Summary: For NordStellar, 2025 was all about turning threat visibility into control. See how our improved features help businesses stop firefighting and start preventing threats.
Cyber threats certainly didn't take a holiday in 2025, and neither did we. But looking back, it wasn’t about putting out fires. It was about installing better and faster sprinklers. We helped many of our customers shift from reactive to proactive defense.
For example, we saw Vilnius Tech prevent 15 cyber-attacks, and Kiloverse move beyond threat firefighting. We watched Omnisend gain visibility into threats and worked with partners like Tailor Made Technologies to secure SMEs. These are just a few highlights from our busy year. But let’s unpack more details.
Making headlines
In 2025, NordStellar became the primary data source for a major investigation by the Independent. A journalist reached out with a simple query: What is actually happening with public sector security in the UK?
The findings were a bit of a wake-up call. Our report revealed that more than 700 government email addresses and passwords had been leaked online. And it wasn’t just a statistic, but a stark reminder that no one is immune to exposure. Not even public administration staff, or maybe especially them. We also cited 9 distinct attempts to sell classified UK military and NATO documents to threat actors, raising genuine concerns about the UK’s national security risks.
But it wasn't about sensationalism; it was about highlighting the scale of the invisible war with cybercriminals. This is what we preach daily: if your data is compromised or on the dark web, you need to know about it before the wrong people do.
Keeping ransomware on the radar
We wish the trend looked different here. Unfortunately, ransomware didn’t slow down in 2025. In fact, Q2 was a blockbuster season for ransomware, but for all the wrong reasons. That’s why, to keep our finger on the pulse, we launched regular ransomware statistics this year. We tracked activity across hundreds of ransomware blogs and dark web forums. The findings were far from optimistic.
Small and medium-sized companies experienced the highest number of attacks, and manufacturing remains the most targeted sector, with 245 recorded cases in Q3 of 2025. North America is the primary hunting ground for hackers, accounting for nearly 50% of all incidents, where cyber gangs like LockBit 3.0 dominate the ransomware arena.
We’ve SOC 2 Type 2 attestation: it’s official
In July, we hit a major milestone: NordStellar became SOC 2 Type 2 compliant. We know trust isn’t given; it’s earned. And SOC 2 Type 2 attestation isn't just a badge for our website footer. It is rigorous, third-party validation that we handle your data with the highest standards of security, availability, and confidentiality. And it means you can rest easy knowing our internal controls are robust.
2025 product highlights
We didn’t just watch threats evolve; we improved our solutions to prevent them more quickly and effectively. Here is a look at the heavy hitters we rolled out this year.
Dark web monitoring: shedding more light on invisible threats
This year, we expanded the capabilities of our dark web monitoring to see further into the corners of the dark web:
Two new big data sources. We added ransomware blogs to provide early warnings of incidents affecting both companies and third-party vendors. We also included dark web marketplaces, where stolen credentials, payment card data, malware, and hacking tools are bought and sold.
Better visual context for dark web threats. Text logs can be abstract and difficult to interpret. Forum posts now include screenshots, offering direct visual evidence of threats as bad actors discuss them.
These two improvements give better insights into how criminals target customers. Knowledge is power, but knowledge of threats is protection.
