Summary: A vulnerability assessment is the proven method for finding vulnerabilities in your IT infrastructure, which helps you protect your business from cyberattacks.
Just because you can’t see a cyber threat doesn’t mean it isn’t there. The truth is, your network or systems could have flaws or weaknesses that you aren’t even aware of. If attackers find them, the fallout can be devastating—we’ve all seen the headlines about big companies losing millions of dollars as a result of breaches.
So, how do you stop your business from becoming the next victim? You need to identify and fix any issues before they can be exploited. This is where a vulnerability assessment is the essential first step.
What is a vulnerability assessment?
A vulnerability assessment is the process of identifying, quantifying, and prioritizing the security vulnerabilities within your organization's IT infrastructure. In other words, it’s a comprehensive security check-up for your network, systems, and applications to discover potential vulnerabilities before they can be exploited by malicious actors.
This systematic approach to finding weaknesses in IT infrastructures goes beyond creating a simple list of flaws. It gives you a clear, actionable plan to strengthen your defenses by helping you understand and prioritize the risks posed by each identified vulnerability.
As a result, you can significantly reduce the likelihood of a security breach, ensuring your business remains secure and compliant with critical standards like ISO 27001 and the NIST Cybersecurity Framework.
Common types of vulnerability assessments
A thorough security strategy involves assessing every part of your IT environment for risks. Here are the most common types of vulnerability assessment:
Network-based assessment
This type involves scanning your network infrastructure (servers, firewalls, routers) for open ports, misconfigurations, and other known flaws. It provides an external view of your security posture and helps identify how an attacker could gain entry to your company network.
Host-based assessment
A host-based assessment goes a bit deeper, taking a really close look at individual hosts like servers and workstations. It involves vulnerability identification in operating systems, software configurations, and user permissions, providing a detailed internal view of a system’s security.
Wireless network assessment
As you can guess, this particular type focuses on your wireless networks and access points. It checks them for weak encryption, unauthorized access points, and other misconfigurations that could allow an attacker to intercept data or gain access to your organization’s network.
Application-based assessment
As the name suggests, application vulnerability assessment focuses specifically on testing web applications for vulnerabilities. It looks for coding flaws and misconfigurations that could lead to issues like SQL injection or cross-site scripting (XSS), which are common attack patterns.
Database assessment
Databases are often the most valuable targets for attackers, and so they must also be scanned for vulnerabilities. A database assessment checks for weaknesses in database management systems, such as weak passwords, unpatched software, and insecure configurations, to prevent unauthorized access to critical business data.
Cloud infrastructure assessment
With more and more organizations moving to the cloud, a cloud infrastructure assessment is vital. It helps identify security gaps and misconfigurations in your cloud services (e.g., AWS, Azure) that could expose your company data or systems to unauthorized access.
How to successfully perform a vulnerability assessment
A vulnerability assessment is a clear, structured process. By following a proven framework, you ensure a thorough review of your systems and receive actionable results. Here’s how:
Preparation. Before you begin, define the scope and objectives of the assessment. Identify your most critical assets and systems. Then, choose and configure the appropriate vulnerability assessment tools for the task.
Scanning. Use your chosen tools to perform
vulnerability scanning across your defined scope. The goal is to create a comprehensive list of all identified weak spots.
Vulnerability analysis. Once you have the raw data, you need to analyze it. This involves removing false positives, grouping similar findings, and getting a clear picture of the actual security vulnerabilities in your company's systems and networks.
Risk assessment. This is a critical step where you evaluate the risk each vulnerability poses to your organization. Use a combination of technical scoring and business context to prioritize your findings.
Remediation. Based on the risk assessment, you can create and execute a plan to fix the vulnerabilities you've identified. This might include applying software patches, reconfiguring systems, or adopting entirely new security measures. After the remediation phase, it's also good to re-scan your systems to confirm all fixes.
