
Anastasiya Novikava
Copywriter
Anastasiya believes cybersecurity should be easy to understand. She is particularly interested in studying nation-state cyber-attacks. Outside of work, she enjoys history, 1930s screwball comedies, and Eurodance music.
Dark web

Summary: The group behind DarkSide may be gone, but its tactics live on. Learn about their methods, risks, and how to build a resilient defense.
Ransomware is now one of the most damaging threats to organizations. The financial toll is staggering. In 2023 alone, victims paid more than $1 billion in cryptocurrency to ransomware actors. In 2024, although payments dropped roughly 35% to about $813 million, the sheer volume of ransomware attacks stayed high. In fact, the 2025 statistics show that ransomware is now a factor in 44% of breaches (DBIR).
What fuels this criminal industry is a ruthlessly efficient model: ransomware-as-a-service (RaaS). It works much like any other software service. A core group of developers builds software (in this case, malware) and portals. And “affiliates” handle the attacks for a share of the profits. This model puts RaaS into more hands, making ransomware a constant danger for businesses everywhere.
In this article, we’ll tell the story of DarkSide, one of the most notorious ransomware groups, and its rise and fall.
The real-world impact goes beyond the ransom itself. In a few days, operations can grind to a halt, supply chains can be disrupted, and a company's reputation can be damaged.
No case illustrates this better than the Colonial Pipeline ransomware attack. This incident shows how a well-organized ransomware group can bring critical infrastructure to its knees. DarkSide, the group behind this attack, perfected the RaaS model, showing how effective it could be against large organizations.
When DarkSide hit Colonial Pipeline, the company shut down its IT systems and halted fuel distribution across the eastern United States. The company paid 75 bitcoin (about $4.4 million at the time), and the U.S. Department of Justice later recovered 63.7 bitcoin from the attackers’ wallet. This incident reveals how ransomware can disrupt an organization and create reputational and financial fallout in days.
So, what is DarkSide? The DarkSide hacker group first appeared in 2020 with professional tooling, a public “press center,” and a victim shaming site. The group, believed to be Russian-speaking, quickly built a reputation for “big game” targets and smooth operations, including stable decryptors, redundant leak infrastructure, and support chats for victims.
DarkSide ransomware-as-a-service model was central to its operations. Core operators developed the malware and leak site, while vetted affiliates executed intrusions and shared revenue. After gaining access, these affiliates exfiltrated data, deployed encryption, and used the group’s TOR-based negotiation portals.
Demands varied from hundreds of thousands to multi-million-dollar sums. Negotiations happened in web chats where DarkSide weighed the victim’s financials and threatened timed data releases to increase pressure. Some victims negotiated down sizable percentages before paying. For example, Brenntag, a global chemical distributor, reportedly reduced a 133.65 BTC demand and paid $4.4 million.
