Summary: LockBit ransomware automated attacks can paralyze systems in minutes. Discover how this self-piloted threat works and the specific steps to stop it.
Encrypted data, locked systems, and a demand for a double ransom payment. That is the reality of a LockBit ransomware attack. Since 2019, the group behind this malicious software has turned cyber extortion into a streamlined, high-speed business model that outpaces almost every competitor in the digital underworld.
LockBit is a "self-piloted" cyber-attack. Once deployed, it automates everything from vetting for valuable targets and spreading laterally through networks to encrypting systems with terrifying efficiency.
While other ransomware groups vanish, the LockBit gang persists by operating like a legitimate software vendor, constantly updating its product. In this article, we will unpack how this criminal enterprise operates, why its automation makes it so dangerous, and the specific strategies you need to defend your organization.
Key takeaways
LockBit operates as a Ransomware-as-a-Service (RaaS) model, where the developers of this malicious malware rent it to affiliate hackers.
It uses lightning-fast encryption that locks only parts of a file, paralyzing a system in minutes—much faster than its competitors.
LockBit automates the attack. Once inside, it goes on autopilot, spreading across the network without human help.
It uses double extortion. Attackers demand a ransom to restore access to data and a second ransom to prevent the leak of stolen data on the dark web.
Protecting your organization against LockBit ransomware demands strict access controls, offline backups, and
continuous attack surface management.
What is LockBit ransomware?
LockBit ransomware is a malicious software that encrypts a system and blocks user access in exchange for a ransom payment. However, to understand this threat, we must look past the code to the organization behind it.
LockBit operates as a Ransomware-as-a-Service (RaaS). The core gang creates the malware and manages the infrastructure, while "affiliates"—hired hackers, network access brokers, and company insiders—find the targets and deploy the payload.
To attract top talent, the group offers a lucrative split, with affiliates receiving up to 75% of the ransom funds. The LockBit ransomware group has also collaborated with other criminal entities, such as the now-defunct Maze, and has established itself as one of the most professional ransomware groups.
What makes LockBit truly dangerous, however, is its efficiency. The malware is "self-piloted," meaning it automates the most critical stages of an attack. Once inside a network, it automatically vets for valuable targets, spreads the infection laterally, and executes double extortion by exfiltrating sensitive data before encryption takes place.
This automated nature removes the human bottleneck, allowing the gang to cast a massive net. It means that any organization with a vulnerability is a potential target—from small businesses to major financial institutions, healthcare providers, and government agencies.
How does LockBit ransomware work?
LockBit is considered part of the "LockerGoga & MegaCortex" malware family, meaning it is targeted rather than scattered like spam, and self-spreading.
What sets LockBit apart is its ability to self-propagate. Unlike older ransomware attacks that require a hacker to navigate a network for weeks manually, LockBit operates on autopilot.
Once LockBit infects a single host, it uses pre-designed scripts to find other accessible devices and spread the infection without human intervention. To remain undetected, LockBit ransomware uses native Windows tools, such as PowerShell, and disguises its malicious code as harmless PNG image files, effectively evading many endpoint security systems.
How a LockBit ransomware attack unfolds
A LockBit attack is a masterclass in automated efficiency. Unlike clumsy, manual hacks that take weeks to unfold, this malware is designed to bypass your defenses quickly. Once it breaches the perimeter, it moves with precise, machine-like speed—escalating privileges, neutralizing security tools, and locking down data before your team even receives an alert.
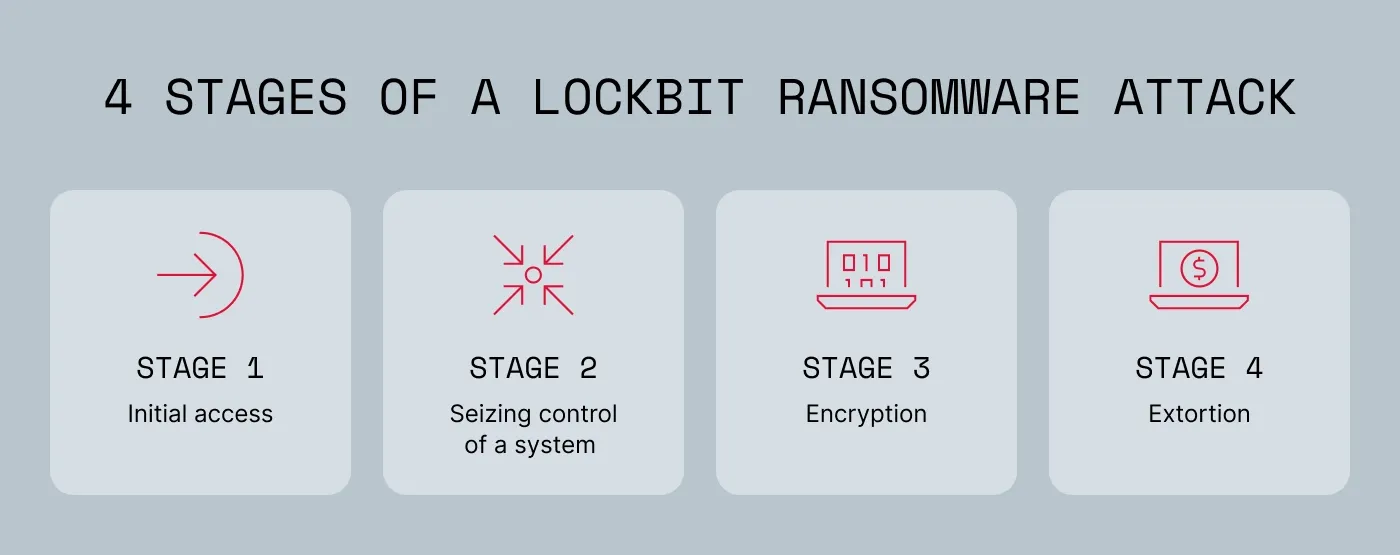
Operation unfolds in four stages:
Stage 1: Initial access
The attack often begins with a quiet intrusion. Attackers exploit software vulnerabilities or use social engineering tactics, such as sending phishing emails that impersonate trusted colleagues, to gain that initial access. Alternatively, they may launch brute-force attacks against weak network configurations to force their way in.
