer, after which they threaten to leak the stolen data if the ransom is not paid.
Once a company is identified from a ransomware listing, we conduct further research to gather firmographic data. While the reported totals—9,251 ransomware attacks in 2025, 6,395 in 2024, and 2,910 in Q4 2025—are accurate, the specific breakdowns presented by industry, company size, and country categories may deviate slightly due to smaller sample sizes. We use various publicly accessible business data sources to identify general organizational attributes, such as industry, geographic region, size, and revenue bracket, using the company name and domain.
Here you can find the main ransomware attack data from the previous quarters.
The upward trend in ransomware activity continued through the third quarter of 2025. Between January and September, our research detected 6,330 cases exposed on the dark web—a 47% increase compared to the 4,293 cases recorded during the same period in 2024. This growth is driven by a record number of active groups and the continued expansion of the Ransomware-as-a-Service (RaaS) model.
Main ransomware targets:
Who was responsible for the attacks:
The number of ransomware attacks surged by 49% in the first half of 2025 compared to the same period in 2024. In total, 4,198 cases were exposed on the dark web between January and June 2025.
Main ransomware targets:
Who was responsible for the attacks: