Summary: Explore 15 key malware threats, their business risks, and best practices to detect, prevent, and respond with stronger cybersecurity strategies.
Malicious software (malware) is no longer limited to annoying pop-ups or harmless viruses. It’s a sophisticated threat that targets sensitive data, corporate networks, and mobile devices. All businesses are at risk of malware attacks, as well as data leaks and service disruptions.
According to recent reports, malware attacks have risen dramatically, causing millions in financial loss and operational downtime each year. Organizations underestimating that threat can face severe reputational damage, regulatory fines, and lost trust.
Understanding types of malware attacks is the first step toward prevention. In this article, we’ll explore different types of malware that businesses need to know, explain how they work, and share practical strategies to prevent malware infections.
What is malware?
Malware, short for malicious software, is any program or code designed to infiltrate, damage, or gain unauthorized access to computer systems. Unlike a harmless application, malware is explicitly intended to steal sensitive information, disrupt operations, or compromise security.
Malware is a major business threat because it can:
Cause financial loss through ransomware, fraud, or regulatory fines
Interrupt daily operations, from network downtime to blocked workflows
Damage a company’s reputation, compromise sensitive data, or trigger publicized breaches by exploiting vulnerabilities.
It spreads through various channels, including phishing emails, infected devices, software vulnerabilities, malicious websites, and compromised remote access credentials. Often, exploiting a single software vulnerability in an exposed service is all an attacker needs to gain an initial foothold.
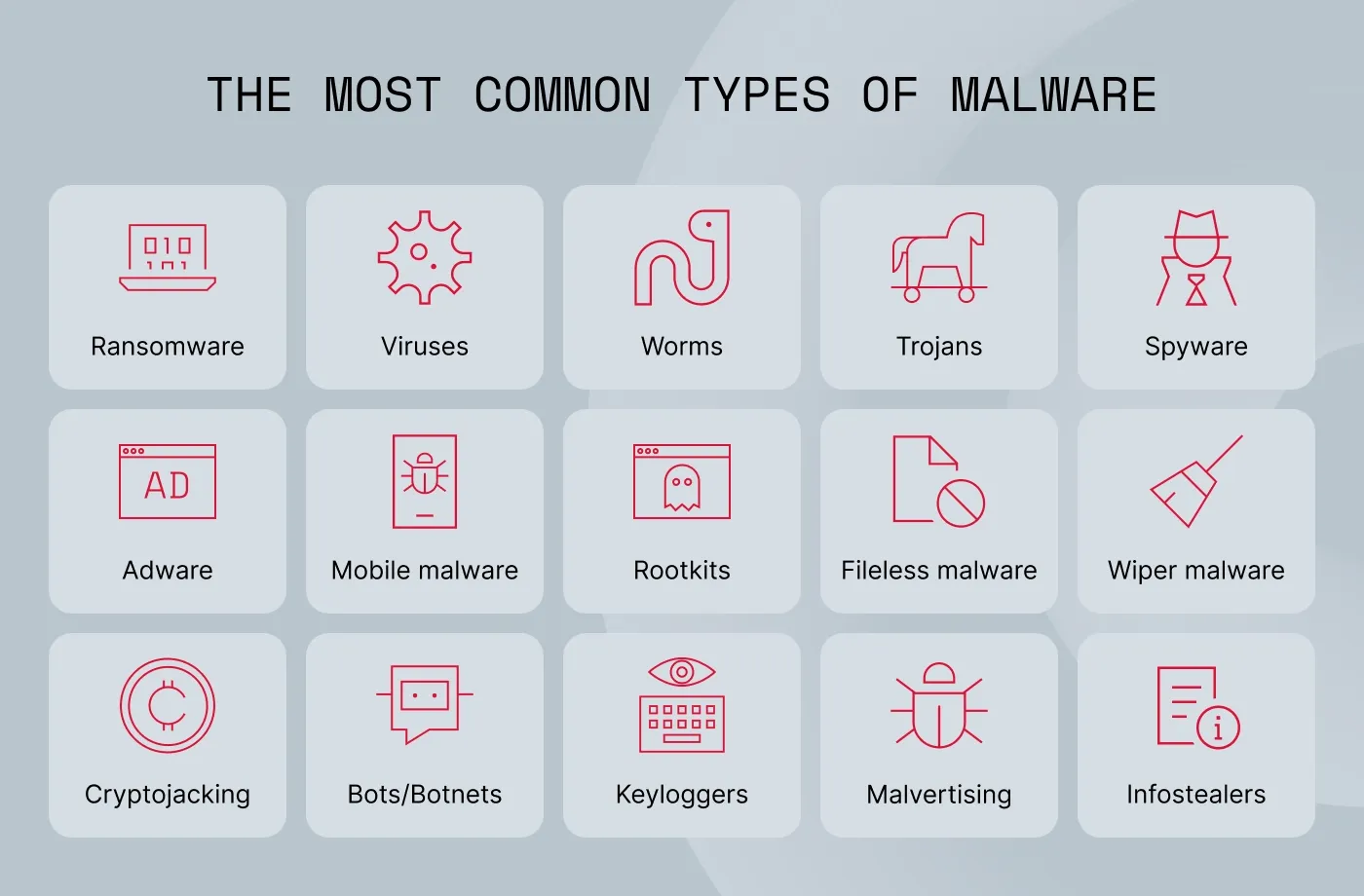
Next, let’s examine the 15 different types of malware—a list of threats that businesses encounter most frequently.