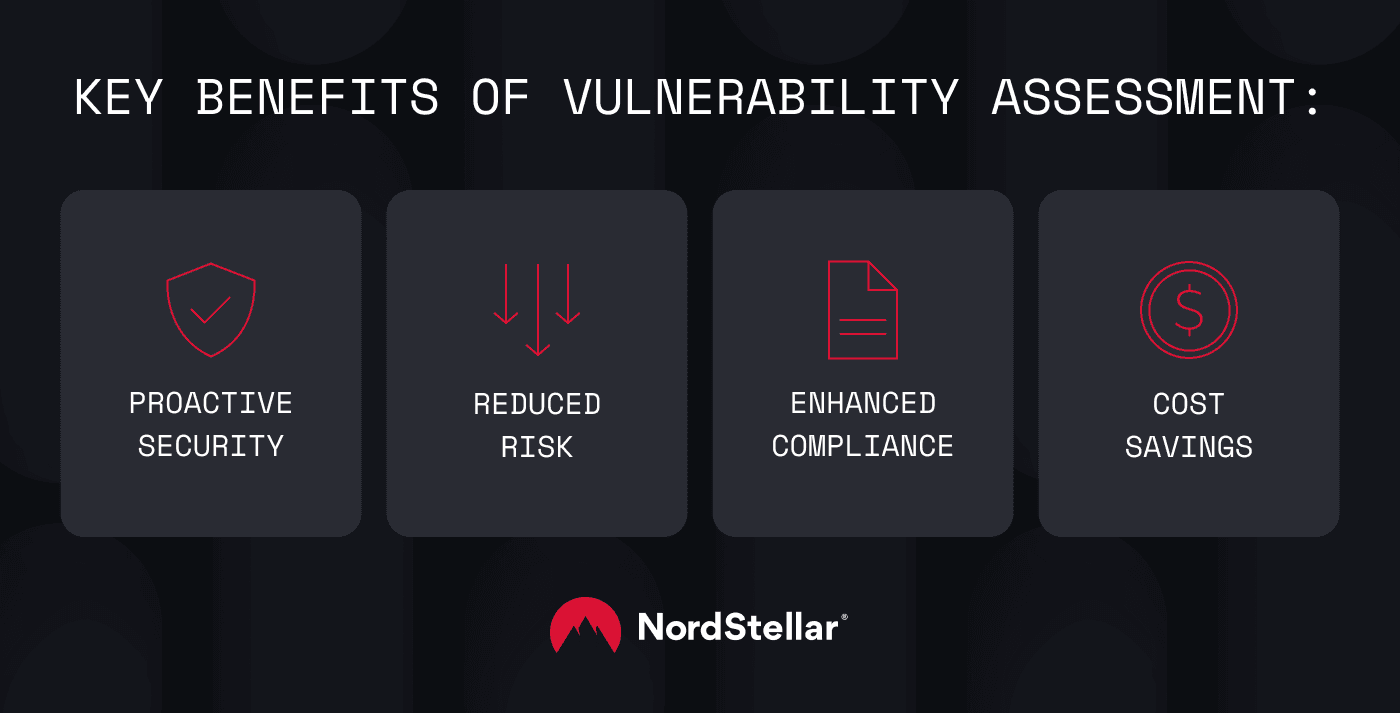
Benefits of vulnerability assessment
Based on what we've covered so far, you can probably imagine that the benefits of using vulnerability assessment tools are significant and far-reaching. Let’s look at some of the most important ones:
Proactive security: It helps you find and fix weaknesses before a threat actor can exploit them, preventing a security breach.
Reduced risk: By addressing vulnerabilities, you lower the overall risk of data loss, financial damage, and reputational harm.
Enhanced compliance: It’s a key requirement for many regulations and industry standards, helping you avoid costly fines and legal issues.
Cost savings: Avoiding a security breach saves more money than fixing the damage it can cause.
Key challenges organizations face when conducting vulnerability assessments
While a vulnerability assessment offers clear benefits, the process isn't always straightforward. Here are a few common issues that can arise:
High complexity of IT environments: Modern IT systems are intricate and constantly changing. This makes it difficult to maintain an accurate scope for assessments. Consequently, it becomes a challenge to track all assets and their interdependencies, leaving potential gaps in coverage.
Dealing with false positives: Manually verifying every identified vulnerability can be time-consuming and resource-intensive. Sometimes, this can distract security teams from addressing critical vulnerabilities that pose an immediate threat to the company.
Prioritization paralysis: A long list of things requiring fixes can be overwhelming for any team, making it extremely hard to decide where to start the repair process. Without a clear prioritization framework, businesses might fix low-risk issues while high-risk ones remain exposed.