Brand protection
We know that your brand is your reputation, and we want to ensure no one “borrows” it. That’s why, in 2025, we introduced these new solutions:
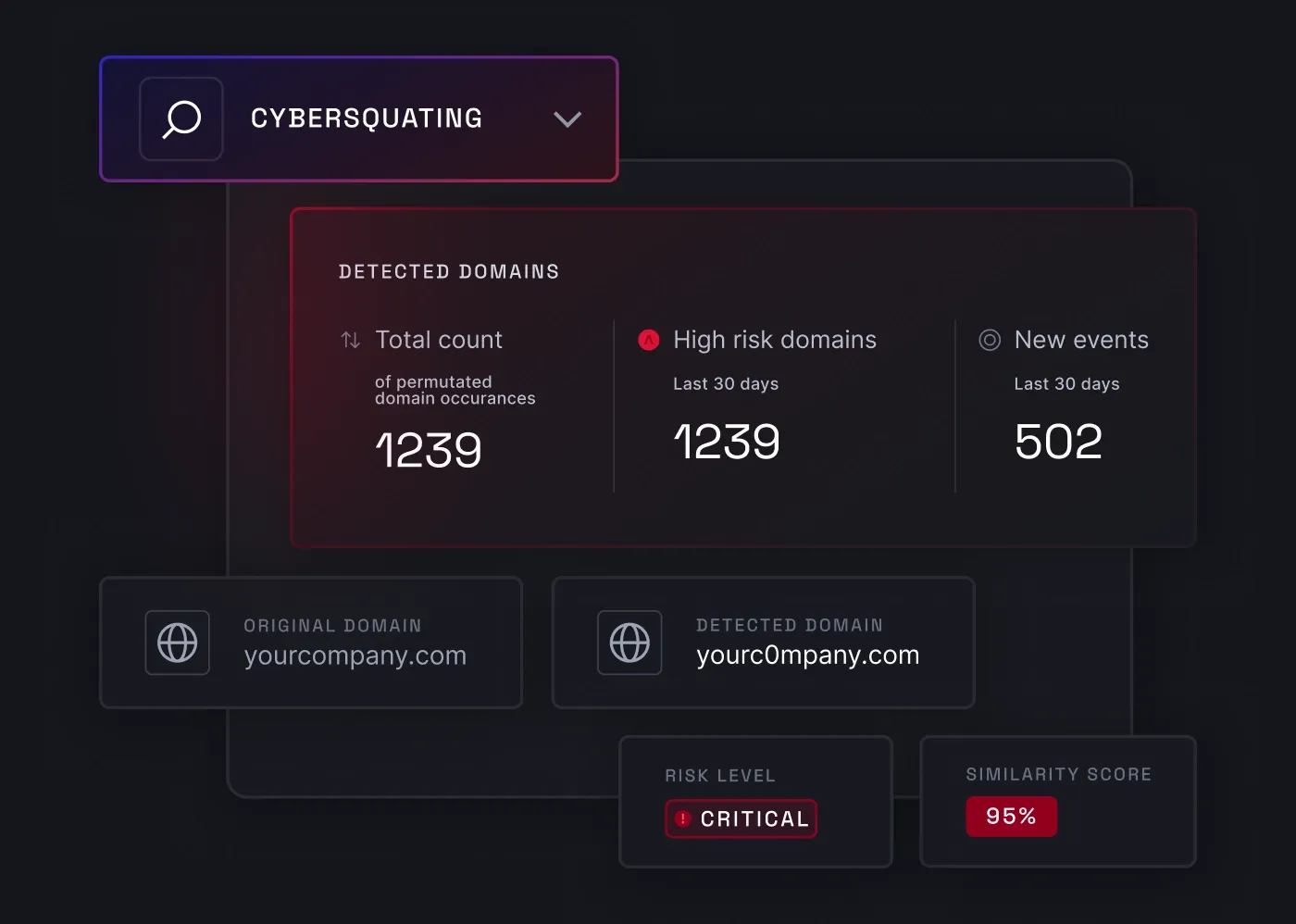
Domain squatting
Cybersquatting detection hunts down malicious domains that impersonate your brand and are later used in phishing and business email compromise attacks. It also gives you clear recommendations on what to do next if your brand has been “stolen”.
Monitoring of social media and app stores
We have also introduced Brand Protection service, which scans social media and app stores for phishing content and malicious applications that impersonate your brand.
Removing fake content
Identifying a threat is the first step. Taking it down is step two. Our takedown services help you remove look-alike domains, impersonating social media accounts, fake mobile apps, typosquatting, and phishing sites that target your brand.
Attack surface management: know your vulnerabilities
We launched Attack Surface Management to give you control over your external infrastructure, including domains, IP addresses, and services. It’s a multi-stage process that spans from identifying weaknesses to constant monitoring. Here is how we ensure your systems are protected:
Identification. You can’t protect what you can’t see. We use automatic asset discovery—with DNS enumeration and web crawling—to map every asset exposed on the internet tied to your organization.
Analysis. We don't just list assets; we vet them. Using passive service fingerprinting, we scan your digital footprint to spot known vulnerabilities that could leave you exposed.
Assessment. Not every alert is a fire drill. We categorize threats by severity and exploitability, helping you prioritize the risks that actually matter.
Remediation. Finally, we help you plug the gaps. With real-time alerts on new vulnerabilities and changes to your attack surface, your team can fix issues before an attacker finds them.
In short, attack surface management reduces cyber risks and allows you to fix vulnerabilities in your external assets.