Ransomware
Ransomware is the digital equivalent of a kidnapper locking up your files and demanding payment. It is often delivered via phishing emails or malicious files and can encrypt business data and halt operations.
High-profile examples include WannaCry and Ryuk. Ransomware is one of the most common types of malware and continues to develop, making prevention a top priority for businesses.
Viruses
Viruses are classic malicious programs that attach themselves to files and spread when those files are shared. They can corrupt important documents, slow systems, or completely destroy essential business data. Early examples like ILOVEYOU and Melissa caused widespread destruction.
The 1999 Melissa virus, for example, used email attachments to overload corporate servers, while the 2000 ILOVEYOU worm overwrote personal files on a massive scale. However, modern variants hide in email attachments or downloads from compromised websites.
Worms
Worms are self-replicating programs that spread across networks without any user interaction. They exploit software vulnerabilities to spread, often overwhelming systems and enabling other malware attacks. Famous worms like SQL Slammer and Blaster caused major network disruptions worldwide.
Trojans
Trojans masquerade as legitimate software but secretly carry harmful code. Once installed, they can access business-critical data, install backdoors, or allow attackers to control infected systems. Zeus and Emotet are notorious examples that have targeted businesses globally.
Spyware
Spyware quietly monitors user behavior and transmits confidential information back to attackers. It can steal password data, track online activity, and even record business communications. Tools like FinFisher and Pegasus highlight the risks, emphasizing the need for proactive monitoring and anti-malware software.
Adware
Adware bombards users with unwanted advertisements and can secretly collect data. While often seen as less destructive, it slows devices, distracts employees, and can act as a gateway for malware attacks.
Fireball and DollarRevenue are prominent examples. The Fireball adware hijacked users’ browsers and could download other malware, while DollarRevenue was known for tracking browsing activity to deliver targeted pop-up ads.
Rootkits
Rootkits burrow deep into operating systems, hiding other malicious programs from detection. They can gain unauthorized access and remain undetected for months, often bypassing traditional antivirus software. The NTRootkit, for example, was an early tool that demonstrated how to hide malicious files and processes on Windows systems. More famously, the Stuxnet worm used a rootkit to conceal its presence while physically damaging industrial machinery.
Fileless malware
Unlike traditional malware that hides in files and executables, diskless malware lives in memory, leaving few traces on disk. It exploits legitimate system processes to execute malware, making detection difficult.
For instance, the Poweliks Trojan stored malicious code directly in the Windows registry to perform click fraud, while PowerGhost used legitimate scripting tools like PowerShell to install cryptocurrency miners across corporate networks. Examples like PowerGhost and Poweliks highlight the need for behavior-based security monitoring.
Bots/Botnets
Bots are infected devices controlled remotely, forming botnets for coordinated attacks. Botnets can launch DDoS attacks, distribute spam emails, or propagate ransomware across computer networks. Mirai and Emotet botnets demonstrate how a single infected device can become part of a much larger threat.
Keyloggers
Keyloggers record keystrokes to steal credentials and other confidential information. They operate silently and capture credentials and sensitive communications. Ghost Keylogger and Ardamax are well-known examples that emphasize the importance of security software and multi-factor authentication.
Malvertising
Malvertising spreads malware through online advertisements, even on legitimate sites. Ads can deliver malicious scripts without any user action. Threats like Angler and RIG exploit kits show that even routine browsing can spread malware if users aren’t cautious.
Cryptojacking
Cryptojacking hijacks computing resources to secretly mine cryptocurrency. It slows devices, increases energy costs, and reduces overall productivity. Scripts like Coinhive illustrate how attackers can exploit compromised devices for profit without the user noticing.
Mobile malware
Mobile malware targets smartphones and tablets, often via malicious apps or links. It can steal data, track location, or gain access to corporate accounts. Joker and FluBot are prominent examples that highlight the growing risk for mobile endpoints.
The Joker malware, for instance, has repeatedly bypassed app store security to commit billing fraud by secretly subscribing users to premium services. And the FluBot banking trojan spreads rapidly through fake package delivery text messages to steal financial credentials from infected devices.