Stage 2: Seizing control of a system
Once inside, the malware takes the wheel. LockBit uses "post-exploitation" tools independently to gain access privileges and move laterally through the network, hunting for high-value assets. It prepares the ground for total devastation by disabling security programs and sabotaging infrastructure that would allow for system recovery.
Stage 3: Encryption
Once the network is compromised, LockBit encrypts files instantly, locking the victim out of their own data without a decryption key. To ensure the message is received (and to add pressure), it drops ransom notes in every system folder.
Stage 4: Double extortion
LockBit doesn't just lock files; it steals them first. This allows attackers to demand two ransoms: one to restore access to your data, and another to stop them from leaking your sensitive information on the dark web.
Related articles

Joanna KrysińskaNov 12, 202512 min read
The evolution of LockBit ransomware
LockBit treats its malware like a commercial software product, following a strict development lifecycle. Since its emergence in 2019, LockBit has mutated through several major iterations, each designed to be faster and more evasive than the last one.
The ".abcd" variant (2019): The original iteration did not yet carry the famous moniker. It was identified by the file extension it used to rename encrypted data: .abcd. This early version left "Restore-My-Files.txt" notes in every folder with restoration instructions.
LockBit 1.0 (Jan 2020): A few months later, the ransomware adopted the LockBit extension. While visually similar to its predecessor, it marked the beginning of the brand's rise in Russian-language cybercrime forums.
LockBit 2.0 (June 2021): This major update introduced "StealBit," a built-in tool for automating data theft. It also shifted tactics by directing victims to a traditional website rather than a Tor link for instructions, in an attempt to make payment easier.
LockBit 3.0 "Black" (March 2022): Borrowing code similarities from rival gangs Black Matter and ALPHV (BlackCat), this variant strengthened LockBit’s position.
LockBit Green (Jan 2023): Demonstrating its adaptability, this version included source code from the disbanded Conti ransomware group.
Cross-platform expansion: The LockBit group has systematically widened its net. In late 2021, it released a Linux-ESXi locker targeting virtual machines, and by April 2023, encryptors targeting macOS had been detected.
Beyond version numbers, LockBit receives continuous updates. Recent changes include the capability to disable administrative safety prompts. This allows the malware to run with higher privileges silently, and a greater focus on double extortion, threatening the public release of private server data if the ransom is not paid.
Protecting your business from LockBit ransomware attacks
LockBit ransomware is a relentless threat, but your organization doesn't have to be an easy target. Law enforcement agencies like the FBI and CISA recommend taking a proactive approach to stopping LockBit attacks before they start.
Here are the essential steps to protect your business from LockBit ransomware:
Build multilayered defenses. Don't rely on a single shield. Use antivirus software and endpoint detection and response (EDR) solutions that can spot malicious activity early. Train your team to recognize the phishing emails that often deliver LockBit ransomware.
Segment your network. Dividing your network into smaller segments can prevent LockBit from spreading to critical systems and causing widespread damage, even if one of your devices is infected.
Control who gets in. LockBit attackers often use stolen credentials. Enforce strong, unique passwords and multi-factor authentication (MFA) to block unauthorized access to your accounts.
Back up data offline. If a LockBit attack happens, backups are your safety net. Store copies of your data offline so you can restore your systems without having to pay the ransom.
Patch vulnerabilities. LockBit usually exploits outdated software to gain entry. Regularly updating your operating systems fixes the security gaps.
Monitor continuously. You can’t stop what you can’t see. Use
threat exposure management solutions like NordStellar to identify the warning signs of a LockBit attack and respond before it causes real harm.
How NordStellar can help you stop LockBit
LockBit ransomware needs a way in. Usually, that path involves a stolen password, an unpatched system, or a convincing phishing email. NordStellar helps you find these weak spots before hackers can exploit them.
Lock down stolen credentials. Hackers often buy stolen logins to walk right past your security defenses. NordStellar’s
dark web monitoring tracks these credentials on criminal forums and marketplaces. If an employee's password is leaked, you receive an instant alert, allowing you to secure the account before an attacker uses it.
Close security gaps. LockBit hunts for outdated software, which is how it opens doors in your network. NordStellar’s
attack surface management maps your infrastructure to spot these vulnerabilities. It shows you
exactly where your technology is exposed so you can fix the issue before it becomes an entry point.
Stop impersonation attempts. Phishing is still one of the most common ways to deliver ransomware. Attackers may fake your website to trick your team or customers. NordStellar’s
brand protection identifies these malicious domains and impersonation attempts, helping you neutralize the threat before anyone falls for the trap.
Stop threats before they get in. NordStellar helps you identify and resolve vulnerabilities before hackers can exploit them to lock your files. Contact the NordStellar team to secure your organization.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she loves explaining complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.