Related articles

Anastasiya NovikavaSep 30, 20257 min read

Rūta TamošaitytėDec 16, 20256 min read
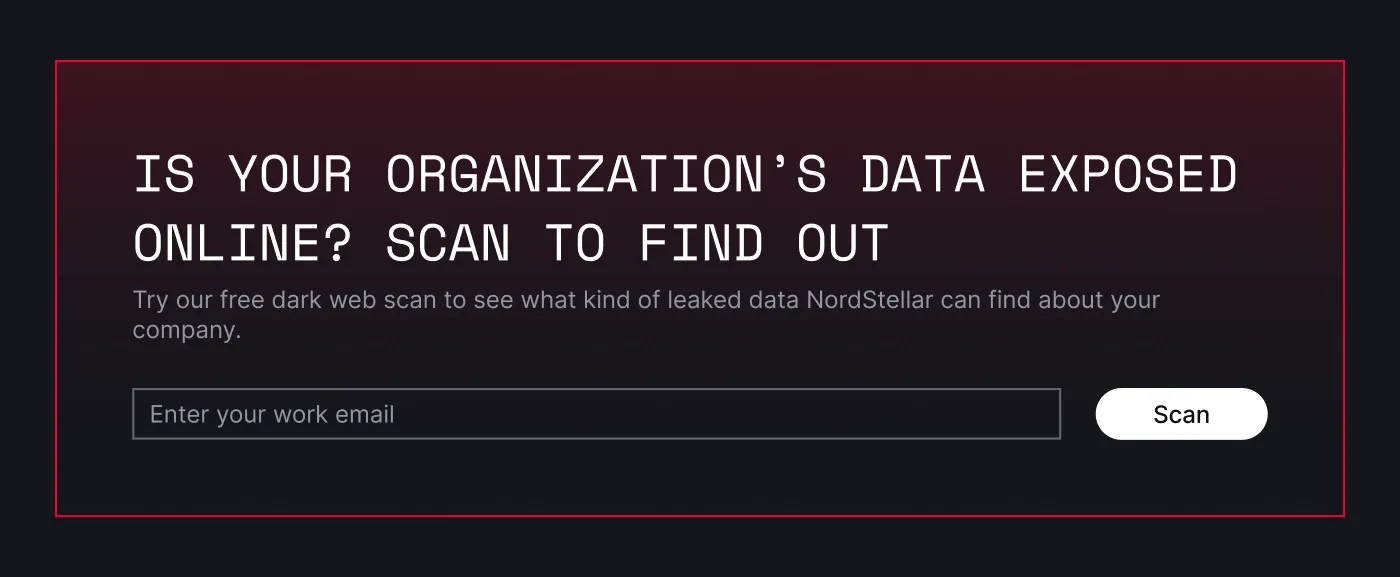
A quick pulse check: dark web scanner
Curious about your exposure? We launched a free online dark web scanner. Anyone can check if their company data has been leaked. It’s a simple, no-strings-attached way to see if your defenses are holding up—try the tool out for yourself.
Core functionality updates
We believe that a tool is only as good as its usability. This year, we have focused on making NordStellar smarter and more user-friendly.
Smarter alerts with identity provider (IDP) integration. To combat alert fatigue, we integrated with identity providers such as Google Workspace, Okta, and Entra ID. This means you’ll only get alerts about leaked credentials relevant to current employees. It cuts the noise so you can focus on real threats.
Improvements to data breach monitoring. We’ve expanded
the malware drawers with new tabs for richer data points. New tabs for FTP, Secrets, Process Lists, RDP, RAC, SSH, VPN, and email clients provide critical context on every malware infection, not just the headlines.
Fuller visibility into malware logs. You can now reveal non-corporate data found in malware logs. How can you view it? Simply turn off the toggle. After you provide consent, all previously blurred non-corporate data will become visible.
Self-managed assets. You can now add, edit, or remove domains, IP addresses, phone numbers, and emails for monitoring purposes.
Granular access controls (RBAC). We introduced role-based access management, allowing you to assign admin, regular, or view-only permissions. It provides better enterprise control over who sees what.
Separate monitoring spaces. You can create distinct monitoring spaces, which is perfect for MSPs, MSSPs, or anyone juggling different sub-organizations.
A brand new look of the NordStellar dashboards. Finally, we gave the platform a facelift. Our UI redesign features cleaner, sharper dashboards that make navigating threat intelligence faster and more intuitive.
Here’s to staying ahead in 2026
We aren't slowing down this year. We have big plans for new features that will continue to tip the scales in your favor.

Joanna Krysińska
Senior Copywriter
Joanna's family has a history in math and engineering, and she loves explaining complicated technical ideas. She helps people understand how hackers think and how to stay ahead of them by concentrating on the human side of cybersecurity.