Wiper malware
Wiper malware destroys files and disrupts operations entirely. Unlike ransomware, it doesn’t ask for payment—it simply erases data. Shamoon and NotPetya demonstrate how wipers can cause catastrophic business interruptions if defenses aren’t in place.
The Shamoon wiper, for instance, destroyed data on over 30,000 workstations in a single attack targeting the energy sector. In 2017, the NotPetya attack disguised itself as ransomware while permanently destroying data, causing billions of dollars in damages and severe interruptions for major global corporations.
Infostealers
Infostealer malware is a type of malicious software that steals sensitive information from infected devices. It quietly gathers login credentials, session cookies, banking details, personal files, and cryptocurrency wallet data. Attackers then bundle this data into a "stealer log" and sell it on underground forums or illicit Telegram channels, which can be used in attacks such as account takeovers or financial fraud.
Notorious examples, such as RedLine Stealer and Raccoon Stealer, often spread through fake software downloads or malicious email attachments, directly leading to credential theft and data breaches.
Bonus: Hybrid malware
Hybrid malware combines traits of multiple malware types for maximum impact. For example, Emotet acts as both a Trojan and a worm, stealing data while spreading across networks. Because hybrid strains merge different common types of malware, they’re harder to detect and demand a stronger security strategy. These complex threats require anti-malware protection and vigilant monitoring to prevent infections.
Because malware continues to develop (from traditional viruses to fileless and hybrid strains) businesses can’t rely on outdated defenses. To counter these threats effectively, organizations need proactive, layered security practices.
Best practices to prevent and detect malware in business systems
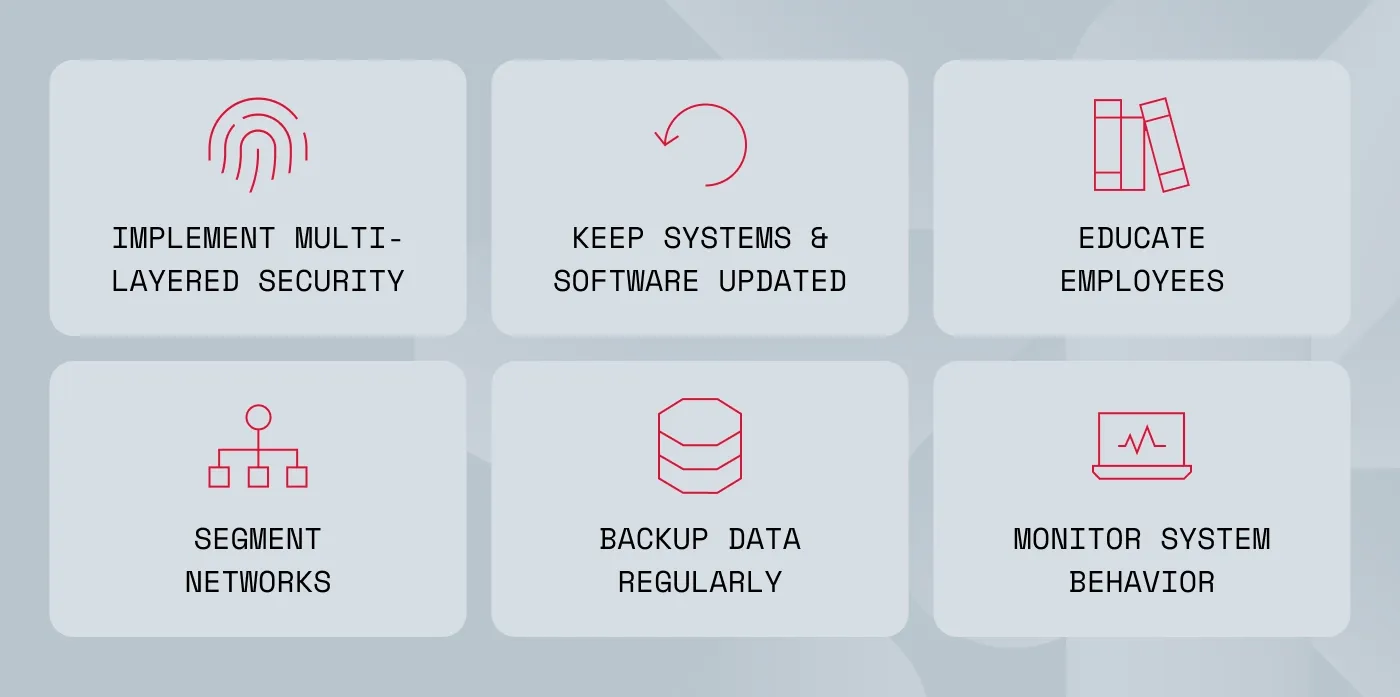
Malware prevention is not a one-time setup. Rather, it’s a continuous effort combining people, processes, and technology. Here are practical steps businesses should follow:
Implement multi-layered security. Use a combination of antivirus software, anti-malware protection, firewalls, and intrusion detection systems. Layered defenses ensure that even if one barrier fails, others are ready to stop the attack. This approach also helps defend against advanced threats like hybrid malware, which combines different attack vectors.