Limited resources: Many organizations, especially small businesses, lack the in-house expertise or budget to conduct thorough assessments. This often leads them to rely on a less-effective, one-off security check-up or to skip the process altogether.
Acting on assessment results: Ensuring the findings are acted upon and remediated effectively can be challenging. This requires strong coordination between security, IT, and development teams to implement fixes without disrupting business operations.
Related articles

Anastasiya NovikavaAug 26, 202511 min read

NordStellarJul 1, 202513 min read
Best practices for keeping your company’s cybersecurity in check
A vulnerability assessment should not be a one-off activity. It’s an ongoing process that is fundamental to a mature security program. Here's how to maintain continuous security:
Schedule regular security scans
Regular, automated scans—daily, weekly, or monthly—are crucial for maintaining continuous cybersecurity of your company. They allow you to catch new vulnerabilities as soon as they emerge, ensuring your defenses are always up-to-date.
This proactive approach ensures that monitoring your security posture doesn't become a one-time event, but rather provides a constant stream of data for your vulnerability assessment report.
Combine with penetration testing
A vulnerability assessment helps you identify weaknesses in systems, while penetration testing employs ethical hackers to actively exploit them. The goal is to demonstrate what would happen to your company in the event of a successful attack.
Combining both practices, you not only get a list of potential vulnerabilities but also a clear understanding of which ones are most likely to be exploited. A good example of this synergy is a company using scans to find all possible flaws, then running penetration testing on the most critical systems identified in their vulnerability assessment report.
Train your staff
By training your team to identify and report suspicious activities and to use vulnerability assessment tools, you enable them to act as a human firewall. Including regular training and simulated phishing exercises on your vulnerability assessment checklist can significantly reduce the risk of a security breach caused by human error.
Keep all your tools and systems up-to-date
There's a saying that goes: "Your security is only as strong as your weakest link." So, make sure all your software and systems, including your vulnerability assessment tools, are always patched and updated. Failing to apply the latest security updates can expose your systems and make your entire infrastructure an attractive target for cybercriminals.
Don't forget about performing external vulnerability scans
Many of the most damaging cyberattacks begin at your network’s perimeter—the point where it connects to the internet. That’s why securing your external attack surface is critical to protecting your business. A key part of this is external vulnerability scanning, which focuses on internet-facing assets like your website, public servers, and external IP addresses.
This is where NordStellar comes in. As a threat exposure management platform, its external vulnerability scanner is designed to detect flaws in the internet-facing parts of your network. Acting like a search engine for connected devices, it maps your digital footprint and flags vulnerabilities—from open ports and outdated software to misconfigurations and unprotected APIs—before attackers can exploit them.
Take action to find and fix your cybersecurity vulnerabilities. Contact the NordStellar team to get started with external vulnerability scanning.
Frequently asked questions (FAQ)
What’s the difference between vulnerability scanning and penetration testing?
Vulnerability scanning is a cybersecurity research method that helps you identify vulnerabilities in your systems, networks, and applications, basically giving you a list of potential issues.
Penetration testing, on the other hand, is a manual process where ethical hackers actively attempt to exploit vulnerabilities in a company's IT infrastructure to demonstrate the real-world impact of a successful attack.
Who is responsible for running vulnerability assessments in a company?
While the IT or cybersecurity team typically performs the technical work of the vulnerability assessment, the ultimate responsibility for managing the overall risk and ensuring remediation lies with business leadership. In other words, it’s a shared responsibility that requires communication between technical teams and management.
How often should vulnerability assessments be performed?
The frequency of running vulnerability assessment processes depends on several factors, including the industry in which your company operates, applicable compliance requirements, and the sensitivity of your company's data. However, as a best practice, you should conduct a comprehensive vulnerability assessment at least quarterly and perform regular, automated scans (daily or weekly) on your most critical systems.
Is vulnerability assessment part of compliance standards?
Yes, many major compliance standards and regulations, such as PCI DSS, HIPAA, and GDPR, require organizations to conduct regular vulnerability assessments as part of their security programs.

Maciej Sikora
Senior Copywriter
A man on a mission to engage audiences with creative wordplay, Maciej knows every complex idea can be broken down into simple words—and that’s his driving force. When he’s not writing, you’ll find him making music, taking a walk with his dog, or watching yet another movie.