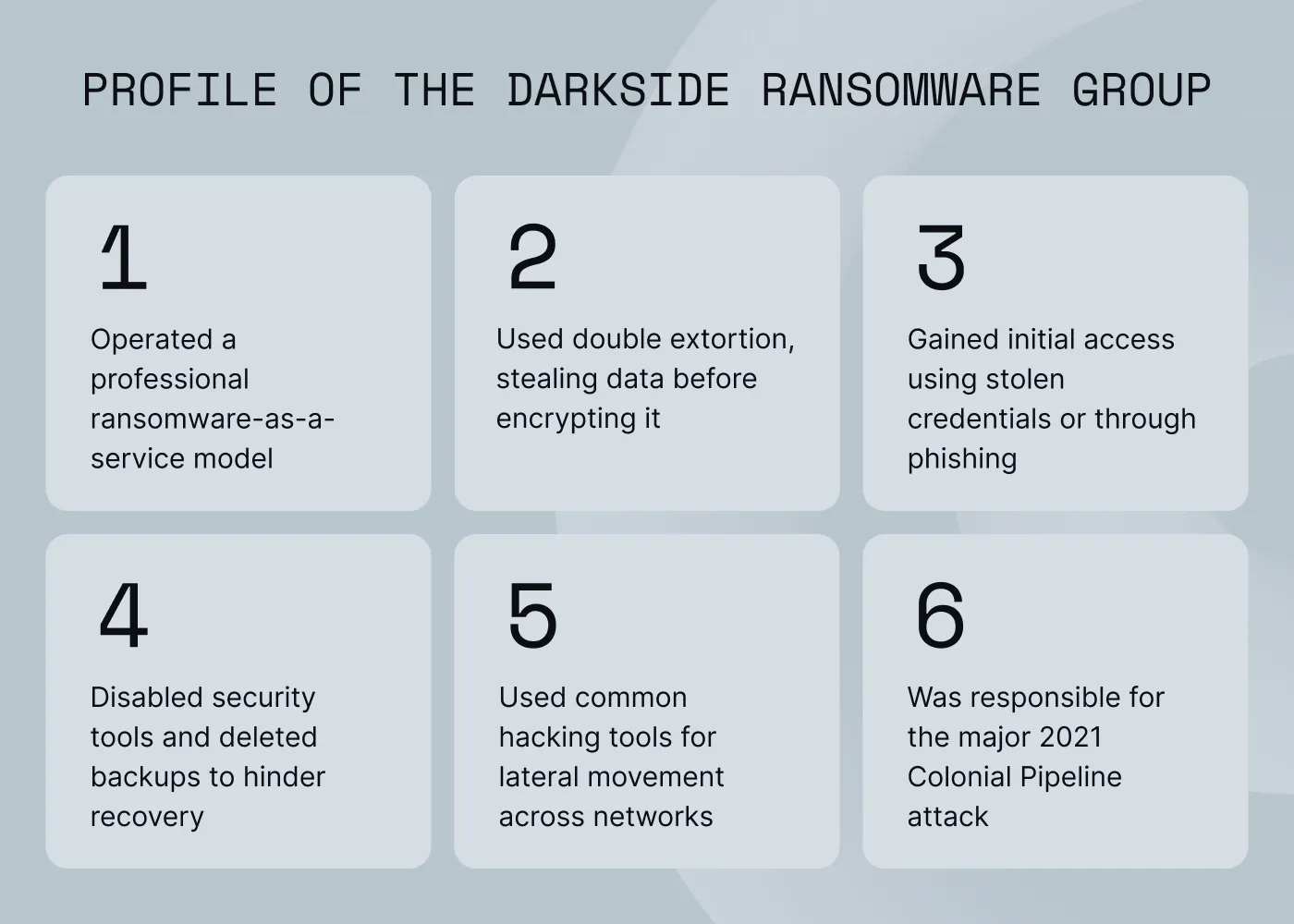
DarkSide affiliates typically obtained remote access through stolen credentials or purchased access from initial access brokers. Exposed RDP or VPN services and phishing continued to feature in many cases.
Once inside, they moved laterally with off-the-shelf tools such as PSExec or Cobalt Strike, enumerated the network, identified backups, then staged exfiltration and ransomware deployment.
On hosts, the DarkSide malware used Salsa20 for file encryption with RSA-1024 to protect keys. Operators commonly disabled security tools, stopped services, deleted volume shadow copies to block recovery, and used TOR for command-and-control and negotiation portals.
Defenders should watch for telltale steps such as:
Public advisories also document DarkSide’s use of RDP for persistence and its double-extortion playbook.
After the scrutiny following the Colonial Pipeline attack, the DarkSide group said its servers and cryptocurrency were seized and declared it would shut down. Within weeks, a new ransomware-as-a-service brand, BlackMatter, emerged. It was assessed as a DarkSide successor that “learned from” the backlash.
The cycle repeated across the ecosystem. For example, many researchers treat ALPHV/BlackCat as a later successor in the DarkSide lineage via rebrands and overlapping affiliates. ALPHV/BlackCat claimed a law-enforcement takedown in March 2024 that experts judged as an exit scam. This pattern shows how resilient the ransomware-as-a-service market is even under strong pressure.
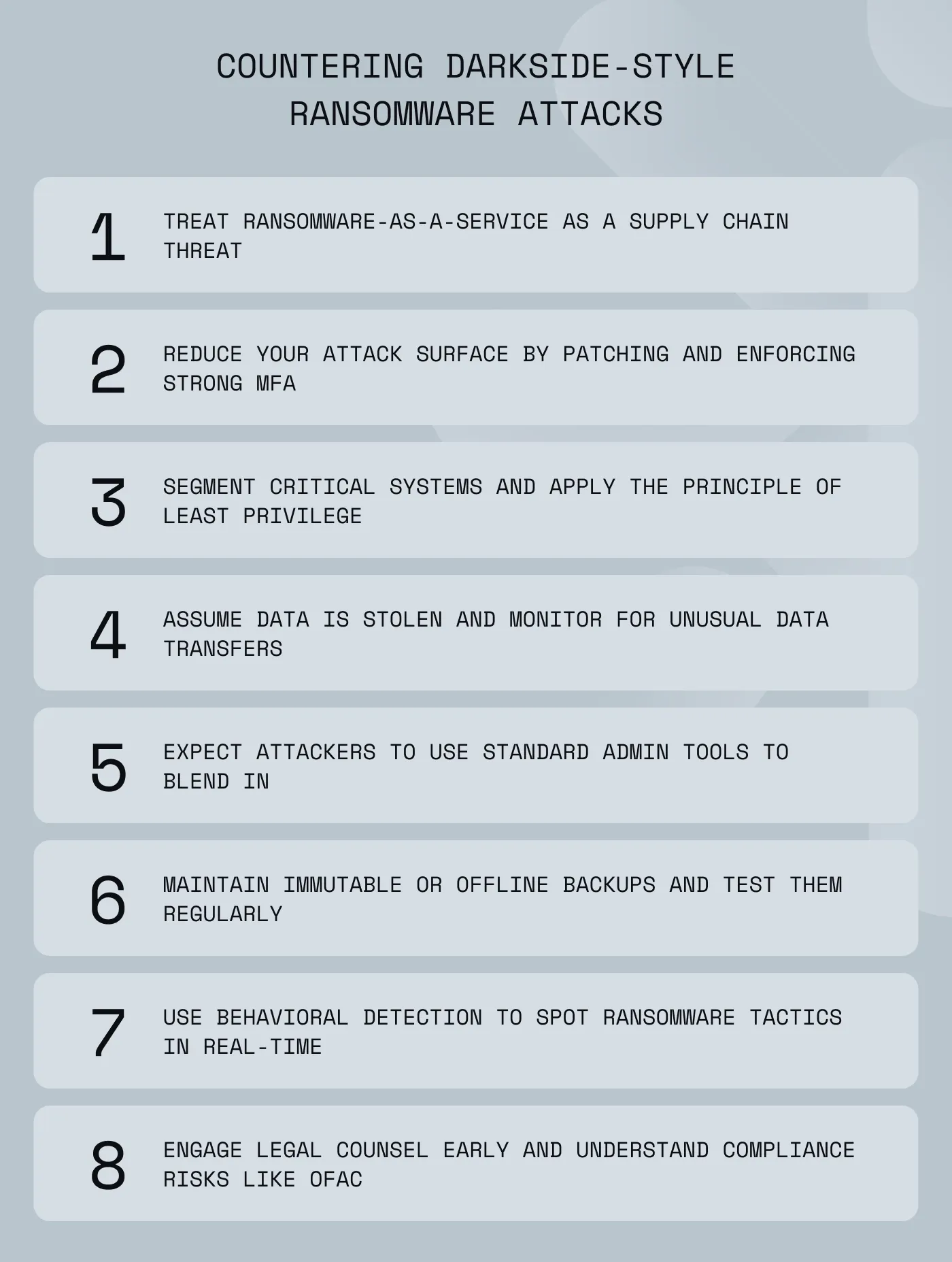
First, it is essential to treat ransomware-as-a-service as a supply chain. This means focusing on disrupting the initial stages by blocking initial access brokers. Organizations can force attackers to work harder up front by reducing exposed services, closing phishing paths, and enforcing strong multi-factor authentication (MFA) coverage.
Alongside preventative measures, defenders must assume data theft before encryption by logging and alerting on unusual data staging, archiving, and egress to cloud storage providers.
Security teams must expect living-off-the-land tactics. Baselining the normal use of tools like PowerShell, WMIC, PSExec, and RDP is crucial to spotting malicious spikes or the use of admin tools from non-admin workstations.
It’s also vital to keep recovery realistic. Attackers methodically remove shadow copies and target backups to prevent restoration, so the most effective countermeasure is to design immutable or offline backups and test restores regularly.
Finally, organizations need to plan for negotiation outcomes. A difficult reality of ransomware attacks is that payment does not guarantee clean data return or deletion. Even when victims pay, some actors re-extort them or leak the data anyway.
Build a layered defense approach:
