
Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.
Cybersecurity

Summary: Disruptions from weak suppliers, ransomware, or political crises can cripple supply chains. Reduce risks through monitoring, training, and strong vendor collaboration.
Let's talk about the modern supply chain. It’s this incredibly complex, global dance of sourcing, manufacturing, and delivering goods. When it works, it’s a thing of beauty. When it breaks? Well, it’s less of a graceful ballet and more like a clumsy uncle at a wedding, knocking over the cake and causing chaos.
The interconnected nature of our global economy means that a single weak link can trigger a domino effect, leading to massive supply chain disruptions. Understanding supply chain vulnerability isn't just a good idea; it's essential for survival.
Your business is part of a sprawling supply chain network, and its strength is determined by its weakest point.
We’ll explore what makes a supply chain vulnerable, its very real impacts on your business, and, most importantly, what you can do to build a more resilient supply chain.
Think of supply chain vulnerability as the collection of weak spots or exposure points within your entire supply chain that make it susceptible to disruptions. It’s the probability that one or more supply chain vulnerabilities will materialize and cause a negative impact.
In simple terms, supply chain vulnerability means an inherent exposure to external risks and internal failures that can compromise your operating ability.
These aren't just theoretical problems. A hurricane shutting down a port, a geopolitical conflict halting trade, or a cyber-attack on a logistics provider are all real-world events that exploit these vulnerabilities. Effective supply chain risk management starts with acknowledging that these weak points exist and then actively working to find and fortify them.
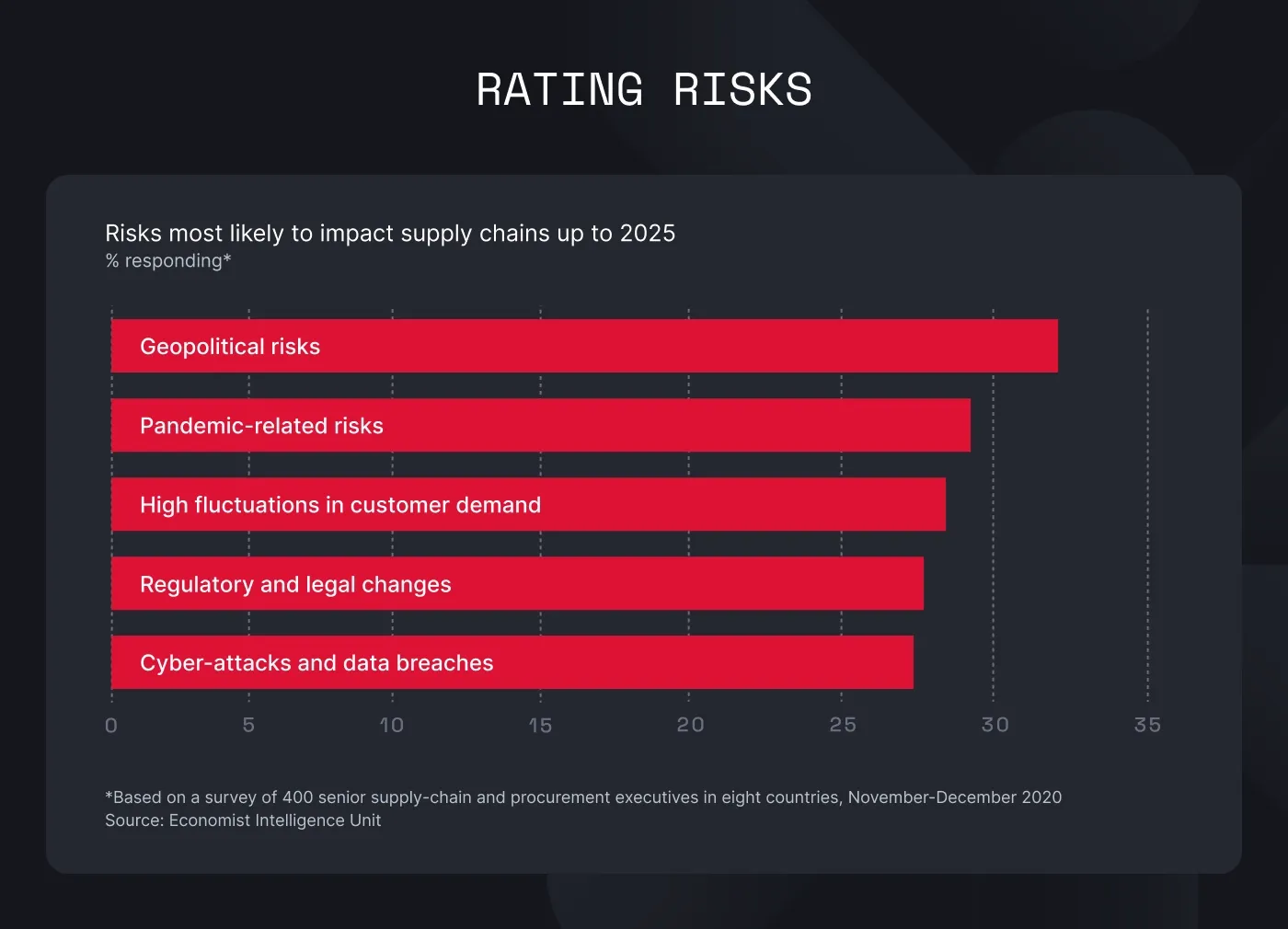
The range of supply chain threats and vulnerabilities is vast. They can come from anywhere, at any time. We could list dozens of supply chain vulnerability examples, but let's organize them and pay special attention to the ones that are becoming alarmingly common: cybersecurity threats, technology risks, and human factors.