Keep systems and software updated. Regular patching closes vulnerabilities that malware exploits. Automating updates reduces the risk of human error, ensuring that no critical patch is missed. Attackers often target outdated software first, so this step is one of the most cost-effective defenses against common types of malware.
Educate employees. Train staff to spot phishing emails, malicious links, and suspicious attachments. Reinforce this with simulated phishing exercises and regular security reminders. Cybercriminals often trick users with fake login pages or fraudulent messages during phishing attacks, making awareness training critical.
Segment networks. Separate systems and control access to limit malware spread. This ensures that even if one endpoint is infected, the rest of the environment remains safe. Network segmentation is especially effective against worms and ransomware, which rely on lateral movement across systems.
Backup data regularly. Maintain offline or unchangeable backups to recover from ransomware attacks or wiper malware. Test restoration processes frequently to ensure that backups are not corrupted or outdated. A strong backup strategy not only minimizes downtime but also prevents attackers from holding your data hostage.
Monitor system behavior. Look for unusual CPU usage, unexpected network traffic, or unknown processes. Implement behavior-based monitoring tools to detect diskless malware, which doesn’t leave traces on disk. By catching early warning signs, businesses can stop small incidents before they become full-blown breaches.
Strong security measures provide the foundation, but true resilience comes from visibility: understanding your assets, monitoring for risks, and aligning defenses with how attackers actually operate.
Related articles

NordStellarJun 17, 20259 min read
Key priorities for modern malware defense
Beyond specific tools and processes, organizations need to focus on several strategic priorities to stay resilient against malware threats.
Visibility is key. Know where critical information resides, which systems are exposed, and how employees interact with data. Proper risk assessment and continuous monitoring ensure malware threats are identified and mitigated before they escalate.
Regulatory compliance and insider risk management matter. Technical controls must be paired with clear policies, role-based access, and ongoing awareness programs to reduce human error and meet audit requirements.
Modern detection beats legacy signatures. Traditional antivirus programs often miss fileless malware and sophisticated hybrid attacks. Modern detection tools block malicious code, monitor real-time threat exposure, and protect enterprise networks and mobile devices proactively.
Focus on surface and supply-chain risk. This is where practices like attack surface management and supply chain security are needed: they help you spot exposed services, vulnerable dependencies, and third-party signals that threaten your environment.
How NordStellar can help
NordStellar is a threat exposure management platform that gives security teams clear, actionable visibility and prioritized guidance. Key ways it helps security teams prevent or reduce malware damage:
Credential monitoring. Alerting on compromised credentials and credential-related indicators found in breach dumps and
infostealer logs.
Dark web monitoring. Continuously scanning dark web hacker forums and marketplaces, as well as Telegram channels, for mentions of your brand, assets, or attack indicators.
Attack surface management. Identifiying exposed assets, misconfigured services, and known software vulnerabilities (CVEs) across your external footprint.
Threat prioritization. Highlighting which findings matter most by adding context: what was discovered, how critical it is, and where to focus first.
NordStellar integrates into existing workflows and SIEMs, turning threat visibility into practical, measurable defense without overwhelming teams.
Conclusion
Malware remains one of the most pervasive and costly cyber threats to businesses. From ransomware attacks to fileless malware, organizations face constant risk to their sensitive data and operations.
Understanding the different types of malware and implementing best practices reduces risk, strengthens business resilience, and ensures continuity. Stay proactive, because in cybersecurity, prevention is always better than a cure.
Prevent malware damage, detect threats early, and protect sensitive data with NordStellar. Contact us today to secure your business.
FAQ
What is the hardest type of malware to detect?
Fileless malware is extremely challenging to detect because it operates in memory rather than on disk, leaving minimal traces for traditional antivirus or software to find. It often exploits legitimate processes, making it nearly invisible to conventional scanning.
Detecting fileless malware requires behavioral monitoring and real-time threat intelligence to catch unusual system activity before it escalates.
What is the most dangerous type of malware?
Ransomware is considered one of the most dangerous types of malware in cybersecurity. When combined with hybrid threats, it becomes even more destructive, encrypting critical files, halting business operations, and demanding payment to restore access.
This results in severe financial, operational, and reputational damage. Unlike many other malware types and examples, ransomware directly disrupts business continuity and spreads quickly across networks and devices.

Agnė Srėbaliūtė
Senior Creative Copywriter
Agne is a writer with over 15 years of experience in PR, SEO, and creative writing. With a love for playing with words and meanings, she crafts content that’s clear and distinctive. Agne balances her passion for language and tech with hiking adventures in nature—a space that recharges her.