Advanced monitoring and threat detection must look for both attack precursors and active deployment steps. Organizations should deploy behavioral detection that flags ransomware tactics in real time, such as bulk file renames, suspicious archive creation, and mass Volume Shadow Copy (VSS) deletions. At the same time, security teams should watch for the indicators that DarkSide-style affiliates use, including credential theft, abnormal RDP activity, and PSExec lateral movement.
External visibility is just as critical. Organizations can use dark web monitoring to track group chatter that references their company or suppliers. For example, NordStellar monitors dark web forums and ransomware blogs for mentions of your domains, employee emails, and brand. It alerts you if your data appears online so you can respond before extortion escalates.
Ransomware attacks introduce serious legal and compliance risks. Engage legal counsel early in any incident. If a sanctioned actor may be involved, U.S. companies face strict liability risk under OFAC rules, even when a third party facilitates the payment. You must document your diligence, report the incident to law enforcement, and evaluate licensing paths where applicable.
You also need to track jurisdictional rules. The UK has announced plans to ban ransomware payments by public bodies and critical national infrastructure, and other governments are reviewing similar proposals. Adjust your crisis communications and board approval processes.
Cyber insurance can offset the costs of incident response, business interruption, and data recovery, but coverage is not guaranteed. To meet policy requirements, you must keep security controls current, notify your carrier quickly after an incident, and follow prescribed forensics and negotiation protocols to avoid disputes.
A service like NordStellar helps organizations face these challenges head-on. The platform provides cyber threat intelligence to spot early signs of an incident, sending alerts that identify leaked credentials. This is a key tool attackers often use to enable remote access.
NordStellar also delivers executive-ready context. It monitors leaked credentials, data breach details, and relevant dark web intelligence to show how threat actors operate and their techniques. These alerts, via NordStellar’s API, can be integrated with SIEM and SOAR platforms. Each alert is categorized by risk levels and incident timeline details, allowing security teams to act quickly.
Even if ransom payment totals fall, the pressure from ransomware persists. Groups rebrand, affiliates rotate, and the tactics that made the DarkSide ransomware group effective continue to pay off for its successors. Proactive security, rehearsed recovery plans, sanctions-aware decisions, and constant exposure monitoring ultimately separate a bad day from a business-ending crisis.
The difference between a manageable incident and a crisis often depends on early warning. See how attackers view your organization and get alerted before extortion escalates. Contact NordStellar to see our dark web monitoring and exposure intelligence in action.