Vulnerability type | Description | Examples |
|---|---|---|
Cybersecurity & technology risks | Threats targeting the digital infrastructure of your supply chain. Weaknesses in software, networks, and data security can be exploited by malicious actors. |
|
Human factors | Risks originating from human error, malicious intent, or lack of knowledge. People are often the most unpredictable element. |
|
Geopolitical & economic risks | Large-scale external factors stemming from political instability, trade policies, and economic shifts that impact the flow of goods. |
|
Logistical & operational risks | Relate to the physical movement and management of goods, from sourcing to final delivery. |
|
Environmental risks | Threats caused by the natural world, which are often unpredictable and can have a devastating physical impact on the supply chain. |
|
The focus on cybersecurity is critical. A software supply chain attack is particularly insidious because it compromises trust in the very tools you use to run your business operations. Attackers target less-secure vendors or even open-source code to gain a foothold, turning a trusted software update into a Trojan horse.
When an attacker exploits a vulnerability, the impact isn't just a minor inconvenience. It sends ripples across your entire organization, affecting everything from your production line to your bottom line and, crucially, your customer trust. These are not just supply chain risks; they are fundamental business risks.
Let’s look at the concrete consequences of these supply chain attacks and disruptions.
Impact area | Description of impact |
|---|---|
Financial losses | This is the most direct and painful impact. It includes lost sales due to product delivery failure, the high costs of expedited shipping to fix a problem, regulatory fines from data breaches, and the expense of recovery efforts. |
Operational disruptions | It can mean production lines stopping due to a shortage of critical components, leading to crippling system downtime. It also includes the inability to process orders or manage logistics. |
Reputational damage | In today's market, trust is currency. A failure to deliver on promises, or worse, a security breach involving customer data, can shatter customer trust that took years to build. Reputational harm can hurt your business for far longer than any financial loss. |
Legal & compliance issues | A security incident can put you in hot water with regulators. Failure to protect personal or sensitive data can lead to significant fines under regulations like GDPR or CCPA. Breached contracts with customers can also end up in legal battles. |
Loss of competitive advantage | While you are busy putting out fires and dealing with operational disruptions, your competitors are moving ahead. Prolonged supply chain disruptions can result in a permanent loss of market share. |
Now that the risks are clear, it's time to take the next step.
You can't fix a problem you don't understand. That's where a supply chain vulnerability assessment comes in.
A supply chain vulnerability assessment is a systematic process for risk identification and analysis across your entire supply chain. It's about moving from a reactive “put out the fire” mode to a proactive risk management strategy. Think of it as a comprehensive health check-up for your supply chain.

Here’s how you conduct one:
Conducting risk assessments is just the start. The real work is in implementing strategies that build supply chain resilience. Here are actionable steps you can take:
Building a resilient supply chain is not a one-time project; it’s an ongoing commitment to vigilance and adaptation. Moving from a reactive to a proactive stance on supply chain vulnerability is the single most important shift you can make.
This involves diversifying suppliers and strengthening logistics, as well as massively emphasizing digital defenses and the human element. True supply chain vulnerability protection integrates people, processes, and technology into one unified strategy.
Your goal isn't to create an unbreakable supply chain—that's impossible. The goal is to build one that can bend without breaking, recover quickly, and adapt to the next unforeseen challenge.
Ready to move from vulnerability to resilience? A comprehensive security assessment is the first step toward fortifying your digital supply chain against modern threats. Contact us to see how we can help you build a more secure and resilient operational future.